
Attackers are leveraging a new malware campaign – dubbed Gooligan – to target Android devices and compromise users’ Google accounts, researchers unveiled on Thursday. To date, the attackers have gained access to more than 1.3 million Google accounts with an additional 13,000 devices being breached each day, according to cybersecurity firm Check Point. The infection begins when a user downloads and installs a Gooligan-infected app on a vulnerable Android device, which includes devices running OS versions 4 (Ice Cream Sandwich, Jelly Bean, and KitKat) and 5 (Lollipop). Check Point researchers found dozens of infected apps on third-party app stores, but notes Android users could also download the apps directly by clicking malicious links in phishing attack messages.
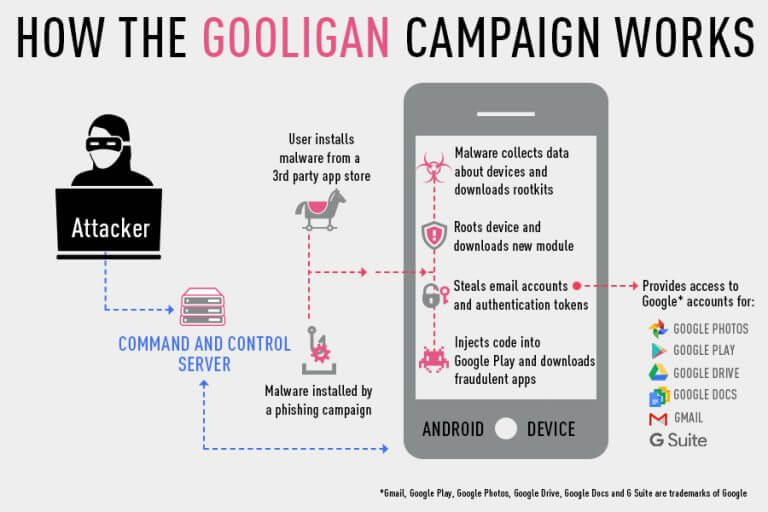
Source: Check Point Once an infected app is installed, it sends data about the device to the campaign’s Command and Control (C&C) server. Gooligan then downloads a rootkit from the C&C server that leverages several Android 4 and 5 exploits, including VROOT (CVE-2013-6282) and Towelroot (CVE-2014-3153), explained Check Point researchers.
“These exploits still plague many devices today because security patches that fix them may not be available for some versions of Android, or the patches were never installed by the user,” said Check Point researchers.
If rooting is successful, the attacker has full control of the device and can execute privileged commands remotely. Next, a module is downloaded onto the device that injects code into running Google Play or Google Mobile Services to avoid detection. Researchers found the module allows Gooligan to steal a user’s Google email account and authentication token information, which can be used to access all the Google services related to the user, such as Google Play; Gmail; Google Docs; Google Drive; and Google Photos. The module also allows attackers to install apps from Google Play and rate them to raise their reputation and potentially increase downloads, as well as install adware to generate them revenue.
“Our research team was able to identify several instances of this activity by cross-referencing data from breached devices with Google Play app reviews. This is another reminder of why users shouldn’t rely on ratings alone to decide whether to trust an app,” warned Check Point.
For more information on Gooligan and a list of infected apps, see Check Point’s blog post here.

