
Chinese networking telecommunications equipment and services company Huawei has patched a vulnerability in its MBB (Mobile Broadband) product E3272s that if exploited could lead to denial-of-service attacks and remote arbitrary code execution. According to a security bulletin released by the company,
"An attacker could send a malicious packet to the Common Gateway Interface (CGI) of target device and make it fail while setting port attribute, which cause a DoS attack. (Vulnerability ID: HWPSIRT-2015-05103)."
Those who wish to exploit this flaw must first log into a PC using the affected product, at which point in time they can send a malicious packet to the targeted device, which in addition to producing a DoS condition could lead to remote arbitrary code execution via a cross-site scripting (XSS) attack or stack overflow. The vulnerability, which received a base score of 4.9 and a temporal score of 4.1 using the CVSSv2 scoring system, was first detected by researchers Timur Yunusov and Kirill Nesterov at security firm Positive Technologies with the assistance of the information security specialist Alexey Osipov back in August of this year.
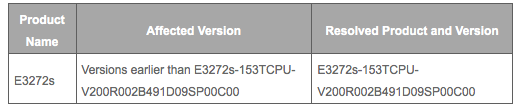
Source: Huawei Huawei has since patched the vulnerability and is requesting that customers contact its TAC (Technical Assistance Center) to request the necessary security upgrades. The TAC's contact information can be found here. News of this vulnerability follows on the heels of a research project launched by Positive Technologies in late 2014 that sought to test the security resilience of six different series of 4G USB modems (including the Huawei E3272s) with 30 different firmware versions. Only three of those versions were proven to be "hack-resistant".
"By exploiting detected flaws, an intruder can gain rights on a remote modem, take control over the computer connected to the vulnerable modem, and obtain access to the subscriber's account in the mobile operator's portal," the research team at Positive Technologies observed. "Moreover, attacks on SIM cards via binary SMS messages allow an attacker to intercept and decrypt a subscriber's traffic, track his or her location, and block the SIM card."
The flaw also comes a few months after Ilya Karpov of Positive Technologies helped detect a host of vulnerabilities, among them two Schneider kits and a number of remote and local exploits, affecting a variety of Siemens' SIMATIC HMI devices.

