It’s been weeks since Apple released its new operating systems, iOS 10 and mac OS Sierra. The new updates brought security patches, features and upgrades. Siri assistant has finally arrived on desktops, and an exciting universal clipboard allows you to select photos from an iPhone device and paste them directly on the desktop. However, with these changes, Apple has decided to leave old loose ends which could affect the security of its products. One of the changes is Apple’s departure from the PPTP encryption protocol in its built-in VPN. The reason for such a step is because of a number of security vulnerabilities found in this security protocol. Apple has publicly announced the departure from PPTP and encouraged the use of other security protocols, such as L2TP/IPsec, IKEv2/IPsec, Cisco IPsec, and SSL VPN. https://twitter.com/itxjamie/status/776102836874649600 PPTP (Point-To-Point Tunneling protocol) – which is considered weak encryption protocol – is also perceived as the fast communication protocol that offers better speed than other protocols. It leaves many PPTP VPN users frustrated as they are hand-tied to using third-party client applications in order to use PPTP VPN connection.
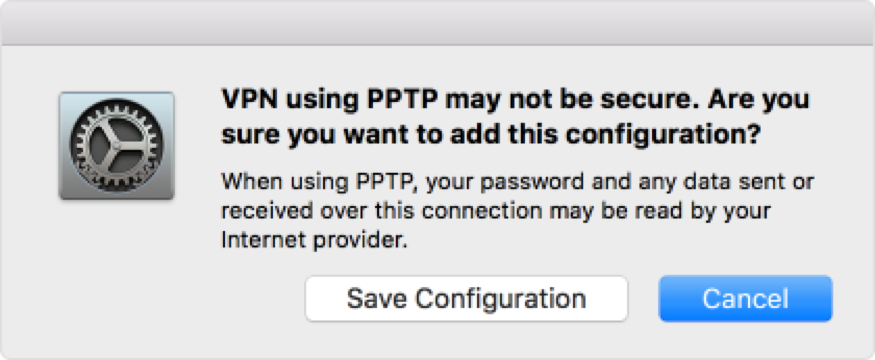
Microsoft also mentioned and advised its users to use alternative protocols in a blog post:
“iOS 10 no longer supports the PPTP VPN protocol. If you have deployed any custom profiles in Intune that use the PPTP protocol, iOS 10 will remove the PPTP connections from any VPN profiles when a user upgrades their device. Intune supports alternatives to PPTP from the IT Admin console.”
Apple has always been taken the security a top priority, which could be seen by the recent question and answers session attended by the company’s CEO, Tim Cook. There, he described encryption as "one of the things that make the public safe.” He further said:
"We feel we have a responsibility to protect our customers." "We believe the only way to protect both your privacy and safety from a cyber attack is to encrypt. We throw all of ourselves into this and are very much standing on principle in this."
While departing from a PPTP connection may seem a frustration for some and a cumbersome process for organizations to update their protocols, it is also a step forward to ensure the security of those who are using VPNs for Mac and iOS devices.
Understanding the said protocols
L2TP/IPsec L2TP (Layer 2 Tunneling Protocol) is a tunneling protocol used in VPN connection. It does not have its own encryption algorithm but relies on the encryption suite of IPsec, which authenticates and encrypts each IP packet of a communication taking place. This protocol offers a balance of speed and security as compared to PPTP. However, L2TP is not compatible with NAT, port-forwarding becomes a necessity in some cases, and if the IP of the IPsec server changes, all clients needs to be informed of the change. IKEv2/IPsec (VPN Reconnect) IKEv2 (Internet Key Exchange version 2) is a tunneling protocol that uses IPsec encryption protocol over UDP port 500. Jointly developed by Microsoft and Cisco, also dubbed as “VPN reconnect,” IKEv2 provides resilience to the VPN connection. When the VPN client moves from one wireless hotspot to other, it automatically disconnects all internet activities when a VPN connection is lost and re-establishes the connection upon successful connectivity. Mobile users specifically can benefit from such a protocol. However, it is not supported on many platforms as it is fairly new to VPN services. In many cases, they just offer a “kill switch option” as a feature in their VPN client. Cisco IPsec Cisco IPsec is a tunneling protocol typically used in the network infrastructure of organizations to secure the communications between Cisco routers and VPN clients. Cisco IPsec applies without affecting the individual workstations, which typically occurs in IPsec. The benefits of Cisco IPsec technology over typical IPsec protocol is that it applies to all the traffic cross the perimeter of the company’s network. There is no need to change the software on the server system. It supports remote access of offsite workers. SSL VPN SSL (Secure Socket Layer) VPN works similar to traditional VPN. The SSL VPN technology has grown in popularity as compared to its counterpart IPsec and allows users to connect remotely to their organizations, obtaining access to the restricted network. It adds advanced encryption technology of SSL and transmits data through an encrypted tunnel to a VPN concentrator, which gives the appearance of a user as that of the local network regardless of the actual location of the user.
Choosing Between Tunneling Protocols
When choosing between L2TP, Cisco IPsec, SSL VPN, and IKEv2/IPsec VPN solutions, consider the following:
- PPTP, unlike other protocols, does not require PKI (Public Key Infrastructure). PPTP VPN provides data confidentiality (captured packets cannot be decoded without encryption key). However, PPTP VPN does not offer data integrity (data was not modified in transit) or data origin authentication (data sent by authorized user).
- L2TP supports either preshared key or computer certificates as the authentication method for IPSec encryption protocol. Computer Certificate Authentication is the recommended method, which requires the PKI to issue computer certificates at each communication step between VPN server and VPN client. L2TP offers data confidentiality, data authentication, and data integrity. Unlike other protocols, L2TP facilitates machine authentication at IPsec layer and authentication at user level at PPP layer.
- Cisco IPsec is suitable for organizations to secure network infrastructure.
- IKEv2 support is limited to systems running Windows 7 and Windows Server 2008 R2. IKEv2 supports latest IPsec encryption ciphers. It supports mobility (MOBIKE), which handles the VPN connectivity issues, and it is a good choice for users. It provides data integrity, confidentiality, and authentication.
- SSL VPN supports the latest technology of SSL as compared to its counterpart IPsec. It is widely used in OpenVPN client. OpenVPN is an open-source software application that applies VPN techniques to create secure connections. It utilizes TLS/SSL for key exchange. It is NAT- and firewall-friendly. Though it offers strong security but it slows down the speed as compared to its counterparts.
Apple has removed PPTP support for its built-in VPN, but it doesn’t limit you from installing third-party VPN client software. However, even with third-party VPN client, it is suggested not to use a PPTP VPN connection (as it has become outdated and vulnerable to cyber attacks) when other strong security protocols are available.

About the Author: Peter Buttler is a professional security expert and lecturer. He serves as a digital content editor for different security organizations. While writing he likes to emphasize on recent security trends and some other technology stuff. You can follow him on Twitter. Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.

