
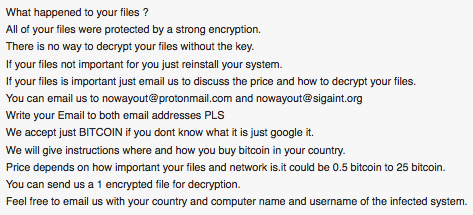
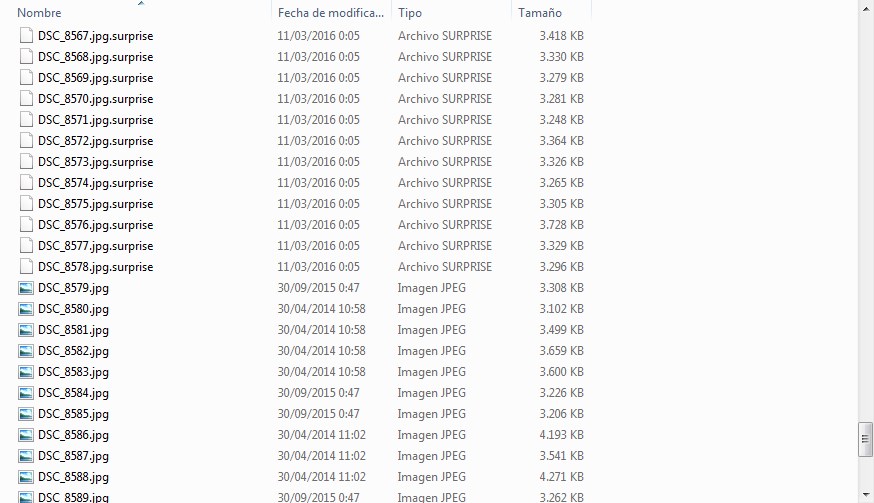
Researchers have tied the propagation of a new type of ransomware to a TeamViewer user. TeamViewer is a cross-platform service that enables remote computer access for tech support calls, meetings, and other purposes. It has been installed on more than a billion devices, which makes its potential attack surface quite extensive. On March 9th, someone posted to the Bleeping Computer forum a thread in which they describe how all of their pictures videos, and PDFs, among other files, have been encrypted and that the ".surprise" extension has been concatenated to every affected filename. According to the infected user, the "Surprise" ransomware downloaded three files onto their computers. One of the files is a ransom note that instructs the victim to email both "nowayout[at]protonmail[dot]com" and "nowayout[at]sigaint[dot]org," at which point they will be told to pay a sum of between 0.5-25 BTC (approximately US$200-US$10,000) depending on "how important your files and network files is."
Source: Bleeping Computer Bleeping Computer's Lawrence Abrams has analyzed the ransomware and determined that it is based off of EDA2, one of two file-encrypting open-source projects (along with Hidden Tear) originally developed by a security researcher in an effort to educate users about malware. The researcher has since abandoned the project after bad actors co-opted his code and used it to develop at least 20 different types of ransomware, including Magic and one that uses the ".locked" extension. As of this writing, the command and control (C&C) servers for Surprise are down. This means that affected users have little to no hope of recovering their files unless the servers go back online.
Source: Bleeping Computer But that's not the end of the story. Additional analysis provided by David Balaban of Privacy PC has revealed that all of the infected users who joined Bleeping Computer's thread on Surprise had TeamViewer installed on their computers.
"The analysis of TeamViewer traffic logs showed that someone had remotely executed surprise.exe process on computers, which resulted in malware injection behind the scenes," Balaban explains in a post. "Furthermore, the researchers discovered that the user ID was identical across most of the unauthorized remote connection sessions, but not all. It’s therefore premature to state for a fact that one account (479440875) was used to infect systems. The scariest thing is that the strange traffic behavior had been taking place for months in some of the reported cases."
To get to the bottom of this ransomware campaign, Balaban recommends that TeamViewer attempt to identify the suspicious account by its user ID.
UPDATE (03/21/2016)
Axel Schmidt, Public Relations Manager at TeamViewer, has contacted The State of Security to clarify this incident:
"We looked thoroughly at the cases that were reported to us. And according to our investigation, the underlying security issues cannot be attributed to TeamViewer," he told The State of Security in an email. "So thus far we have no evidence that would suggest any potential security breach of TeamViewer that attackers exploit. Furthermore, a man-in-the-middle attack can nearly be excluded because of TeamViewer’s deployed end-to-end encryption. Apart from that, we would like to state, that none of the reports currently circulating hint at a structural deficit or a security glitch of TeamViewer."
Schmidt has also emphasized that "careless use," or the use of the same password across multiple online accounts, explains nearly all of the cases that TeamViewer's teams have examined. With that in mind, he recommends that all TeamViewer users download the software only through official company channels; protect all of their web accounts with strong, unique passwords; protect their TeamViewer accounts specifically with two-factor authentication; and determine that their device/computer has not already been infected by malicious software.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

