
A joint investigatory effort neutralized more than 850,000 unique infections of Retadup, a worm known for targeting Windows machines in Latin America. In March 2019, Avast came across an interesting cryptomining payload that arrived with a advanced stealthy process hollowing implementation. The security firm decided to look into what means of distribution the cryptocurrency miner was using. This analysis led researchers to Retadup. Spotted by Avast in previous campaigns, Retadup is a worm that tends to achieve persistence on victims' computers. It then leverages those infections to expand its reach even further and to install additional malware payloads on the compromised host. Most of the time, this payload was a cryptominer, though researchers did spot the worm dropping STOP ransomware and the Arkei password stealer. Avast's analysis revealed something interesting about Retadup, particularly its command-and-control (C&C) infrastructure. As it explained in its research:
...[W]e found that while it is very prevalent, its C&C communication protocol is quite simple. We identified a design flaw in the C&C protocol that would have allowed us to remove the malware from its victims’ computers had we taken over its C&C server. This made it possible to put an end to Retadup and protect everyone from it, not just Avast users....
Realizing that Retadup's C&C infrastructure was primarily based in France, Avast shared its findings with the Cybercrime Fighting Center (C3N) of the French National Gendarmerie at the end of March. It also proposed a disinfection plan in which it would take over the C&C server and abuse the design flaw to neutralize infections. The Gendarmerie liked the idea, so it opened a case on the worm, presented the disinfection scenario to a prosecutor and shared parts of a snapshot of the Retadup C&C server disk with Avast. These efforts helped the security firm learn more about the malware in the meantime, including the fact that those responsible for the worm had accidentally infected themselves with the Neshta fileinfector. In July, the Gendarmerie received the green light to proceed, so it replaced the C&C server with another server that used the design flaw to disinfect Retadup-infected machines. It also contacted the FBI to assist with taking down some infrastructure based in the United States. Through these efforts, the malware authors lost complete control of their bots on 8 July. Those bots communicated a great deal of information to the disinfection server. Through that activity, Avast learned that its scenario had helped disinfect over 850,000 unique infections of Retadup, with the vast majority of these located in Latin America. The security firm also learned that more than half of affected machines had been running Windows 7 at the time of infection.
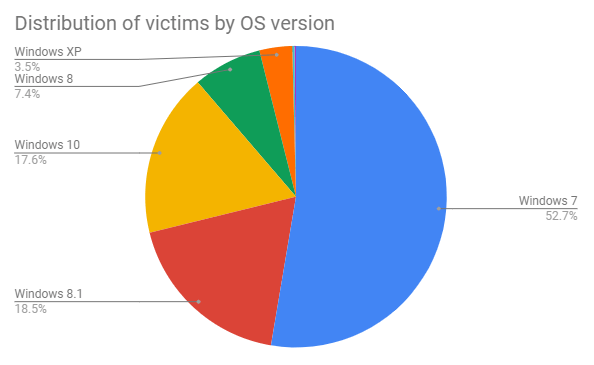
A pie chart illustrating the distribution of Retadup’s victims by operating system version. (Source: Avast) This investigation underscores the need for organizations to defend their users against malware like Retadup, Neshta and other threats. They can do so using a solution that looks out for known malware signatures and signs of zero-day threats. Learn how Tripwire can help.

