
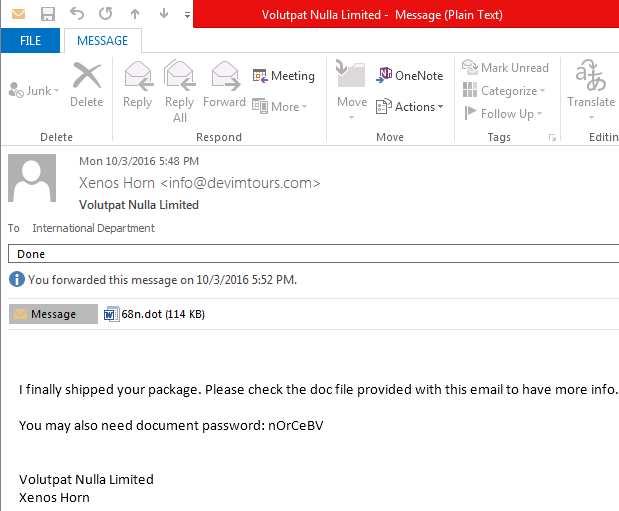
A type of macro malware campaign has incorporated password protection into its attack emails in order to serve up ransomware. The campaign begins with an email that comes with an attached document bearing the .dot extension. It's password-protected, and the only way a recipient can open it is to enter in the password provided by the sender in the email's main body.
Source: McAfee Labs
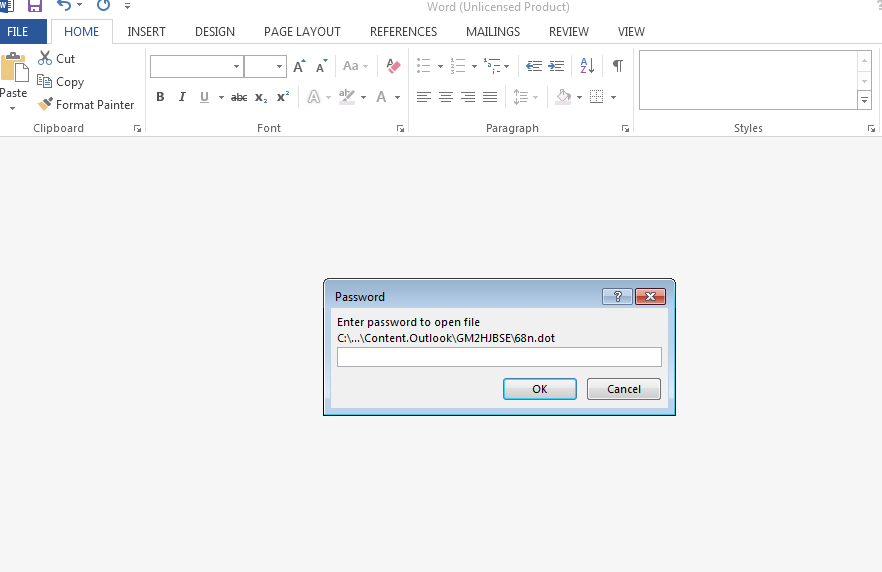
Source: McAfee Labs It's a clever trick, as password protection makes it more difficult for an anti-virus solution to extract and analyze the attached document for malware. After the recipient enters in the password, the document behaves like most other macro-based malware. Diwakar Dinkar and Satish Chimakurthi of McAfee Labs explain:
"Once the user provides the password to open the document, it prompts the user to 'enable editing and enable content to read content.' If a user clicks 'enable content,' macros will be enabled and will drop a malicious VBScript with a random name in %appdata%."
That particular VBScript comes with high levels of obfuscation. When it is deobfuscated, it downloads the encrypted payload, which is decrypted by a XOR operation. But like most advanced malware, the payload doesn't execute immediately. Instead this campaign makes use of one of the most common evasive techniques in malware: timing-based evasion. The McAfee researchers elaborate on that point:
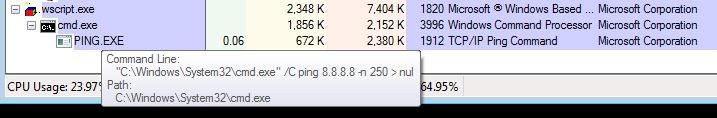
"Malware authors uses different techniques to delay the execution of any suspicious functionality for a certain time. Generally sandbox systems monitor execution for a limited time, and in the absence of malicious activity classify a program as legitimate. Attackers uses techniques such as onset delay, stalling code, and extended sleep calls to delay the execution in sandbox environments. This variant delays execution by running cmd.exe with the parameter 'ping 8.8.8.8 -n 250 > nul,' which pings the Google DNS server 250 times and ignores the results."
Source: McAfee Labs Execution of the payload results in the campaign dropping Cerber ransomware onto the victim's computer. To protect against this malware campaign, users should exercise caution around suspicious email attachments from unknown senders and maintain an up-to-date anti-virus solution on their computers.

