
A security researcher has developed a device called MagSpoof that can emulate any magnetic stripe or credit card wirelessly. Hacker Samy Kamkar first came up with the idea shortly after he lost his American Express card last August. At that time, he noticed a pattern in his replacement card's last four digits when compared to those of his previous AmEx cards. He subsequently developed an algorithm that aligned with his observations, a formula which according to PCWorld has since accurately predicted 40 original cards and replacement cards shared with him by his friends for his research.
“One hundred percent of them followed my predictions,” Kamkar said in a phone interview Tuesday. He just needs the old card number and the expiration date to complete the calculation.
To share his findings with the wider security community, Kamkar has developed MagSpoof, a device which can use his algorithm to predict any replacement card's number based on a canceled card's digits.
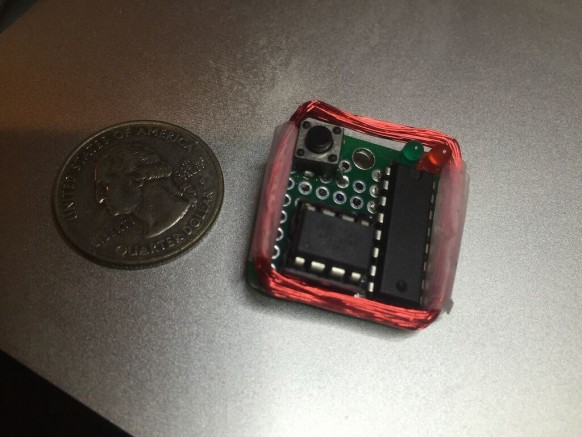
The $10 MagSpoof device that implements Samy Kamkar’s American Express card number prediction attack (Source: WIRED). MagSpoof works by using data stored on magnetic stripes, reports Softpedia. Any magnetic field contained in the stripe of a payment card can be stored on the device. Someone can then reproduce that particular magnetic field at a higher intensity near any point-of-sale (PoS) payment reader and complete a transaction wirelessly without physically having to swipe the card. A video of MagSpoof in action is available here. Since having announced the creation of MagSpoof, an AmEx representative contacted WIRED and explained that two protections, an extra security code embedded in the magnetic stripe of credit cards and chip-and-pin (or EMV) technology, can allegedly negate the device's capabilities.
“Simply knowing a card number wouldn’t allow a fraudster to complete a purchase face-to-face because a card product would need to dipped at many of the stores with EMV chip portals, or swiped. In addition, the security code embedded in the card product would need to be verified. For both EMV chip and magnetic stripe cards, the security code changes with the card number and is impossible to predict,” writes AmEx spokesperson Ashley Tufts.
Tufts's explanation notwithstanding, all PoS terminals are not created the same. For instance, Kamkar was able to complete transactions using two of his own guessed cards at two different restaurants. EMV technology is not air-tight, either.
"I discovered that if I can modify the service code, or create a new card with a different magstripe with the same data but just flip that bit, I can essentially disable that requirement for the chip," the hacker said, as related by CSO Online.
He subsequently went on to do just that and make a purchase with a card that should have completed a chip-and-pin transaction. It is clear that MagSpoof can be compromised if left in the wrong hands. As a result, Kamkar has designed the device so that users cannot store magnetic stripes that they are not legally authorized to possess. In other words, they must have/own the magnetic stripes in order to study them using his device. MagSpoof costs $10 to make and requires no more than a micro-controller, motor-driver, wire, a resistor, switch, LED, and a battery. Instructions for assembly can be downloaded off of GitHub here.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

