
A security researcher successfully compromised a Facebook server only to discover that someone had already been there. Bug bounty hunter Orange Tsai explains in a blog post that after poking around some Class C IP addresses of "vpn.tfbnw.com," an internal domain for Facebook, he came across a special server with the name "files.fb.com." The researcher quickly determined that the IP appeared to be Accellion's Secure File Transfer. Through several rounds of testing, he eventually found seven vulnerabilities that he exploited to install a webshell and take control of the server. He also reported those flaws privately to Accellion. While he was gathering vulnerability details to submit to Facebook, he spotted some strange PHP error messages.
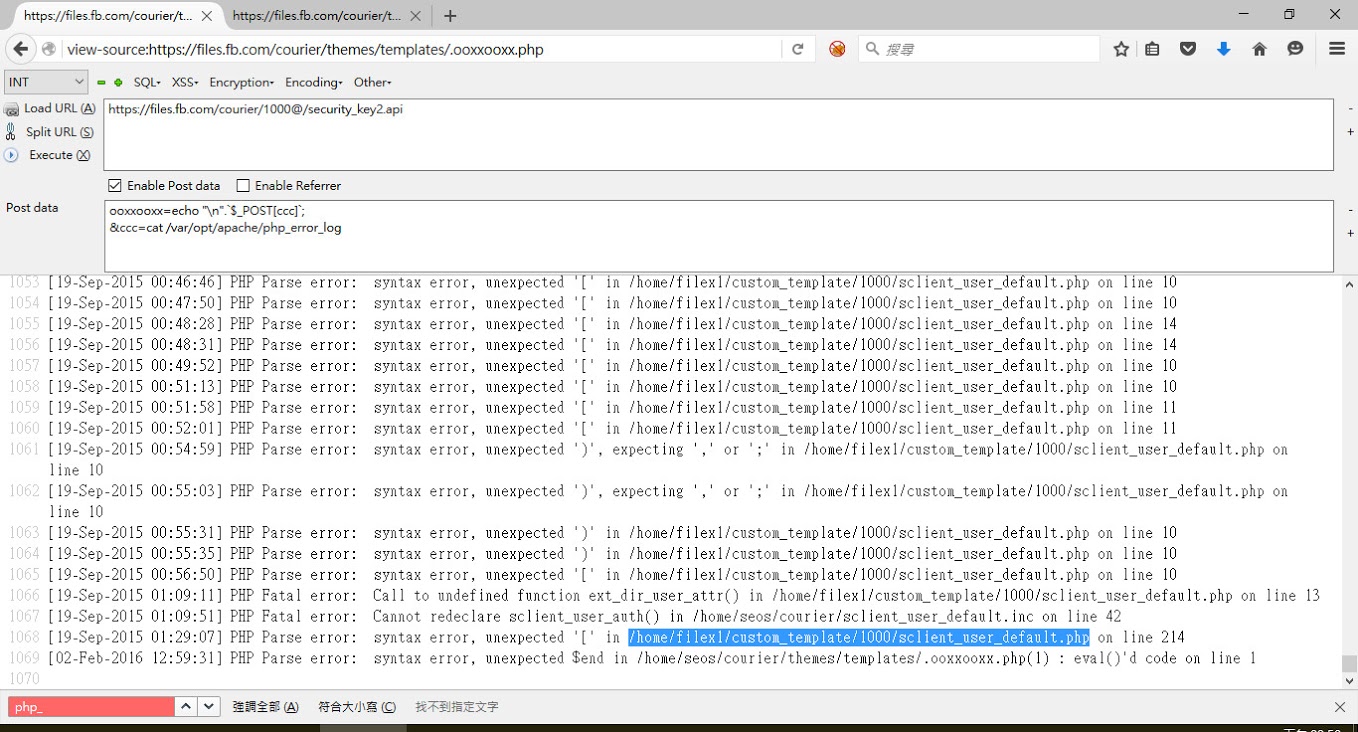
The PHP error log Those led him to a few webshell files, including some one-line backdoors and a file containing the original PHP app for password verification.
"A brief summary, the hacker created a proxy on the credential page to log the credentials of Facebook employees," Orange recalls. "These logged passwords were stored under web directory for the hacker to [access]... every once in a while."
The scripts were used once in July and then again in September of last year. After collecting some additional information about his exploit, the researcher submitted his findings to Facebook's bug bounty program back in February of this year. He was rewarded US$10,000 for his efforts. Since then, Reginaldo Silva, a security engineer at Facebook, has confirmed that the malicious scripts were put in place by another researcher hoping to snag a bug bounty.
"We're really glad Orange reported this to us. In this case, the software we were using is third party. As we don't have full control of it, we ran it isolated from the systems that host the data people share on Facebook. We do this precisely to have better security," said Silva. "We determined that the activity Orange detected was in fact from another researcher who participates in our bounty program. Neither of them were able to compromise other parts of our infrastructure, so the way we see it, it's a double win: two competent researchers assessed the system, one of them reported what he found to us and got a good bounty, none of them were able to escalate access."
For information on Facebook's bug bounty program, please click here.

