
A security researcher recently discovered a cross-site scripting (XSS) vulnerability in Google by accident. Patrik Fehrenbach explains in a blog post that he came across the flaw after deciding to take advantage of Google Cloud Console's 60-day free trial and test for XSS bugs. XSS flaws come in two types. A bug is 'reflected' if the payload executes immediately after a user accesses a link, and it is 'stored' if the payload is stored in a database and executes once other users visit the page. Fehrenbach tested for both types, but he came up with nothing. After about two months, Google sent the researcher a notification that his free trial was about to expire. Rather than have to pay for Google Cloud Console, the researcher decided to delete his project that just happened to have a XSS payload in its title. To his surprise, his payload executed.
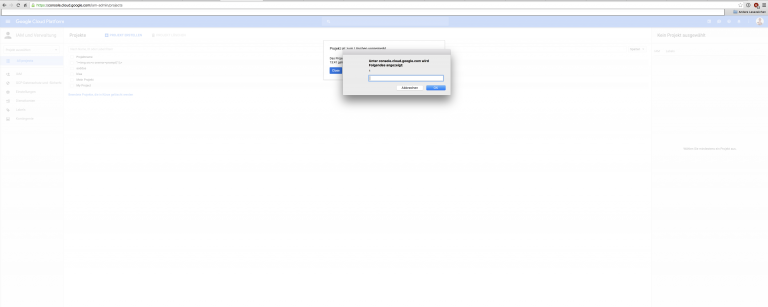
"As it turned out, Google was not filtering the error message once a project which canceled. Astute readers may question why this was not classified as a low level self XSS. This issue was escalated because the Google Cloud Platform can be used by multiple users; if a user creates a project with a malicious XSS payload, that payload could be used against the project administrator to execute malicious javascript (if they delete the project, which seems likely)."
Fehrenbach collected the vulnerability details and sent them to Google in a report. The tech company responded by fixing the flaw and awarding the researcher $5,000 for his efforts. You can view a video of the proof-of-concept exploit Fehrenbach sent to Google's Vulnerability Rewards Program (VRP) here. News of this discovery follows on the heels of popular domain registrar GoDaddy's remediation of a blind cross-site scripting (XSS) vulnerability that attackers could have used to take over, modify, or delete users’ accounts.

