
Our smartphones know everything about us – who our friends are, where we have been, our financial details, our health information and other intimate details of our lives. But can we trust our phones to keep these our personal information secret? One of the biggest security and privacy challenges of smartphones are the very apps we install on them and use every day. Many applications that we install are free, everything from utilities to games; however, if we are not paying for these apps, how are the developers making money? Many app developers generate revenue by harvesting information from your device and selling this aggregated information to marketers and other organizations. Often times, what these applications collect is disclosed in privacy policies and terms and conditions – yet most of the time they don't. Furthermore, many app developers may incorporate third-party tools and libraries in their apps, which harvest additional information the developers may not be aware of. I am an advisor to a startup in Portland called Privacy Sentry, focused on unveiling the secret behavior of mobile applications. Their first app for Android, called SpyAware Privacy Defender, provides device owners the ability to see what data is being collected from their device, as well as where that information is being sent to. In addition to the app itself, additional tools are deployed to provide a deeper analysis of an applications behavior at the packet level.
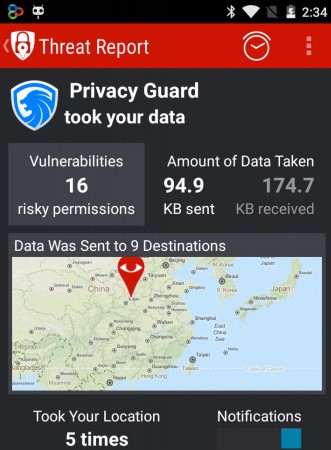
One interesting application that we discovered and monitored with SpyAware was an application called LEO Privacy Guard, which advertises itself as an application that protects your privacy. However, when analyzing the application, we discovered a number of disturbing things. First was the overzealous permissions the application required – everything form app history, identity, contacts, location, SMS, phone history, photos and other media, and even accessing the camera on the device. Although the application may have permission to access sensitive information on the device, it is not exactly a smoking gun, so we analyzed what data was actually being sent outside the device... this was when things got worse.
We discovered that a number of device and personal identifiers were being sent to servers in China and Singapore unencrypted, including the IMEI (International Mobile Station Equipment Identity), IMSI (International Mobile Subscriber Identity), as well as device MAC address along with other identifying information. Additional information is being encrypted and transmitted to these same servers.
The LEO Privacy Guard privacy policy only states that they gather device information, which can be rather vague. Privacy Sentry asked the company behind the application for clarification with regards to what they are doing with the information they are collecting, but they did not respond to inquiries. The fact that data is being stored on servers in China and Singapore is problematic for a number of reasons – the data then falls under the jurisdiction of laws of those countries, if law enforcement or a government agency were to make a request for this information, they would be required to hand it over. None of the information with regards to what specific data was being collected or where it is being sent to was disclosed in the privacy policy. This raises more questions and increases the risks to security and privacy, more than the app helps protect it. You can read the full Privacy Sentry report here. The LEO Privacy Guard application is just one example of information being harvested and sent to servers both inside and outside the country. One of the biggest challenges with securing mobile devices is getting visibility into what information is being collected and shared. It is important for consumers and businesses alike to be conscious of what applications are being deployed to their devices. A game that you download and install on your phone for your child to play with could be much more than that, and if that same device is used for banking or business, it could put you and your organization at unnecessary risk. As we also saw with the recent XCodeGhost vulnerability and exploit, the supply chain of app development can also put you at risk, so it is advisable to only install applications from trusted vendors and trusted application stores and solely select those apps you need. Also, be sure you review the permissions of the applications you install (for Android) and actually pay attention to the privacy policies and terms of use for apps.

