
A security firm has identified MalumPoS, a new type of point-of-sale (PoS) malware that is targeting businesses in the hospitality, food and beverage, and retail industries. According to a blog post published by global security software company Trend Micro, the authors of MalumPoS designed the malware to collect data from PoS systems running Oracle® MICROS®, a payment system commonly used by businesses in the affected industries. Trend Micro estimates that over 330,000 businesses located primarily in the United States are currently running Oracle® MICROS®.
"In general, PoS RAM scrapers like MalumPoS are designed to scrape off credit card data from an infected systems’ RAM," explains Jay Yaneza, a threat analyst for Trend Micro. "Every time the magnetic stripe of a credit card is swiped, the malware can steal stored data such as the cardholder’s name and account number. This data can then be exfiltrated and used to physically clone credit cards or, in some cases, commit fraudulent transactions like online purchases.
The security firm has also noted several other features of MalumPoS. These are:
- Configurable: The malware's design allows threat actors to add additional PoS systems, processes, and areas to be scraped, which potentially places a wider number of retailers at risk.
- NVIDIA Disguise: Upon successful installation, MalumPoS disguises itself as a display driver, which is stylized as "Display Driv3r," produced by NVIDIA, a visual computing and computer graphics company. This technique is meant to make the malware appear harmless to users.
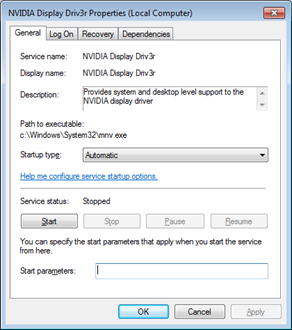
- Other Targets: In addition to Oracle® MICROS®, the malware also targets Oracle Forms, Shift4 systems, and those accessed via Internet Explorer, with a large chunk of those affected originating in the United States.
- Selective Credit Card Scanning: MalumPoS selectively scans for PoS data and information relating to the following credit cards: Visa, MasterCard, American Express, Discover, and Diner’s Club.
To read more about MalumPoS, which joins the ranks of other point-of-sale malware including Backoff and LusyPoS, please click here. You can also learn more about how PoS and other types of malware, such as Rombertik, evade detection here.

