
A security firm has uncovered a new strain of ransomware that is seeking to extort money from websites powered by the Linux operating system. On Thursday, Russian antivirus company Dr. Web added the malware, known as "Linux.Encoder.1," to its virus database. A description of the ransomware was created the following day:
"Once launched with administrator privileges, the Trojan loads into the memory of its process files containing cybercriminals' demands," explains the company in post on the malware. "As an argument, the Trojan receives the path to the file containing a public RSA key. Once the files are read, the malicious program starts as a daemon and deletes its original files."
Dr. Web goes on to map out the infection process of Linux.Encoder.1. The ransomware first encrypts all files found in the directories /var/lib/mysql, /etc/nginx, and others. It then moves on to the home directories, followed by the directory from which it was launched as well as the root directory. Next, it targets specific files, first those whose names start with a specific string, including "public_html" and "www", and then finally those with the file extensions ".docx", ".jpg", ".exe", and many others. Upon completion of the infection process, the ransomware displays a message to the victim demanding one Bitcoin ($300-$400 USD) in ransom, which is less than the usual 2-4 Bitcoins demanded by other ransomware authors, as Softpedia reports. Below is an image of the ransom message displayed on an infected machine:
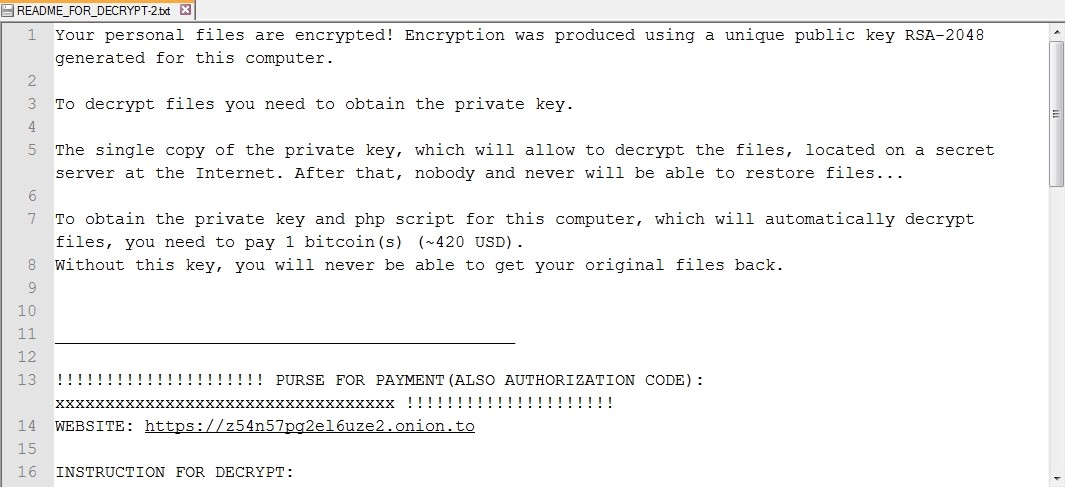
Ransom note shown to infected victims (Source: Softpedia) Professional web designer Daniel Macadar saw this exact same message on Wednesday when the ransomware targeted one of the servers he uses. As noted in a blog post by Brian Krebs, Macadar was behind on his backups, so like the FBI recently recommended to do in certain situations, he paid the ransom after setting up a Bitcoin account. Within three hours, the server was fully decrypted, but not all was well:
“There’s a decryption script that puts the data back, but somehow it ate some characters in a few files, adding like a comma or an extra space or something to the files,” he said.
To help secure his website against future attacks, Macadar enlisted the help of an independent security service, which found an unpatched hole in the website's Magento shopping cart service. Acknowledging this example, Dr. Web recommends that sysadmins and web developers maintain regular backups while they work to develop a decryption tool for Linux.Encoder.1. To learn more about how you can protect yourself against ransomware, please click here.

