
Phishers hacked an extension for Google Chrome and abused their ill-gotten access to push out spam to unsuspecting users. The security incident befell Copyfish, a type of software which allows users to extract text from images, video, and/or PDF documents. Only the program's Chrome extension suffered as a result of the attack. It's Firefox counterpart was not affected.
Copyfish's developer, a company known known as a9t9 software, says it's traced the trouble back to a phishing attack that occurred on 28 July:
"A team member received an email from Google' saying that we need to update our Chrome extension (Copyfish) otherwise it would be removed from the store. “Click here to read more details” the email said. The click opened the 'Google' password dialog, and the unlucky team member entered the password for our developer account. This looked all legit to the team member, so we did not notice the pishing attack as such at this point. Pishing for Chrome extensions was simply not on our radar screen. [sic]"
The firm doesn't have a screenshot of the fake password page but explains it appeared "only once," which a9t9 software feels is a "clear giveaway" in hindsight. It did take a screenshot of the initial phishing email and its reply, however.
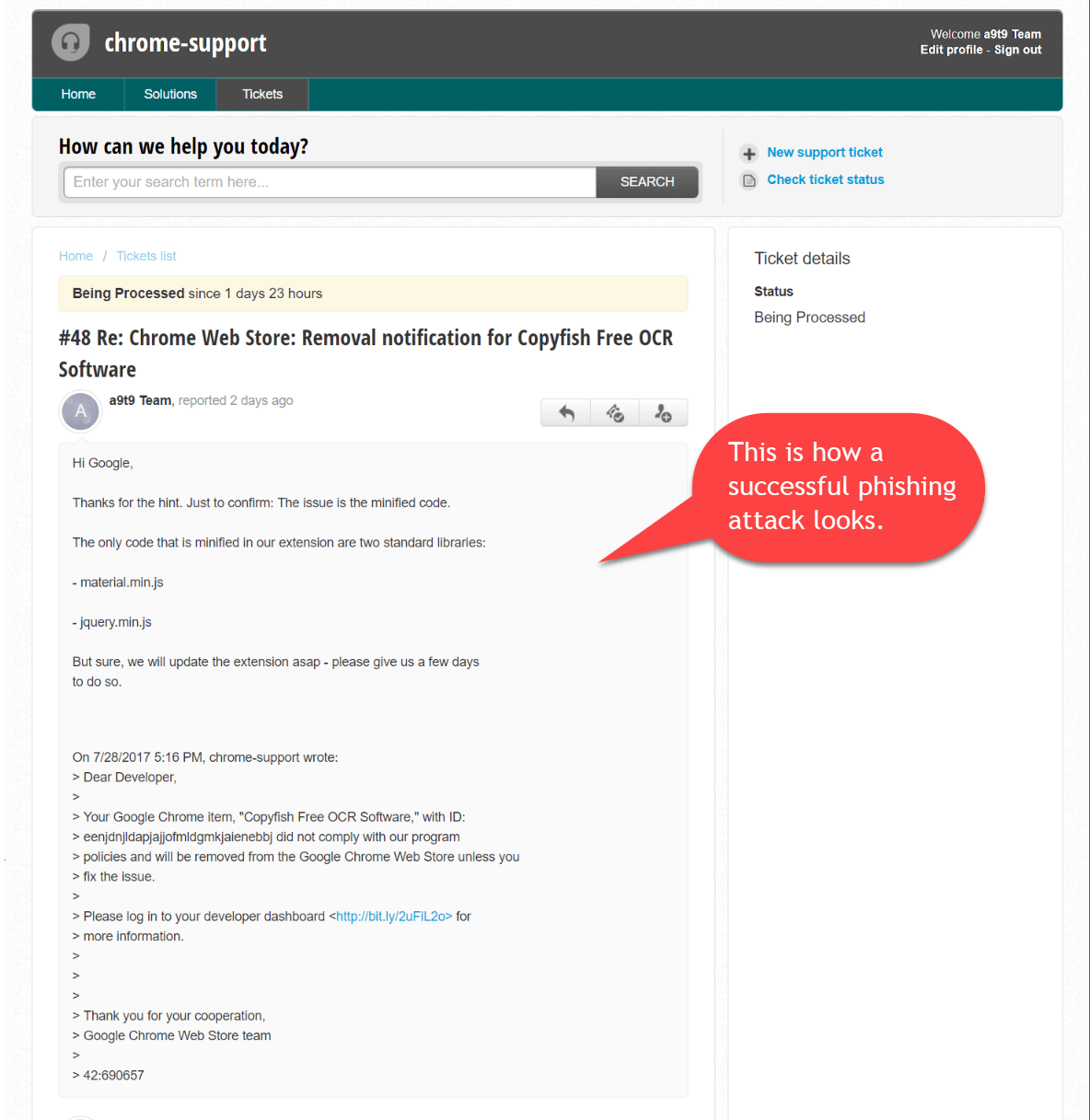
A screenshot of the phishing email. (Source: a9t9 software) The bit.ly link is clearly visible in the text-based version of the phishing email seen above. Unfortunately, the team member was using HTML-based email at the time of the the attack. They didn't spot the bit.ly link hidden in the message and assumed it was legitimate. After they clicked on the attack link and entered in the password for a9t9 software's developer account, those behind this attack updated the extension on 29 July to "V2.8.5". The modified add-on began pushing out spams and ads the next day. Copyfish's makers noticed the issue fairly quickly. But they couldn't do a thing about it. As they relate in their post:
"We log into our developer account and boom - our Copyfish extension is gone! It seems the hackers/thieves/idiots moved it to THEIR developer account. We currently have no access to it! So far, the update looks like standard adware hack, but, as we still have no control over Copyfish, the thieves might update the extension another time… until we get it back. We can not even disable it - as it is no longer in our developer account."
On 31 July, someone helped a9t9 stop the extension from pushing out spam. But Copyfish's illegitimate owners could update the extension in the future to resume its malicious activity. To help prevent this from happening, the software company is currently working to reach the Chrome Store admins, report this instance of abuse, and regain access to their program. Attackers are known to target login credentials for a variety nefarious purposes. As a result, it's important that organizations and users alike protect themselves. For instance, enterprises should conduct phishing training with their employees and instruct them to hover their cursor over links embedded in emails before they click on them. For more information on how to defend against phishing attacks, please click here.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

