
Digital security common sense says you should never plug an unauthorized device like an unknown Universal Serial Bus (USB) into your computer. Of course, logic doesn't always reign supreme when it comes to using a computer. We saw this on display at Black Hat USA 2016 when Google's anti-abuse research team shared an experiment for which its researchers dropped 300 USB sticks on a college campus. Passersby picked up 98 percent of the USBs, and they plugged in and accessed files on 45 percent of the devices out of curiosity, a desire to help a lost device's owner, and even an unfounded trust in these computing devices. Ultimately, USBs don't deserve our trust. It's possible for attackers to craft a malicious device disguised as a normal thumb drive that can log users' keystrokes. Technically, these USB hubs (both external and internal to a computer) should prevent an attacker from leveraging such an instrument to steal data from adjacent USB-connected devices. But that's not the case in practice. As it turns out, many USB hubs don't sufficiently secure the communication lines between USB ports and the computer, an oversight which attackers can exploit to steal sensitive data.
It's Called "Channel-to-Channel Crosstalk Leakage"
For their experiment, researchers Yuval Yarom, Yang Su, and Damith Ranasinghe of the University of Adelaide along with Daniel Genkin of the University of Pennsylvania and Maryland tested 50 computers and external USB hubs. They found that 90 percent of the devices they examined can potentially leak information to compromised devices. This vulnerability boils down to several elements. First, many buses, or devices which transmit information to different components of a computer system, don't use encryption and authentication to secure their communication channels. Instead, they depend on a unicast network model to route their messages from the sender to the receiver, something which is known as "upstream traffic." As the Yarom and his colleagues explain in their research paper (PDF):
"Each hub has one upstream port and up to seven downstream ports. Downstream traffic is broadcasted to all of the devices in the tree. However, upstream data is only sent along the (single) path from the transmitting peripheral device to the host. In particular, hubs which are not located on the path between the transmitting peripheral and the host should not be able to observe the peripheral’s upstream USB traffic."
But that begged the question: could common communication buses be vulnerable to off-path attacks? Could actors in some way monitor an adjacent USB port from other ports on the same hub? To determine if this "channel-to-channel crosstalk leakage" phenomenon was possible, the researchers connected a USB input keyboard to a hub. They then used an oscilloscope to monitor the data sent from the device to the computer. All the while, they measured the leakage on a different USB port of the same hub. This leakage manifested itself on the D+ or D- differential data signal line relative to the GND line on one of the hub’s other downstream ports. By using signal processing techniques, the researchers were able to decode the information contained in the data line leakage.
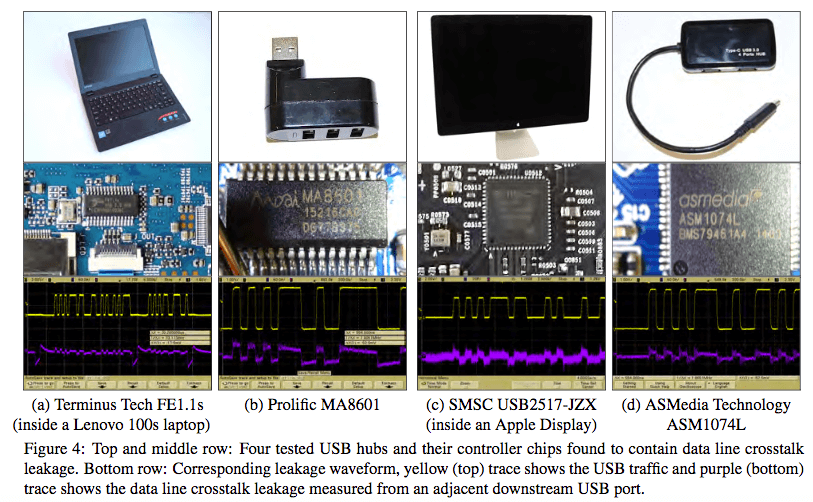
USB Snooping Made Easy: Crosstalk Leakage Attacks on USB Hubs, page 5 Yarom and his colleagues replicated this technique to extract keystrokes from USB keyboards, credit card data from a USB card reader, and microphone signals from a USB headset. They then took their efforts one step further by constructing a "spy probe" hidden inside a USB lamp and connecting it to a bus slot on a Microsoft Surface Pro. Here's what they discovered:
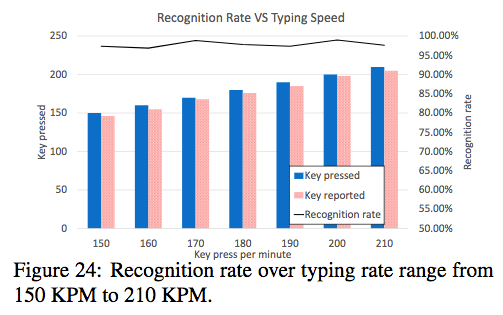
"We measured the spy probe’s key recognition rate under various typing speeds. Using a digital metronome as a speed reference, we pressed a random key on every metronome pulse. We evaluated the spy probe’s ability to operate at various typing speeds. As can be seen in Figure 24, the spy probe achieves 97% accuracy rate for typing speeds from 150 KPM (Keypress Per Minute) to 210 KPM. Notice that average adult typing speed is between 36 and 45 words per minutes, equivalent to 200 KPM."
USB Snooping Made Easy: Crosstalk Leakage Attacks on USB Hubs, page 15 Their spy probe implementation used commercial off-the-shelf components not optimized for capturing USB traffic. This means the device took up a lot of space and used a lot of energy. Designing dedicated hardware to do the job could make these kinds of attacks more inconspicuous in the wild.
Concluding Recommendations
To prevent crosstalk leakage and bad actors from capturing it, USB hub manufacturers can optically decouple bus data lines and use a 5V supply for each downstream support. That kind of solution can be expensive. For a cheaper alternative, a LC low pass filter and low dropout regulator could do the trick. The researchers also recommend that the USB protocol adds end-to-end encryption or encryption with a session key to help guarantee the confidentiality and integrity of messages. Those countermeasures, however, overlook the most salient point of the experiment. As Dr. Yarom told the University of Adelaide in a statement:
"The main take-home message is that people should not connect anything to USB unless they can fully trust it. For users, it usually means not to connect to other people's devices. For organizations that require more security, the whole supply chain should be validated to ensure that the devices are secure."
For best practices on how to protect your organization's supply chain, click here. You can also hear Dr. Yarom and his colleagues present additional findings from their experiment on 18 August 2017 at the USENIX Security Symposium held in Vancouver, Canada.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

