
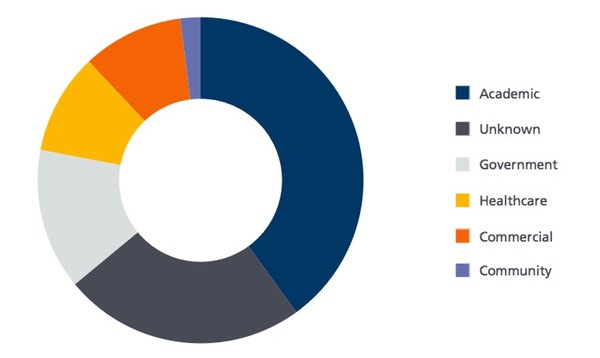
Researchers at BAE Systems have published a report investigating the return of the Qbot network-aware worm, revealing infections on some 54,517 PCs. 85% of the affected systems are based in the United States, with academic, government and healthcare industry networks particularly badly hit. Earlier this year, for instance, the media reported that the Royal Melbourne Hospital's pathology department had been badly affected.
The Qbot worm, also sometimes known as Qakbot, is not a new threat. First seen as far back as 2009, the malware continues to spread because online criminals have taken its original source code and continued to adapt it to evade detection. Judging by BAE Systems' findings, they appear to have been worryingly successful. Typically Qbot is being spread via compromised websites, hosting the Rig exploit kit. When a user visits the hacked site on a vulnerable computer, a malicious obfuscated script is silently executed to serve up the exploit and install the malware onto Windows PCs.
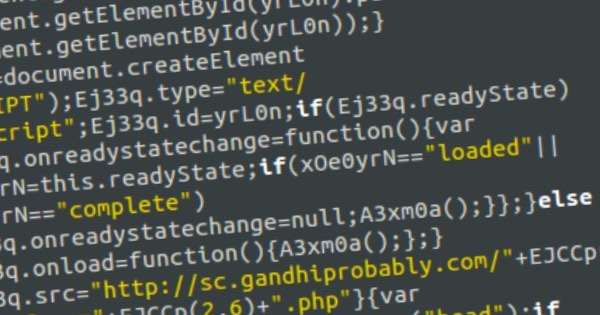
Although this is a common method of spreading Qbot, it is also for attackers to target corporations through malicious emails. BAE Systems reports that detection by anti-virus products, however, is hampered by the fact that the Qbot malware contacts its Command & Control (C&C) center in order to receive updates, mutating its appearance, re-compiling and re-encrypting itself, using server-based polymorphism in an attempt to avoid identification.
"The server-based polymorphism used by Qbot allows it to largely avoid AV detection. Typically, out of 55 AV vendors, only a couple of reputable AV vendors are reliably able to detect Qbot - or to be specific, generically detect its external encryptor. After a few days, the same sample is normally detected by more than half of the AV engines. However, as the bot normally updates itself with a new version within a day or two, it keeps ahead of this process and remains undetected for long periods."
Furthermore, the malware is capable of detecting if it is running inside a Virtual Machine sandbox, and change its behavior in an attempt to avoid being spotted. Any unreliability in detection by security software is an issue, because of what Qbot can do once it has infected your computers. Qbot is primarily designed to harvest passwords and other credentials. Sneakily, Qbot attempts to grab passwords from Windows' Credential Store, potentially revealing network logins, and passwords used for Outlook, Windows Live Messenger, Remote Desktop and Gmail Messenger. Furthermore, Qbot attempts to access Internet Explorer's password manager, stealing cached username and password credentials. With these details - and further credentials stolen from network traffic - Qbot's attackers can break into FTP servers and infect other websites with exploit kits to spread their malware. Furthermore, because of its backdoor capabilities, Qbot opens a potential route for hackers to steal sensitive data or intellectual property, disrupt infrastructure, or plant more sophisticated malware inside an organization. BAE Systems reports that Qbot is becoming a more pernicious threat - exploiting its server-based polymorphic capabilities and other tricks in an attempt to avoid reliable detection. However, it doesn't appear that the hackers behind the Qbot attacks are immune to making their own mistakes. BAE Systems describes how the criminals "tripped up" when Qbot infected a small number of out-of-date PCs. Rather than infect the PCs, it actually caused them to crash - alerting the affected organization that there was a problem on its network and causing the malware's identification earlier than perhaps might otherwise have occurred. Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor, and do not necessarily reflect those of Tripwire, Inc.

