
Back in February, Tripwire first unveiled its 2016 Breach Detection Survey. The study evaluated the confidence and efficacy with which IT professionals in the United States could implement seven key security controls: PCI DSS, SOX, NERC CIP, MAS TRM, NIST 800-53, CIS 20 Critical Controls, and IRS 1075. Together, those controls recommend accurate hardware inventory, accurate software inventory, continuous configuration management and hardening, comprehensive vulnerability management, patch management, log management, and identity and access management as parts of an ongoing endpoint security strategy.
The results of the survey revealed that IT professionals were generally overconfident in their ability to detect a breach. As I wrote back in February, 60 percent of the study's 763 respondents said they were unsure how long it took for automated tools and vulnerability scanning systems to generate alerts. The majority of those who did have an idea answered it would take only minutes or hours, which disagrees with the findings of both Mandiant's M-Trends 2015 Report and Verizon's 2016 Data Breach Investigations Report. The preponderance of over-assuredness among IT professionals holds steady across across each industry. To illustrate that fact, Tripwire has broken down its survey by sectors. I'll start with finance.
Overconfidence Among Financial IT Professionals
Overall, it would seem financial respondents are just as overconfident as the survey's general pool of IT professionals. Let's take a closer look. 87 percent of financial IT pros said they could remove an unauthorized device from the corporate network within minutes or hours. However, when asked about their ability to detect new assets, three-quarters of IT professionals in the financial sector said they could automatically discover at most 80 percent of hardware assets, and just over a third (37 percent) said their automated tools could discover critical details about unauthorized configuration changes to network devices.
"The majority of respondents aren't discovering all of the assets on their network automatically, but also indicate it takes only minutes or hours to discover new devices on the network," said Tim Erlin, director of IT security and risk strategy at Tripwire. "Either they have an overabundance of staff manually watching network traffic, or there's a gap that's open to attackers."
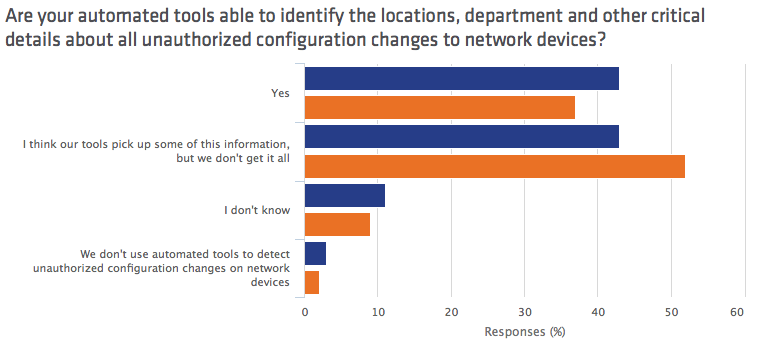
That gap comes in two forms: ignorance and a narrow focus on compliance. Regarding the former, our survey demonstrated that 80-90 percent of financial IT professionals believe it will take just a few hours for vulnerability scans to detect configuration changes and issue an alert. However, more than half (59 percent) of all security personnel don't know how long this detection and alert process actually takes. It would seem many IT staff members working in the finance industry are also following a "check the box" compliance model that leaves additional gaps in the network. Here are some important facts to consider:
- Of those vulnerabilities that were found, 45 percent of them were not fixed within a month.
- 29 percent of respondents do not detect every attempt non-privileged users make to access sensitive files, and about the same proportion (33 percent) do not log to a central system.
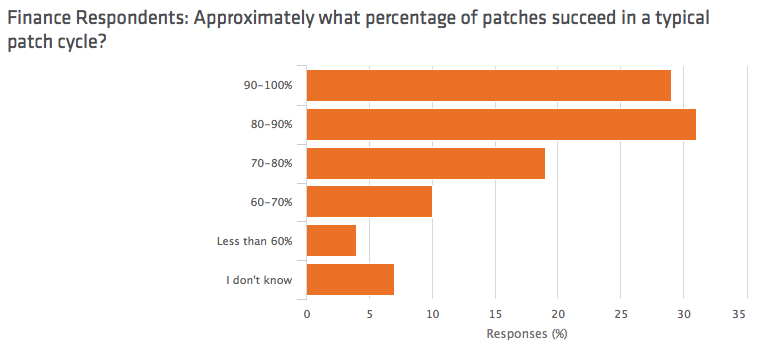
- 40 percent of financial IT professionals said that fewer than 80 percent of patches succeed in a typical patch cycle.
Conclusion
Ignorance and a narrow focus on compliance both stem from too many unknowns. To help address this challenge, Tripwire's senior security research engineer Travis Smith recommends that IT professionals everywhere--not just in the financial sector--invest some effort in proactively identifying what is currently installed on the network.
"The path to a mature security deployment is through visibility because you cannot protect what you cannot see. Understanding what you have and how you can potentially be compromised will allow the security team to focus on where attackers are likely to strike. The cost of being proactive is always less than the cost of being reactive. That is why it’s important to follow best practices outlined by various security controls."
For more information on Tripwire's breach detection survey, please click here. You can view the survey's findings with respect to finance here. Title image courtesy of ShutterStock
