
Hackers have been found exploiting a freshly-uncovered vulnerability in Microsoft's software to install malware on business computers. According to security researchers, since last month a Russia-linked hacking group known as APT28 have been using a Microsoft protocol called Dynamic Data Exchange (DDE) to run malicious code through a poisoned Word document. Targeted attacks linked to APT28 (also sometimes known as the "Fancy Bear" hacking gang) have taken advantage of the recent New York City terror incident in an attempt to plant spyware via the method. DDE, as its name suggests, allows messages and data to be shared between applications. Last month, it was discovered that it was possible to launch attacks exploiting DDE through Word documents, Excel spreadsheets, and Outlook even when macros have not been enabled. Now, of course, attacks exploiting Microsoft Office documents are nothing new - and most of us who work in the security industry know to be wary of enabling macros when opening files because of the potential for malicious code to be executed.
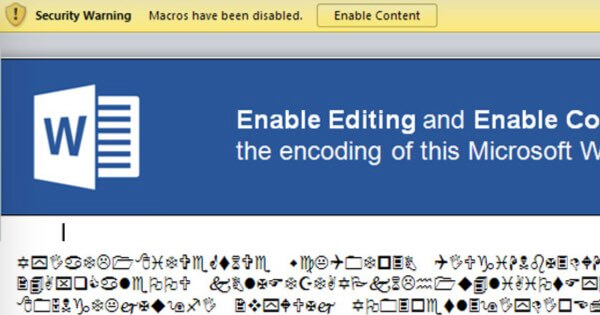
But with this DDE attack, you see no prompt to enable macros. This lack of a warning allows attackers to side-step an obstacle which has often acted as a final safety net for their intended victims. Instead, the most you might notice that's unusual is a pop-up message box asking if you want to update the document with data from linked files.
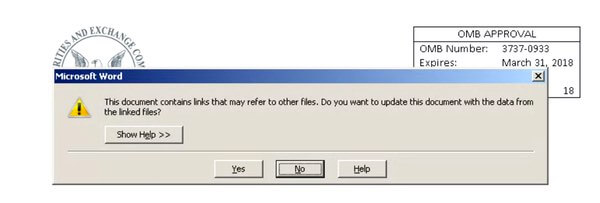
"This document contains links that may refer to other files. Do you want to update the document with the data from the linked files?"
Microsoft, in a security advisory released yesterday, has described how the technique could be used in a typical email attack:
In an email attack scenario, an attacker could leverage the DDE protocol by sending a specially crafted file to the user and then convincing the user to open the file, typically by way of an enticement in an email. The attacker would have to convince the user to disable Protected Mode and click through one or more additional prompts. As email attachments are a primary method an attacker could use to spread malware, Microsoft strongly recommends that customers exercise caution when opening suspicious file attachments.
So, after decades of email-based malware attacks, we're back to some tried-and-trusted advice: be very wary of opening unsolicited email attachments. And as Microsoft considers the functionality of DDE to be a feature rather than a bug, it seems unlikely that it will be patching the technique anytime soon. According to Microsoft's advisory, concerned Microsoft Office users are advised to check their DDE-related security settings and disable the automatic update of data from linked fields to mitigate the threat. Currently, this mitigation may require some tinkering in the Registry and so should be done cautiously. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc-

