
A South Korean web hosting company has paid more than one million dollars in ransom after suffering an Erebus ransomware infection. The ransomware, which has been around since September 2016 and reemerged in February 2017, struck NAYANA on 10 June. Those responsible for the attack demanded 550 Bitcoins or approximately US$1.62 million. The web hosting company negotiated a smaller amount of 397.6 Bitcoins, or around $1.01 million, to be paid in three installments. By 17 June, NAYANA had already made two payments.
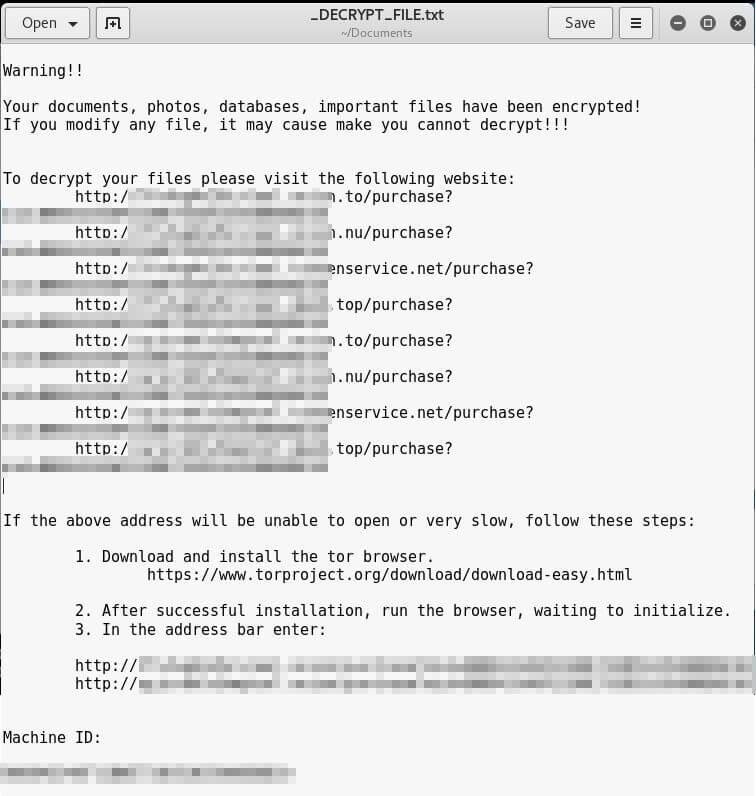
Erebus has a multilingual ransom note (English shown above). (Source: Trend Micro) It's currently unknown how Erebus arrived onto NAYANA's servers. Given the fact that the company's website runs Linux kernel 2.6.24.2, a version which was compiled in 2008, the ransomware might have acquired root access by exploiting a Linux-based vulnerability. Alternatively, it might have exploited security flaws in the website's outdated Apache and PHP versions or even leveraged a local exploit. Regardless of how it struck the company, the ransomware didn't waste any time in encrypting NAYANA's files using a multi-layer encryption routine. Trend Micro's Ziv Chang, Gilbert Sison, and Jeanne Jocson elaborate on this scheme:
"The file is first scrambled with RC4 encryption in 500kB blocks with randomly generated keys. The RC4 key is then encoded with AES encryption algorithm, which is stored in the file. The AES key is again encrypted using RSA-2048 algorithm that is also stored in the file. "While each encrypted file has its RC4 and AES keys, the RSA-2048 public key is shared. These RSA-2048 keys are generated locally, but the private key is encrypted using AES encryption and another randomly generated key."
Erebus is capable of encrypting 433 different file types, though it's also known to go after web servers. Once it encrypted NAYANA's assets, the attackers revealed their unprecedentedly high ransom demands. On 18 June, NAYANA began its work to recover its 153 Linux servers affected by the ransomware. Those servers store the websites, databases, and multimedia files of approximately 3,400 businesses. Some of the servers recovered in the second patch thus far have experienced database errors. When NAYANA has recovered all its infected servers in the first and second batches, it intends to make the third installment. Users and businesses alike can protect against ransomware like Erebus by backing up their regular data on an ongoing basis, patching their software of known security vulnerabilities, and not clicking on suspicious links and email attachments.

