
Security researchers came across a phishing email that used a Google Ad redirect as a part of its efforts to steal victims' Microsoft credentials. Cofense found that the email originated from the legitimate email address “info@jtpsecurity[.]co[.]za.” The security firm reasoned that attackers had compromised that email account and abused their access to target employees in multiple organizations. The email arrived with a message indicating that it was sent with "High importance." When coupled with the inclusion of the word "security" in the sender's email address and the use of "Recent Policy Changes" as the subject line, this tactic attempted to trick the recipient into believing that the email was important and required immediate attention. In support of this ruse, the email informed the recipient that they needed to accept new "Terms of Use & Privacy Policy.” It then instructed them to click on either an "Accept" button or a "Learn More" option.
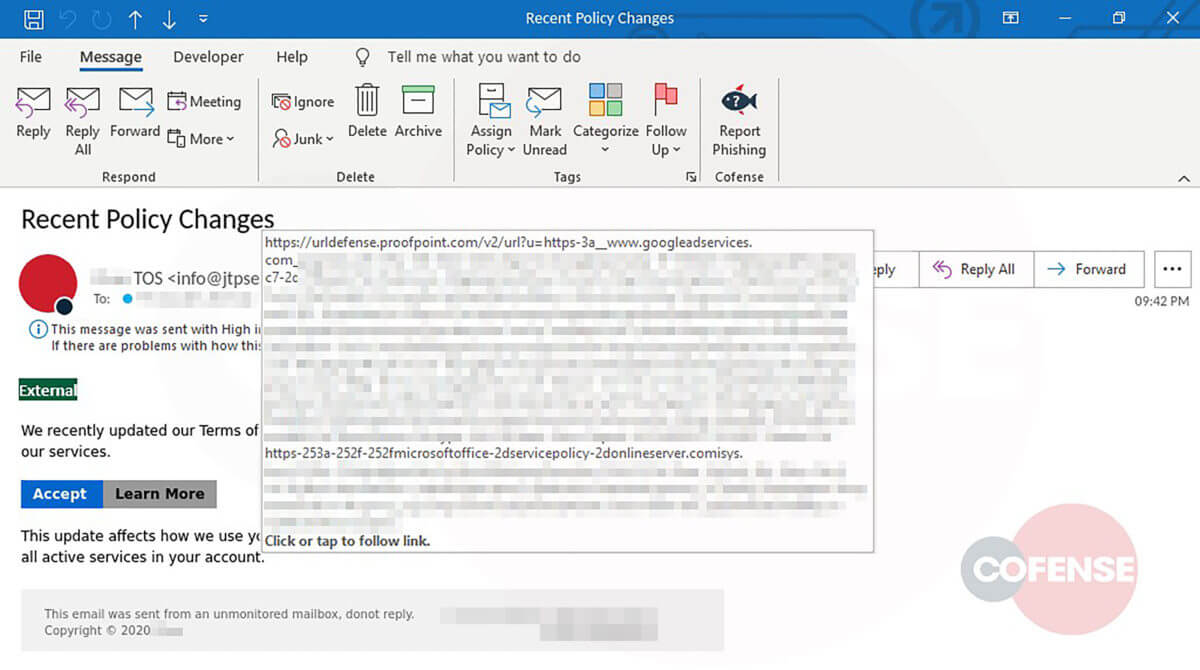
A screenshot of the phishing email with the buttons' URL displayed. (Source: Cofense) The researchers at Cofense found that both buttons contained the same embedded link. As they explained in their research:
...[T]he threat actor has utilized a Google Ad Services redirect to pilot users to their phish. This suggests that the threat actor(s) may have paid to have the URL go through an authorized source. In turn, this easily bypasses secure email gateways and exposes employees to the phish.
From there, the campaign led the user to a fake page that functioned as a duplicate of the official Microsoft page. This imposter page presented the visitor with a privacy policy that contained logos for both Microsoft and the user's company. It then prompted them to click on an "Accept" button. Doing so sent the user to another page designed to steal their Microsoft credentials. Upon receiving their victim's details, that page showed a "We've updated our terms" dialog box before redirecting them to a legitimate Microsoft page containing the tech giant's service agreement. The campaign discussed above highlights the need for organizations to defend themselves against phishing operations. They can do so by educating their employees about some of the most common types of phishing attacks that are in circulation today.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

