
The Philadelphia ransomware enables attackers to offer "mercy" to their victims by choosing to decrypt their files for free. Attackers are likely distributing Philadelphia, which is a new version of Stampado, via the use of phishing emails disguised as payment notices from Brazil's Ministério da Fazenda or the Ministry of Finance.

Source: Bleeping Computer Philadelphia isn't like other ransomware, however. Its maintenance depends on "bridges," a feature upon which Philadelphia's author expounded at length to an interested buyer. Fortunately, a user of Bleeping Computer managed to capture part of the conversation on the AlphaBay dark web marketplace:
"Bridges are the way victims and attacker enters in touch in a distributed network. It's simply a PHP script that uses itself as database (no MySQL or whatever needed, just PHP). Bridges store the clients keys, verifies payments and provide the victims informations to the headquarters safely. And they can be hosted on nearly any server: even hacked servers, shared hosting (free hosting works but it is not recommended as they can delete your account if it's not a fully functional website), dedicated or VPS (recommended for bigger attacks, although the requests are small and are only done a few times). As the bitcoin payment verification is done on the server side, by the bridge, there is no way to spoof it on the victim machine. Also, the distributed bridges network will grant a better anonimity."
To infect a user, someone who purchases a license to Philadelphia for 400 USD must install PHP scripts for the Bridges on their attack websites. At the same time, they need to install Philadelphia Headquarters onto their machine. That control panel allows them to communicate with each Bridge, which gathers information about each victim and stores the encryption key. Philadelphia Headquarters also comes with a "Give Mercy" button, which allows attackers to decrypt a specified user's files for free.
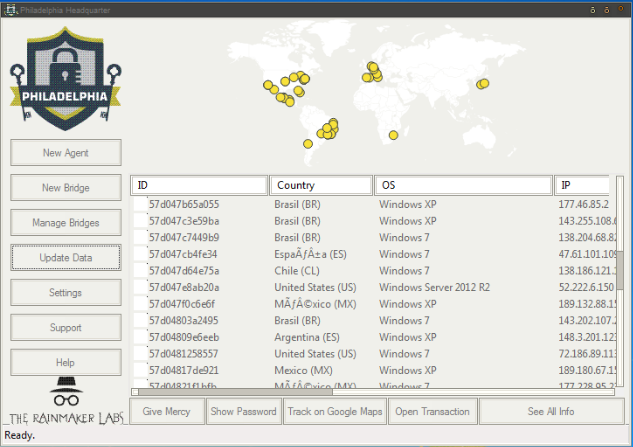
Source: Bleeping Computer Sounds pretty impressive, huh? Well, there's a problem with Philadelphia's implementation of the Bridges system. As computer security expert Lawrence Abrams explains:
"Unless these bridges are stored on anonymous networks like TOR, they will most likely be discovered and taken down fairly quickly. As the addresses to these bridges are hard coded into the ransomware, once the bridge is disabled, a victim no longer has the ability to pay the ransom or decrypt their files. For this implementation to really work, an attacker would need to setup bridges using Tor, which increases the complexity of the setup."
Like other crypto-ransomware currently in circulation, Philadelphia targets removable drives and encrypts files based upon a list of approved file types before it loads up its ransom message:
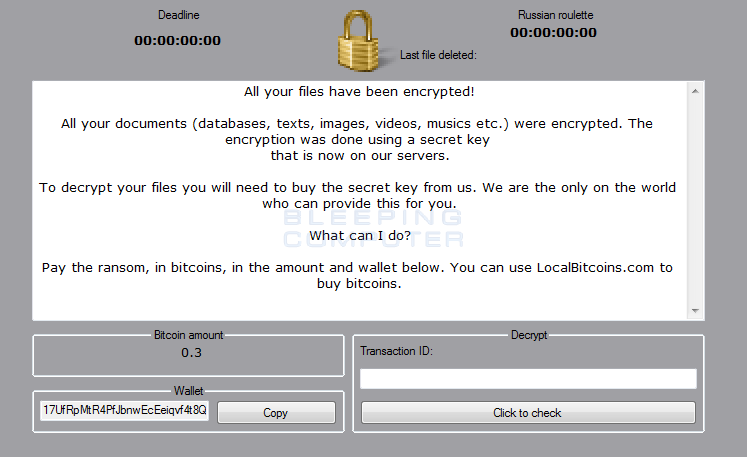
Source: Bleeping Computer Even so, the ransomware claims it "innovates" over other crypto-malware samples, such as by auto-detecting when a victim submits a Bitcoin payment. Victims affected by Philadelphia currently do not have a way to recover their files for free. But as security researcher Fabian Wosar is confident the ransomware can be decrypted, it's likely only a matter of time before a decryption tool comes out. While we wait, users should back up their critical information regularly and follow other ransomware prevention strategies. They can also learn more about ransomware in general here.

