
A security researcher has come up with a method that would allow an attacker to bypass the iOS passcode limit on certain iPhone models. Sergei Skorobogatov's process consists of an attacker mirroring the Flash memory stored in an iPhone 5c's NAND cells. During a press conference back in March, FBI Director James Comey explained his agents could not use a NAND mirroring attack to bypass the iOS passcode limit on the iPhone 5c of one of the San Bernardino shooters. He said it just "doesn't work." Several days later, the FBI announced it had successfully unlocked the terrorist's iPhone using a method it had purchased for one million dollars that neither targeted the device's NAND cells nor required Apple's assistance. As it turns out, the FBI might have wasted taxpayers' money when they could have unlocked the iPhone in question for less than 100 USD. That was Skorobogatov's total budget for his NAND mirroring attack, a method he explains in his research paper (PDF):
"So far no one has demonstrated a fully working hardware-based NAND mirroring attack on iPhone 5c. Therefore, this paper is aimed at demonstrating the feasibility of such a process."
After disassembling the iPhone and removing the NAND chip, the researcher wired the chip to a connector and verified he could eavesdrop on all NAND communication. That process was not easy. Skorobogatov encountered several signal integrity issues that prevented the phone from properly booting. He addressed those problems using hardware-based solutions, such as by inserting small termination resistors on all signal lines. Once he confirmed that everything was working, the researcher captured all of the NAND chip's commands so that he could properly write its contents to a backup NAND chip.
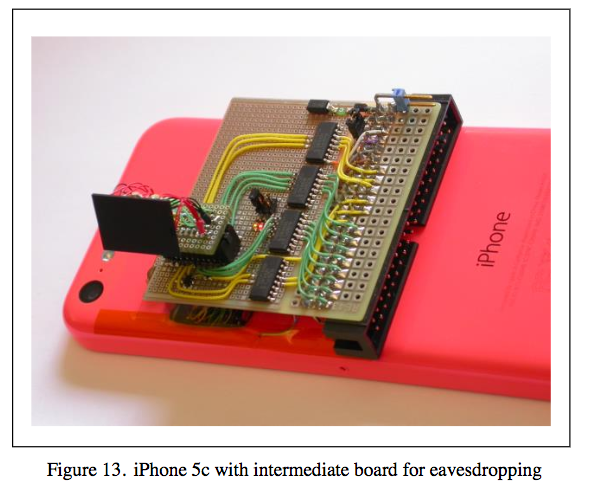
The researcher then connected the original NAND chip to the iPhone 5C, tried the passcode 6 times, powered down the device, erased all changes to the chip that indicated someone had unsuccessfully attempted to login using the backup, and plugged the NAND chip back into the phone. Using this method, the researcher estimates the FBI could have brute forced the passcode in a matter of days:
"Once the phone is powered up and the screen is slid the passcode can be entered six times until the delay of one minute is introduced again. Then the process of mirroring from backup can be repeated again and again until the correct passcode is found. On average each cycle of mirroring for six passcode attempts takes 90 seconds. Hence, a full scan of all possible 4-digit passcodes will take about 40 hours or less than two days."
You can view a demonstration of the method below: https://www.youtube.com/watch?v=tM66GWrwbsY Okay, so if this method could work on an iPhone 5c, why didn't the FBI try it? Matthew Green, a computer science professor and cryptographer at Johns Hopkin University, thinks the FBI might have been deterred by the possibility of damaging the terrorist's data beyond repair. As quoted by WIRED magazine:
"Everyone I know who was trying it couldn’t get past the fact that it required incredible soldering abilities. You could fry the chip."
As of this writing, the FBI has not yet commented on Skorobogatov's research.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

