
Netflix has released a new tool called Sleepy Puppy that helps security researchers capture, manage, and track cross-site scripting (XSS) propagation over extended periods of time. Two application security researchers for the movie-streaming service, Scott Behrens (@helloarbit) and Patrick Kelley (@monkeysecurity), created the Sleepy Puppy tool to address a critical weakness in traditional XSS testing.
"Often when testing for client side injections (HTML/JS/etc.) security engineers are looking for where the injection occurs within the application they are testing only," observe the researchers in a description of Sleepy Puppy on GitHub. "While this provides ample coverage for the application in scope, there is a possibility that the code engineers are injecting may be reflected back in a completely separate application."
Behrens and Kelley go on to explain that their tool addresses this shortcoming via the use of inter-application XSS testing by enabling JavaScript payloads that callback to the Sleepy Puppy application. This allows for the tracking of payloads across different users and applications as well as over extended periods of time. At the heart of Sleepy Puppy is the 'PuppyScript,' a customizable JavaScript that collects information on the client and application whenever the payload executes. The default configuration of the PuppyScript generates useful metadata including the URL, user-agent, referer headers, cookies, and other sources of data.
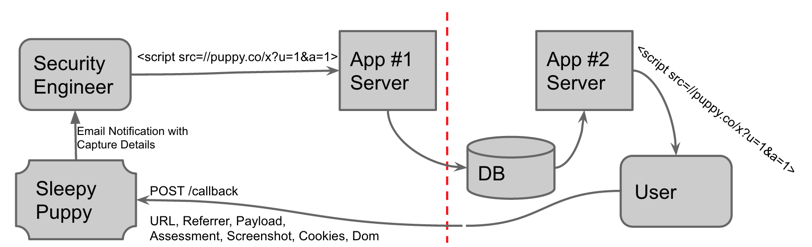
Source: The Neflix Tech Blog PuppyScripts and the information they produce can help security researchers track XSS propagation across different applications and in turn mitigate vulnerabilities more quickly. As Behrens and Kelley note in a post on The Netflix Tech Blog, more advanced users can chain PuppyScripts together and use them to capture arbitrary data from any input source.
“It’s a phenomenal concept,” said Daniel Miessler, Practice Principal at HP’s security organization “That’s huge, especially when you could be getting detonation events days, weeks, or months after the attack was sent. It’s a really cool feature that should take front and center in the explanation of the tool."As noted by The Register, Sleepy Puppy works with Docker and can be plugged into Burp Suite or Zap using the API. The platform follows a series of other security tools released by Netflix, including the Fully Integrated Defense Operation (FIDO) incident response tool that was made available earlier this year.

