
A new remote access trojan (RAT) known as Kedi phones home and transmits a victim's stolen data to attackers using Gmail. The malware relies on spear-phishing, one of the most common types of phishing attacks, for distribution. These attack emails spread a 32-bit Mono/.Net Windows executable, written in C#, that masquerades as a Citrix tool. It then changes its disguise to Adobe file after it installs itself in the Adobe folder of %Appdata%.
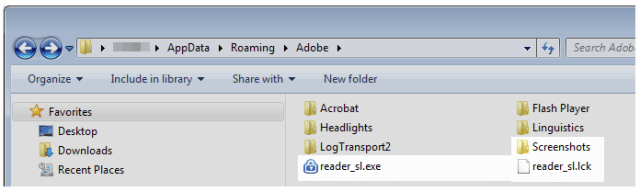
Kedi's Adobe disguise. (Source: Naked Security) Kedi comes with some configuration data that it protects using XOR-based encryption. This data contains instructions for the usual functions of a RAT, such as grabbing screenshots and logging keystrokes. The malware then takes the information it stole from a victim and sends it back to its attackers. It can do so via DNS and HTTPS. But what makes Kedi unique is its ability to phone home using Gmail. Naked Security author Bill Brenner elaborates on this technique:
"Using Gmail to receive instructions from its C2, Kedi navigates to the inbox, finds the last unread message, grabs content from message body and parses commands from this content. To send information back to command and control, base64 encodes the message data, replies to the received message, adds encoded message data and sends its message."
No doubt malware developers programmed Kedi's Gmail functionality in an attempt to prevent security researchers from detecting the threat. It's reasonable to assume that other bad actors will go to these lengths to preserve their malware, as well. With that said, users and businesses should work to prevent a malware infection. First, they should install an anti-virus solution on all workstations and keep that solution updated. Second, organizations should conduct ongoing phishing awareness training with their employees. Lastly, businesses should develop a vulnerability management program that's capable of quickly addressing known security issues. To do a better job of keeping up with the thousands of vulnerabilities reported each day, click here.

