
Attackers are increasingly exploiting the fact that email gateways turn a blind eye to links to popular sites such as YouTube, in order to phish passwords from unsuspecting computer users. Researcher Ashley Trans of Cofense highlighted the threat in a blog post describing a recent phishing campaign. In the attack, an unsuspecting user receives an email which purports to come from SharePoint, claiming that a new file has been uploaded to his company's SharePoint site.
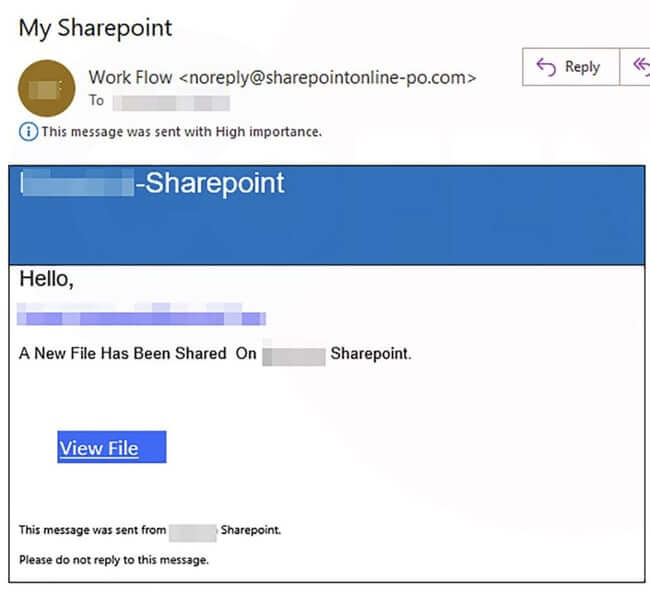
To the untrained eye the email may appear legitimate, and an unwary user might click on the link contained inside the email without proper due care and attention. A more cautious user might have hovered their mouse cursor over the link within the email, and found that it actually took them via YouTube.
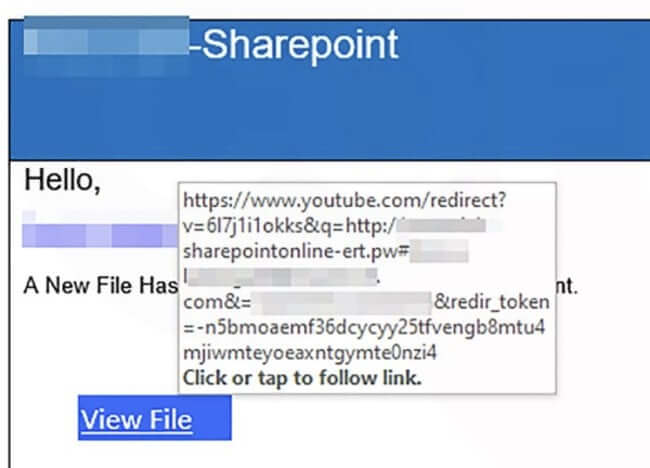
Closer examination reveals that although the link in the email does indeed point initially at YouTube (youtube.com), it also sends a series of parameters telling YouTube to redirect any traffic to a URL at <companyname>[.]sharepointonline-ert[.]pw, which in turn ultimately takes the user's browser to its final destination: a phishing page hosted on a legitimate Google site, googleapis.com.
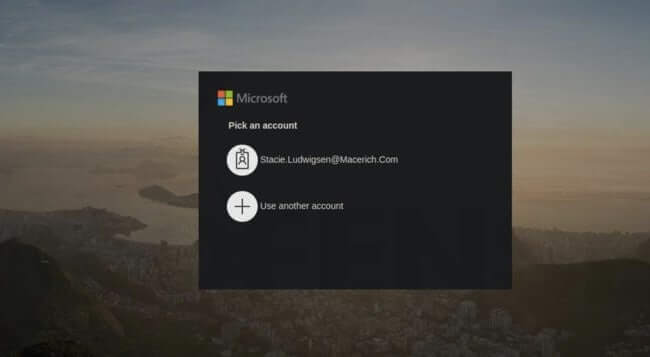
In the attacks seen by Cofense's research team, the phishing page poses as a harmless-looking Microsoft login page. The username field of the login page is automatically populated with the target's email address, and any password entered is automatically sent to criminals. Again, it's easy to understand why users would believe the webpage to be genuine. According to Cofense, it will not be obvious to most users that anything about the page is suspicious:
Nothing appears amiss–in fact, it is almost a perfect replica. The main differences are: the box surrounding the login is black instead of white; the small detail of the banner at the bottom has different information than Microsoft’s actual login; and the copyright year is showing as 2019.
The disappointing truth is that YouTube provides a method for anyone to create a link at youtube.com, which automatically redirects browsers to third-party phishing sites without any warning. And because email gateways typically whitelist popular domains such as youtube.com, facebook.com, and other social media sites it's a highly effective way for attackers to get their malicious links in front of innocent users. In contrast, an email which had linked directly to a phishing page might have been less successful at waltzing past email security solutions. If you're a regular user of YouTube you may already have seen this redirect facility in use. Just check the descriptions of different videos, and when they contain a link hover your mouse over it to see where it will take you. A YouTube video with a description containing a link will actually follow this format: https://www.youtube.com/redirect?q=[target_URL]&redir_token=[token]&event=video_description&v=[video_ID] As researchers have noted before, the system can be exploited to trick users if a valid token is taken from a legitimate YouTube redirect link and then used in a malicious campaign. One way to counter the problem would be for email gateway filters to treat YouTube redirect links with more suspicion, rather than assume that any link pointing to youtube.com is going to keep the user at youtube.com. But ideally I would like to see Google tighten up how it checks redirect links to prevent them from being abused by attackers in phishing attacks like this.
Editor’s Note: The opinions expressed in this guest author article are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

