
Security researchers spotted a phishing campaign that used SharePoint to bypass email gateway and other perimeter technologies. Cofense learned of the campaign after it analyzed an attack email sent from a compromised account @independentlegalassessors.co.uk. The email asked the recipient to review a proposed document by clicking on an embedded URL. In this particular instance, bad actors wrapped the URL with Symantec’s Click-time URL Protection. They also crafted the URL so that it redirected the recipient to a compromised SharePoint account in order to deliver a secondary malicious URL embedded within a malicious OneNote document. This URL, in turn, sent users to the main phishing page.
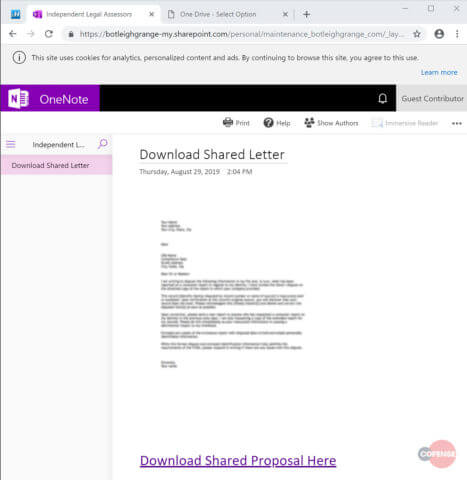
Malicious OneNote document (Source: Cofense) Milo Salvia, a threat analyst at Cofense, described what happened next in a blog post:
The phishing page is a cheap imitation of the OneDrive for Business login portal. There the recipient is given two options to authenticate: with O365 login credentials or credentials from any other email provider. We see this tactic quite often, as it increases the chances that the recipient will log in.
Further analysis by Salvia and his fellow researchers revealed that the campaign used login.php to post credentials stolen from the phishing page to [@]gmail[.]com, another compromised account. By using SharePoint, malefactors empowered their campaign to evade most email perimeter technologies. It's therefore not surprising that this isn't the first instance in which phishers have used SharePoint. In fact, digital criminals are increasingly turning to SharePoint as a malware infiltration technique to steal users' Office 365 login credentials. This campaign highlights the importance of organizations taking steps to protect themselves against a phishing campaign. One of the best ways they can do this is by educating their employees about some of the most common types of phishing attacks in circulation today. Here's a great place to start.

