
Researchers have detected a new phishing campaign that uses some clever tricks in order to steal users' Stripe credentials. Cofense discovered the campaign when it came across an attack email that pretended to originate from "Stripe Support." The message informed recipients that their account contained invalid details and that it was therefore scheduled to be suspended unless they acted quickly. Using that fabricated fear and sense of urgency, the email instructed the recipient to click on the embedded "Review your details" hyperlink.
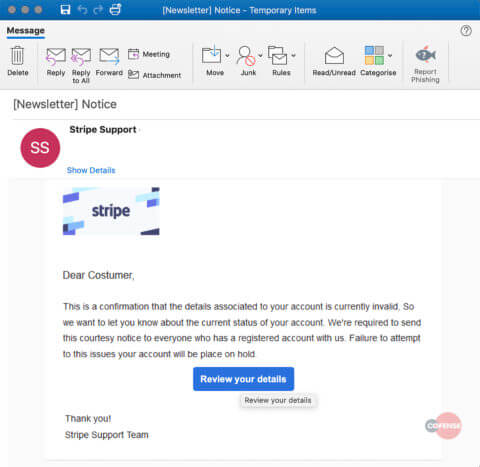
The attack email analyzed by Cofense. Those responsible for this campaign crafted the hyperlink so as to foil the efforts of security-minded users. As Cofense explained in its analysis of the scam:
Usually one can check the destination of the hyperlink by hovering over it with the mouse curser. The true destination of this hyperlink is obscured by adding a simple title to HTML’s <a> tag, which shows the recipient the title “Review your details” when the recipient hovers over the button instead of the URL. Potentially this is a tactic to mask the true destination from a vigilant recipient.
When a recipient clicked on the hyperlink, they found themselves redirected to a phishing website designed to look like the Stripe customer login portal. Upon submitting their email account and Stripe password, the phishing site displayed another form that asked victims to hand over their bank account number and phone number. The campaign then asked those who complied to enter their email account and password once more before sending them to the legitimate Stripe login page. The attack email detected by Cofense highlights the importance of organizations educating their employees about the dangers of phishing attacks. One of the best ways they can do this is by familiarizing their workforce with some of the most common types of phishing techniques. This resource is a great place to start.

