
On November 17, 2016, the security community witnessed the resurgence of a familiar enemy. That's the day when Shamoon 2, the successor of an attack campaign which first emerged in 2012, delivered Disttrack wiper malware to an organization based in Saudi Arabia. True to its design, Disttrack spread through the company's network and overwrote the Master Boot Record (MBR) on every computer it found. The malware thereby rendered each infected machine unable to properly boot its operating system. Shamoon's reemergence surprised everyone. But as it would turn out, the attack campaign wasn't finished. Not by a longshot.
'Enhanced' Shamoon 2 Strikes Again
On November 29th, 2016, researchers at Palo Alto Networks detected an attack against a second organization based in Saudi Arabia. The campaign delivered a Disttrack sample that was in many respects similar to the November 17, 2016, payload. As we saw in the first Shamoon 2 attack, the malware came with three components – a dropper, a communication module and a wiper. Disttrack also retained its ability to spread through the local network by logging in with legitimate domain account credentials, copying itself to the system, and creating a scheduled task that executes the payload. But not everything was the same. First, researchers found 16 sets of user and administrator account credentials hardcoded into the malware. All but one of those passwords fulfilled Windows' complexity requirements: they contained both uppercase and lowercase letters as well as at least one number and/or one symbol. That's not even the most significant change, however. Researchers at Palo Alto Networks explain:
"A new development with this latest Disttrack payload is that several of the usernames and passwords are found within official documentation as administrator accounts for Huawei’s virtualized desktop infrastructure (VDI) products, such as FusionCloud. This may suggest that the targeted organization used these credentials when deploying Huawei VDI systems. Shamoon actors may have obtained these credentials from a prior attack; however, it is also possible that the actors included these default usernames and passwords as an attempt to guess the login credentials to the VDI infrastructure."
So, what's the big deal? VDI solutions take snapshots of a system at a given time in a certain state. Organizations can therefore use these technologies to recover from wiper malware like Disttrack. But if Disttrack comes with default credentials for well-known VDI products, it can log into those solutions, wipe any saved snapshots, and thereby prevent an organization from restoring their systems.
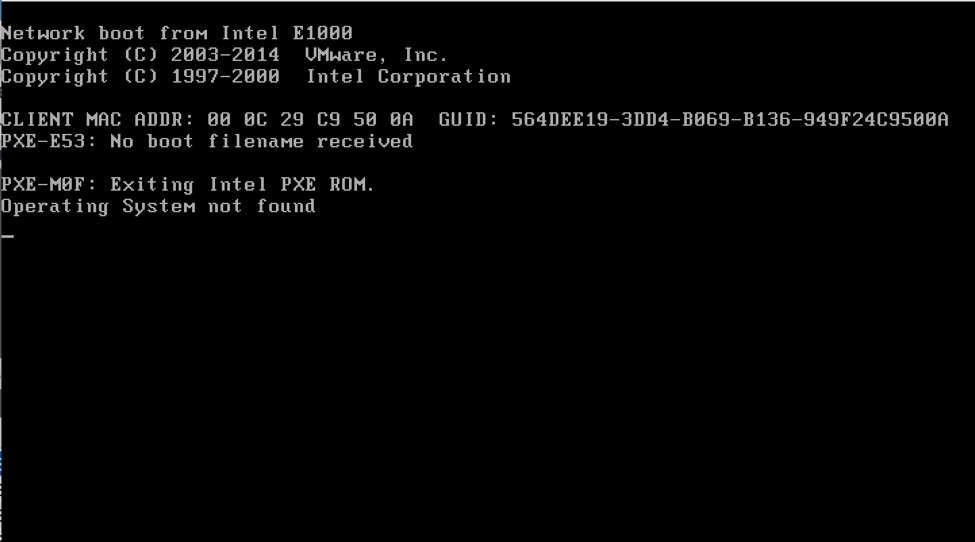
System unable to find its operating system. (Source: Palo Alto Networks)
Conclusion
Just like in the November 17, 2016, campaign, Disttrack configured itself to attack at a time that would allow the malware to do maximum damage. The malware sets its "kill time" to 01:30 on a Tuesday – a part of the day when most staff were offsite. By the time the organization's IT employees began arriving for work, Disttrack had already ravaged multiple parts of the company's network. Don't let this happen to your organization. To protect against Shamoon's destructive forces, enterprises should train their employees to avoid clicking on suspicious links and email attachments. They should also consider implementing additional safeguards designed to protect the credentials of their VDI deployment as well as deploy a tool like MBRFilter to prevent malicious actors from modifying a machine's MBR.

