
Researchers identified a large-scale cryptocurrency miner infection in which a new malware family called "Norman" took part. The Varonis Security Research team made the discovery while investigating a cryptominer infection at a mid-sized company. Here's what they found through this effort:
Almost every server and workstation was infected with malware. Most were generic variants of cryptominers. Some were password dumping tools, some were hidden PHP shells, and some had been present for several years.
Varonis didn't have a difficult time identifying the hosts affected by the attack. That's because they all used DuckDNS, a dynamic DNS service which users can use to create custom domain names. In this particular case, the infected hosts leveraged DuckDNS for their command-and-control (C&C) infrastructure. This process ultimately led Varonis to uncover Norman. The sample identified by the data security software firm functioned as an XMRig-based cryptominer. It also concealed itself as "svchost.exe." Even so, the malware stood out for its abilities to evade detection. For instance, the malware's DLL arrived with triple obfuscation courtesy of the Agile obfuscator. Later on in the infection chain, the malware terminated its mining component whenever a user opened Task Manager so as to trick them into thinking that nothing's wrong. It also injected an obfuscated miner version to Notepad, Explorer, svchost or wuapp depending on the infection's execution path. As of this writing, it's unclear which actor created Norman. Varonis did determine that the actor likely spoke French because they used a French version of WinRAR to create an SFX file used in the campaign. In order to learn more about the malware, the firm also modified the threat with code so that it'll be notified of new commands received by Norman going forward.
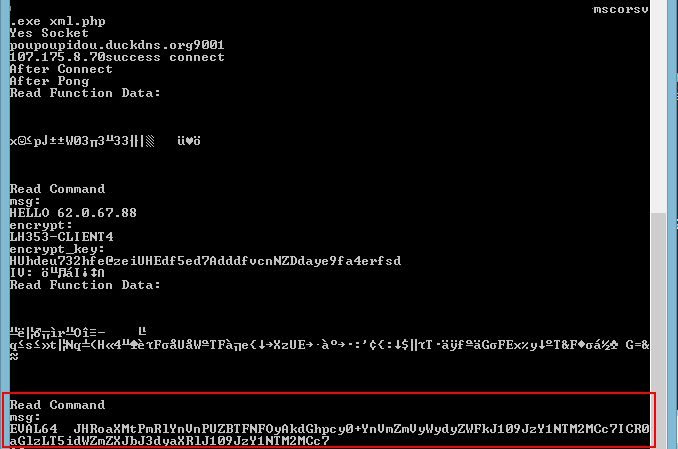
A screenshot of Norman malware with the code added by Varonis outlined in red. (Source: Varonis) This campaign highlights the need for organizations to defend themselves against digital threats like cryptomining malware. Towards that end, organizations should consider investing in a solution that provides continuous visibility over system changes in their network. This tool should also leverage real-time analysis to help spot malware that attempt to cover their tracks. Learn how Tripwire can help in this regard.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

