
The gang responsible for the Maze ransomware family conducted an attack in which they distributed their malware payload inside of a virtual machine (VM). Sophos’ Managed Threat Response (MTR) observed the technique in action while investigating an attack that occurred back in July 2020. In that incident, the attackers packaged the ransomware payload inside of a Windows .msi installer file that was more than 700MB in size and distributed it onto the VM’s virtual hard drive.
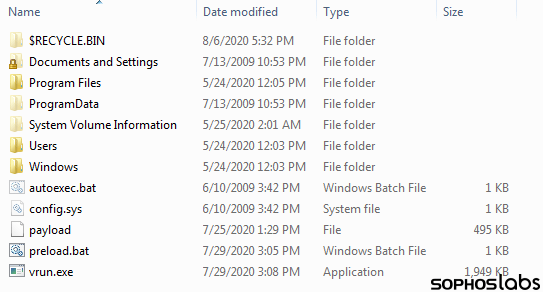
A look inside the Maze-delivered VM, with the 495KB ransomware payload clearly visible. (Source: Sophos MTR) An investigation into the attack revealed that the malicious actors had been present on the targeted organization's network for at least six days prior to distributing their ransomware payload. During that period, they had built lists of internal IP addresses, used one of the organization's domain controller servers and exfiltrated information to their data leaks site. This dwell time could explain the existence of certain configurations of the Maze-delivered VM. As quoted by Sophos' MTR in its research:
The virtual machine was, apparently, configured in advance by someone who knew something about the victim’s network, because its configuration file (“micro.xml”) maps two drive letters that are used as shared network drives in this particular organization, presumably so it can encrypt the files on those shares as well as on the local machine. It also creates a folder in C:\SDRSMLINK\ and shares this folder with the rest of the network.
The campaign described above wasn't the first instance in which attackers have delivered ransomware inside a virtual machine. Back in May 2020, Sophos' MTR spotted the Ragnar Locker crypto-malware family pull the same trick. The virtual machine in that attack ran Windows XP as opposed to the Windows 7 instance on the VM containing Maze. Furthermore, the latter VM was larger in size in order to support additional functionality. This technique highlights the need for organizations to defend themselves against a ransomware infection. They can do so by working to prevent a crypto-malware attack in the first place.

