
A hacker known as Rasputin used SQL injection (SQLi) to breach the databases of over 60 universities and government agencies. The threat actor, a Russian-speaking computer criminal who gained notoriety back in December 2016 for hacking the U.S. Election Assistance Commission (EAC), is targeting universities and government facilities based in the United States and Britain. Dozens of organizations have already fallen victim to Rasputin. These institutions include New York University, University of Cambridge, the City of Pittsburgh, the U.S. Department of Housing and Urban Development, and the Fermi National Accelerator Laboratory.
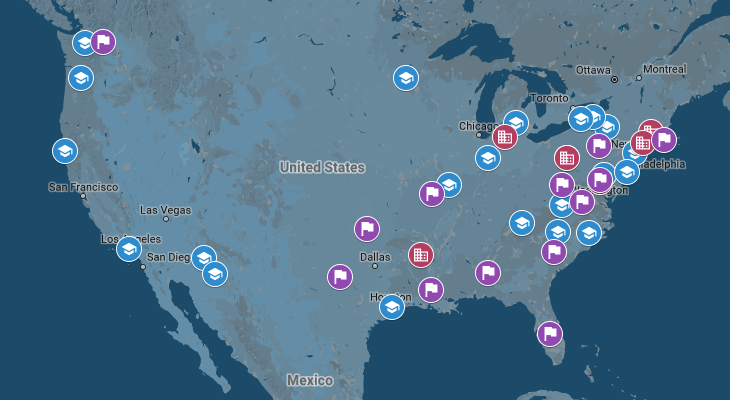
Geographic locations of Rasputin’s latest U.S. education and government victims. (Source: Recorded Future) Threat intelligence provider Recorded Future feels Rasputin's focus on these industry verticals is deliberate. As it explains in a blog post:
"These are intentional targets of choice based on the organization’s perceived investment in security controls and the respective compromised data value. Additionally, these databases are likely to contain significant quantities of users and potentially associated personally identifiable information (PII)."
Rasputin pulled off the attacks using a technique known as SQL injection. It's when a bad actor exploits a vulnerability that allows them to directly access a database through a web application or browser. Databases that are vulnerable to SQLi don't sanitize a user's input before they execute an instruction. Such a hole allows for an attacker to download, modify, and view a database's contents without the proper authorization. It's therefore no surprise this type of vulnerability has been responsible for some high-profile breaches like those that affected Yahoo and LinkedIn. For more information on how SQLi works, please view this three-part guide.
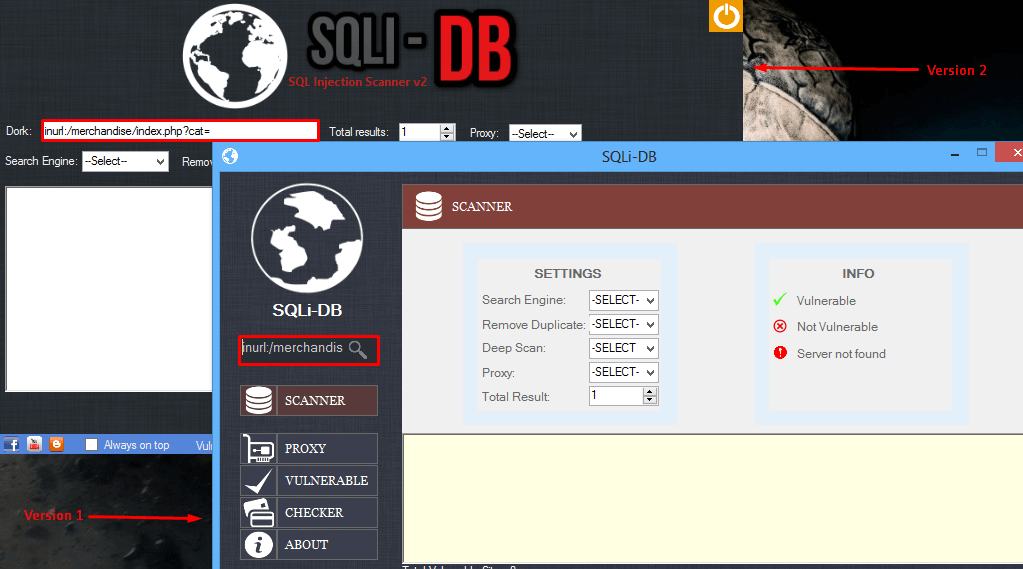
(Source: Recorded Future) Recorded Future is troubled by the prevalence of actors like Rasputin who use tools to search for databases that are vulnerable to SQLi:
"The evidence suggests economics play a role in causation for this troubling trend. The problem and solution are well understood, but solutions may require expensive projects to improve or replace vulnerable systems. These projects are often postponed until time and/or budget is available, until it’s too late to prevent SQLi victimization."
To address this issue, the threat intelligence provider feels organizations should receive a financial incentive to plug SQLi holes in their systems.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

