
Malware as a business model rests on two core tenets—the first is innovation. Malware authors are constantly innovating tools and techniques that allow their software to slip past network defenses, to brute force their way past weak authentication credentials, and to escalate local privileges—all in an attempt to counter the work of security personnel. Not surprisingly, malicious programs commonly change from year to year. 2015 was no exception. The second tenet is money. Bad actors need money to sustain their criminal activities, and they are willing to chase a payday through a variety of means. Some turn to ransomware, while others turn to lucrative targets, such as point-of-sale (POS) terminals. Case in point, in the third quarter of 2015 alone, researchers at Trend Micro observed a 66 percent increase in the volume of POS malware attacks. Retail is a common target for these types of offenses, but it doesn't stand alone in the crosshairs.
"While the traditional retail establishments have been popular targets, the threat extends to any company that runs point-of-sale," said Tim Erlin, Director, Security and IT Risk Strategist at Tripwire, in a blog post. "Most recently, we’ve seen a spate of identified compromises at hotels, like Hyatt, Starwood and Hilton."
The prospect of compromising a POS terminal is an enticing one. If done correctly, a computer criminal can make off with thousands, if not millions, of unsuspecting credit card holders' payment details. With that in mind, it is no surprise the security industry has witnessed significant innovation in POS malware over the last few years. A few samples in particular have set the bar for POS malware development. One of those is ModPOS. First detected in 2012, ModPOS is a modular POS malware platform that comes equipped with a number of loadable plugins, including a keylogger, a POS RAM scraper and other functionalities. The malicious framework is known to have targeted U.S. retailers back in 2014, though it is likely criminals used ModPOS to attack additional victims that have not yet been identified. In an effort to understand the threat ModPOS poses to organizations that run point-of-sale, not to mention the evolution of POS malware more generally, we turn to Lastline, an advanced malware protection firm which has analyzed this malicious framework. Only by understanding how ModPOS executes on victims' machines can we hope to protect organizations from sophisticated POS malware threats.
The ModPOS Infection Cycle
ModPOS initiates infection using a dropper component that contains an encrypted portable executable (PE) file. Once the PE has been decrypted, the malware selects a random driver-service that exists on the system and reuses it as its own 32-bit driver. The malicious framework then launches that driver into the Windows kernel. The driver loaded into the kernel is obfuscated with several layers of packing. To unpack the driver, the malware initiates three stages in sequence. In Stage 1, the malware loads up an unpacker containing several basic mathematical operations such as add and xor. Using a series of functions, the unpacker generates random numbers that are passed as arguments to the simple mathematical operations. But those arguments are stored on a separate stack, which means the content in this phase returns to its original form once the main unpacking loop completes. Lastline reasons malware authors developed this process to throw off human analysts.
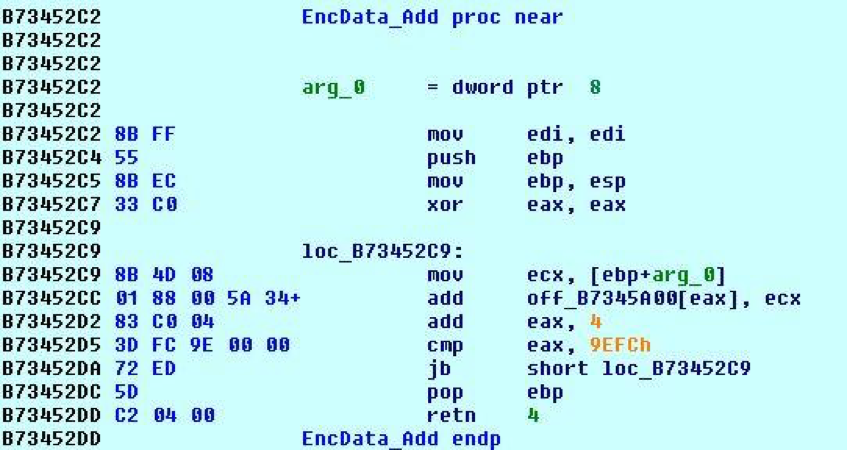
The real decryption function at that point begins and uses a XOR key to decrypt the remaining code before jumping to the Stage 2, where a small grouping of code allocates memory, arranges code sections, relocates variables and jumps, and builds import tables. Stage 2 eventually jumps to the Stage 3, which launches the decrypted ModPOS functionality. Once decrypted, the malicious framework wastes no time in assembling some system information into a Globally Unique Identifier (GUID), which is used as the name for creating a Mutex thread. That thread enables the malware to bridge the gap between the Windows kernel and Windows user-mode.
"The thread injects code into a trusted user-mode process csrss.exe (windows subsystem process)," Lastline details. "To this end, it enumerates the processes running on the system using NtQuerySystemInformation (with parameter SystemProcessInformation(0x5)), checks the name of each process, and, once found, opens the target process. The code retrieves the process handle and allocates 0x1000 Bytes inside the target process using NtAllocateVirtualMemory. Then it combines two location-independent shellcode buffers embedded inside the kernel module and writes them into the target process's memory through NtWriteVirtualMemory (location 89837A07). This shellcode serves as entry point to running in user-mode."
If the code is successfully into csrss.exe, the malware can exploit that entry point to set up a communication channel between the kernel- and user-mode components, allowing ModPOS to communicate with a command and control (C&C) server and load up a number of plugins, such as a keylogger and POS RAM scraper. At that point, the attacker can do whatever they want with the kernel or any other process on the infected system.
Conclusion
ModPOS is a sophisticated POS malware framework that uses multiple unpacking phases to load up its final payload and inject malicious code into into user- and kernel-mode processes. Given the evolution of POS malware threats, it is important that organizations running point-of-sale continually monitor their POS terminals and other endpoints for suspicious behavior like those displayed by ModPOS. To learn more about POS Threat Protection and how Tripwire Enterprise can help secure POS terminals, please click here. Title image courtesy of ShutterStock
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

