
There are several technical methods of stealing passwords via malware or software vulnerabilities, and one of the most difficult to defend against occurs when users disclose their credentials unknowingly. Yes, I am referring to phishing. Specifically, phishing that tricks users into accessing a fake website and entering their credentials. We often see fake Gmail or Dropbox emails, and most users have the skills to deduce that those are classic phishing emails.
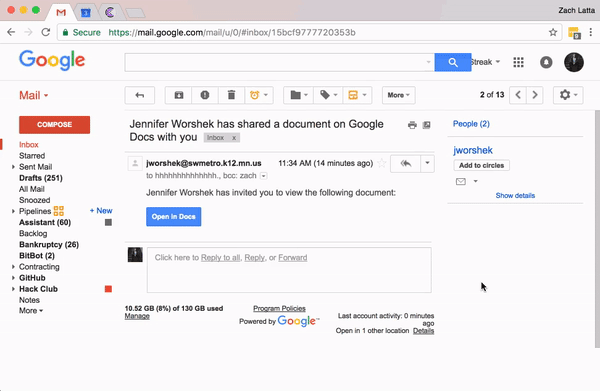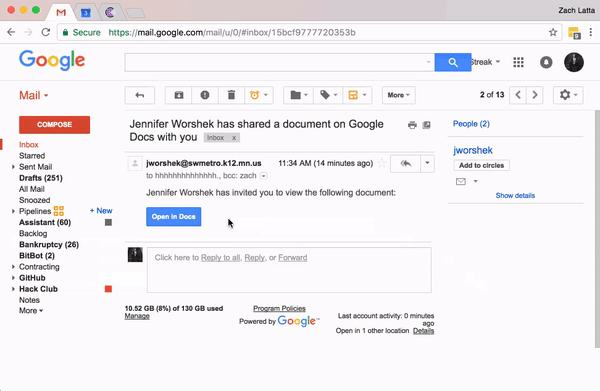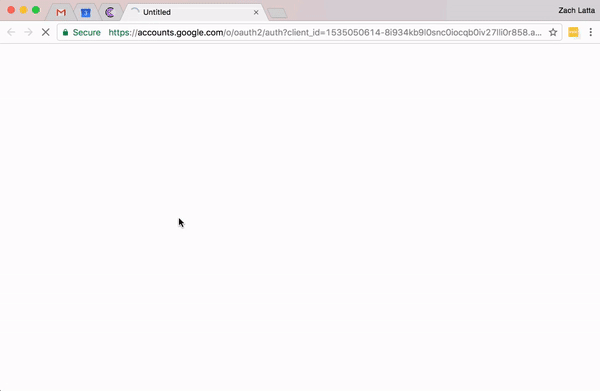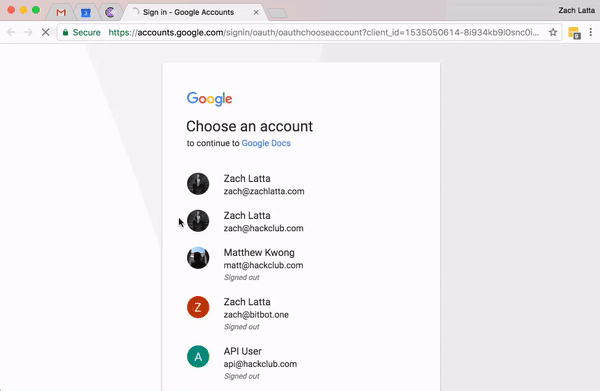
However, the lines get a little blurred when a phishing email seems to come from a work-related or other trusted source. Imagine an email that claims to come from your IT department, inviting users to log into the new HR system. If standard communication practices and channels are in place, this announcement will likely seem odd. However, if that is not the case, this email may prompt users to, at least, click the link. And if the phishing site looks convincing enough, a trusting user may even enter his or her credentials. At that point, the damage is done.
So, how can an organization defend against this method of phishing?
One of the best defenses is to implement 2-factor authentication wherever possible. If credentials are stolen, a second factor is required before an attacker can leverage those credentials. This will not stop an attacker from stealing credentials, but it may prevent an attacker from using them successfully. Another important defense is to train users. This allows users to practice the skills in order to spot phishing and allows the security team to learn valuable insights from user behavior that might be taken for granted by a technical person. For instance, users may make the assumption that the organization has filtering in place to prevent any malicious email from getting through, which simply isn’t true. Regardless of any high quality email protection in place, some malicious emails may still get through. This is also true of malicious sites; users may assume there are protections in place to prevent access to malicious sites, but even the best web filtering tools can let a few malicious sites through. Once users understand that your security tools may not stop every malicious email or site, they may develop a heightened sense of responsibility to help maintain the security of the organization. It is also important for users to understand how easy it is to set up a phishing site. Setting up a website with a login form, a title, and your organization’s logo is trivial. An attacker can also easily clone any publicly available web page, even a web page from your organization, and register a similar domain.
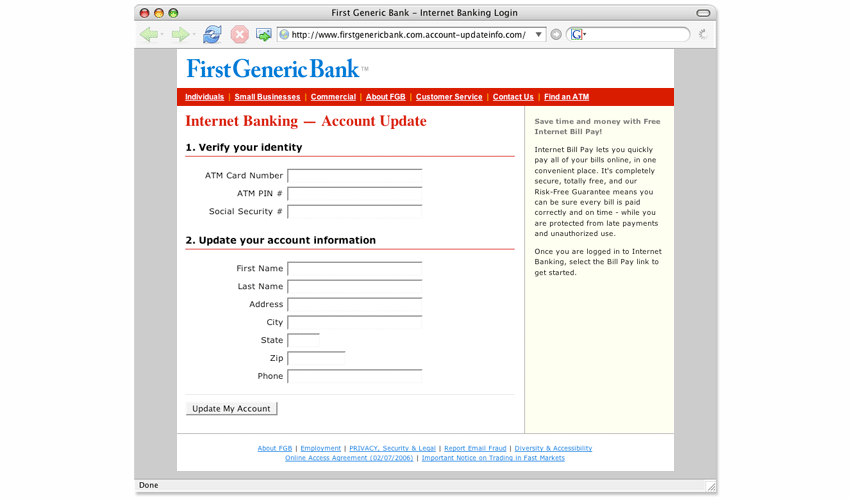
Source: PhishTank An attacker can also obtain a free certificate to display the lock icon, which only means that the URL matches the certificate and its traffic has been encrypted. However, this doesn’t ensure users’ security. Users are a large component of the security equation. Therefore, focusing on educating users to make secure choices and migrating to a security-conscious organizational culture will provide a major win for an organization’s security posture.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

