
NameCheap has said it intends to notify customers of a misconfiguration issue that allowed customers to create subdomains for any hosted account. Richard Kirkendall, CEO for the ICANN-accredited registrar, said on Twitter that the company is currently conducting an audit and plans on "contacting any affected customers directly" following the discovery of a misconfiguration issue on its nameservers. He went on to say that NameCheap has implemented a fix and that it's a "high priority" for the enterprise to inform customers of what happened. The issue first came to light on 5 February when NameCheap customer Kirk McElhearn received an email from Google warning him that it appeared someone had hacked a few of his subdomains.
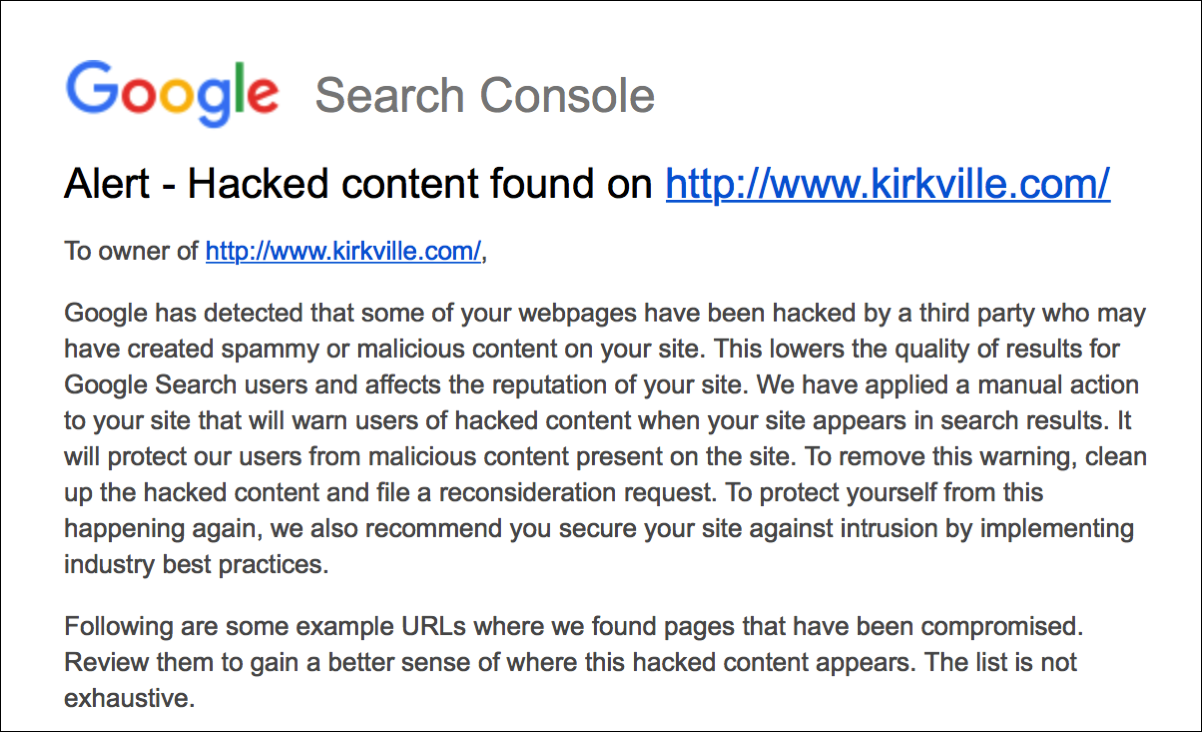
A screenshot of the email received by McElhearn from Google. (Source: kirkville.com) Concerned, McElhearn checked Cpanel to see if anyone had hacked into his account. He didn't find any new subdomains, including the ones Google told him about in its email. After changing his password for safe measure, McElhearn contacted NameCheap. The registrar looked into the matter and told McElhearn it had detected a misconfiguration issue on one of its nameservers. Essentially, another customer of NameCheap had abused the weakness to add the subdomains for kirkville.com to their own hosting account. That's not all the flaw allowed, however. As McElhearn explains in a blog post:
Even though I have SSL on my website – meaning that it uses https instead of http in its URL – and any incoming traffic to http://www.kirkville.com is automatically redirected to the https version of the site, the sub-domains were parsed by name servers before they reached my site’s server, so they weren’t redirected.
From those unprotected pages, unauthorized actors could capitalize on the prominence of another customer's website like McElhearn's to distribute spam and malware. In an email sent to The State of Security, Kirkendall says the issue stemmed from NameCheap's use of a custom implementation of DNS for its shared hosting systems that he says are separate from its core domain business. The company uses shared hosting to point all domains to the same DNS cluster servers. While serving benefits for NameCheap, Kirkendall explains the setup created the issue reported by McElhearn:
Any client on our Shared Hosting was able to add a subdomain of the domain pointed to DNS cluster to it’s[sic] cPanel and manage it from there. To do so one just needed to find out that the domain was pointed to our DNS cluster.
Kirkendall confirmed that the number of affected domains was "less than 100" and that NameCheap rolled out a fix on the same day of discovery. Even so, McElhearn told The Register he's still waiting for an official acknowledgment of the issue from the company:
They certainly haven't contacted me about it, outside of the tweet which isn't what you'd call official. And Teeny tiny is not a useful term.
If you are a NameCheap customer, you should check to make sure no one has added any unexpected web pages to your account. It's also a good idea to confirm you've protected your account with a secure password and two-factor authentication (2FA).
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

