
In the past, Osiris was mostly known as an Egyptian god of the afterlife, the underworld, and the dead. Now it's known as the latest extension of the Locky ransomware menace, as its creators decided to switch from a Norse mythology theme to an Egyptian one.
.osiris Locky Gets Better at Avoiding Detection
No user wants to see the .osiris file extension appended to their files. Unfortunately, ransomware as sophisticated as Locky tends to find its way into users’ computers quite easily, as evident by its constantly increasing infection rates. Furthermore, Locky’s code has been improved once again to avoid detection. Not surprisingly, the ransomware is distributed via a spam campaign delivering blank emails or such with one single line them, as discovered by researchers. Usually the one-liner emails urge users to open the attached files. The email attachments have unusual extensions, such as .342, .343, .552, or .xls, .tdb, .zk. Here is an example of the latest spam campaign spreading the .osiris iteration of Locky:
From: “Marina” Subject: Emailing: _0828817_36073220 Your message is ready to be sent with the following file or link attachments: _0828817_36073220 Attachment: _0828817_36073220.xls
Such attachments typically contain a Microsoft Word file that prompts the potential victim to enable macros. Once executed, the targeted computer becomes infected with Locky. As a result, all the victim’s files are encrypted, and a ransom note is displayed on the desktop. The note with the payment instructions is saved as a file dubbed OSIRIS-([a-z0-9])\.htm. The symbols within the brackets are randomized numbers and letters.
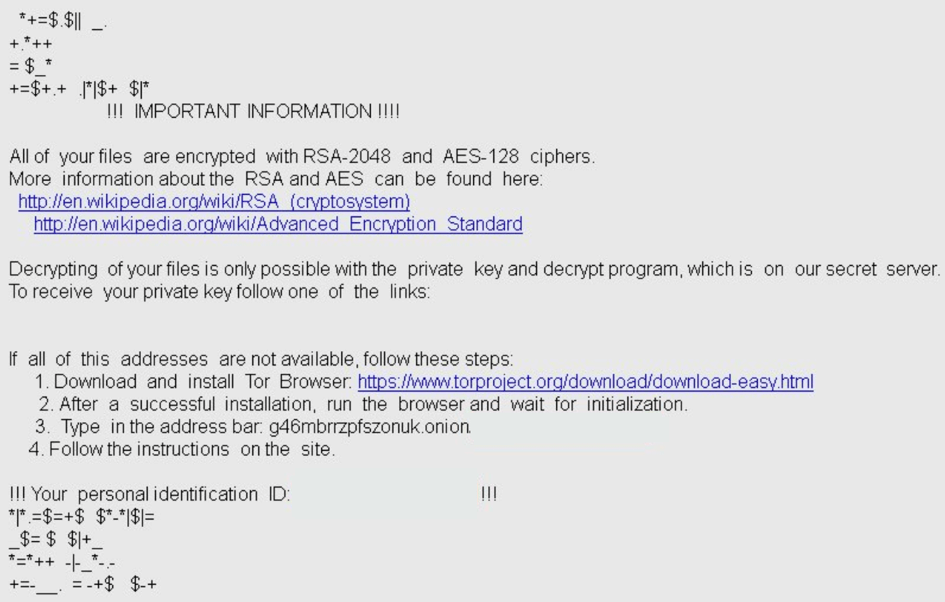
Next, Locky provides a link to a network domain hidden within the TOR browser service. The domain looks exactly like its .thor iteration.
Why .osiris Locky Victims Shouldn’t Pay the Ransom
Victims of previous Locky campaigns have reported that paying the ransom to cybercriminals didn’t help with recovering their files. Victims should neither pay the ransom nor should they attempt any communication with cybercriminals. The more money crooks receive, the more money they have to further develop their malicious, file-encrypting operations. Unfortunately, the continuous sophistication of Locky only proves that cybercriminals are getting better at what they do. For now, there is no decrypter to help victims of the crypto menace, and most likely there will never be. Locky uses a combination of RSA-2048 and AES-128 – two very strong encryption algorithms. Victims could still try restoring their files with data recovery software and should start backing up their data from now on. In the meantime, we all should pray that whoever is behind Locky will soon end up behind bars.

About the Author: Milena Dimitrova is an inspired writer for SensorsTechForum.com who enjoys ‘Mr. Robot’ and fears ‘1984’. Focused on user privacy and malicious software, she strongly believes that passwords should be changed more often than opinions. If common sense makes no sense, she will be there to take notes. Those notes may later turn into articles! Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.

