
It is a well-known fact that legacy equipment shall continue to play a crucial role in the continuity and stability of critical infrastructure, especially in industrial control systems. A recent Center for Digital Government survey found that 70% of respondent agencies depend on legacy infrastructure for their operations. Another recent report from Deloitte and MAPI, “Cyber risk in advanced manufacturing,” underscores the importance of protecting the legacy control systems. As per the report, modern industrial control systems are considerably easier to secure than their predecessors. It follows a survey of more than 200 manufacturing enterprises, of which 40 percent reported they were affected by cyber incidents in the preceding 12 months. The report highlights the facts that the greatest risk exists in legacy industrial control systems.
So what exactly is legacy infrastructure? Why does it need protection?
In contrast to the latest and advanced equipment used in modern smart industries such as smart grids or smart factories, legacy equipment is generally dated and in some cases 20, 30 or even more years old. This equipment still works and is often not replaced, sometimes owing to the enormous capital expenditure required for an upgrade. At times, such equipment does not even understand IP (Internet Protocol), as the communication protocol and may use some proprietary communication mechanism. Here the task of updating becomes ever-daunting, as what's required is to overhaul not only the control system equipment but the network infrastructure, as well. Another big challenge with some of these dated control systems is they run old and sometimes outdated versions of operating systems or application software that are no longer supported by their manufacturers or even by the software development community. Such systems leave vulnerabilities unpatched, making them insecure to attacks and exploits. To add to it, these at times also do not support SSL (Secure Socket Layer) and/or TLS (Transport Layer Security) to provide authentication and encryption of the communication channel itself. Similarly, for devices that do support SSL and/or TLS, their versions are mostly outdated and unpatched. Even the availability of a software upgrade or patch does not address the final problem, as several of these systems do not upgrade at all. The impediments include remote and hard-to-reach locations of these systems and a complex upgrade procedure. Moreover, the mere upgrade process makes the system unavailable for the upgrade duration that is unacceptable downtime for critical infrastructure. All these shortcomings make these systems vulnerable to exploits, and once compromised, it is extremely hard to detect and remediate owing to the same reasons as the ones for not upgrading them. These exploits not only make the control system unavailable for normal operations; they create severe and catastrophic damage to the entire industrial operation, as well.
Three ways to protect your legacy infrastructure
Secure your end points
The endpoints that include a mélange of control system equipment such as remote terminal units (RTUs), programmable logic controllers (PLCs), intelligent electronic devices (IEDs), etc. should be made secure by allowing only those communication messages to reach them for which they are designed to operate. Snubbing out any and all unnecessary traffic from the communication channel leading up to the endpoint prevents it from being exposed to an exploit or an attack. There is a general notion within the industrial control system environment: “if it is not broken don’t fix it.” As long as the control system is working as expected, there is always a risk of destabilizing it by doing a software upgrade or maintenance. However, on the other hand, there is always a need to upgrade the system in order to protect it from vulnerabilities or protocol exceptions. In such cases, a protocol anomaly detection firewall, also called as a Deep Packet Inspection Firewall (since it not only looks at the packet headers but also the protocol message content deep within the packet to apply a filter), is a necessary means for allowing only valid and safe protocol messages to reach the end device, thereby alleviating the need for patching software vulnerabilities.
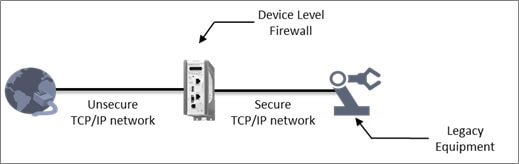
Figure 1: Device-level firewall to protect legacy end device from unwanted and malicious traffic
Secure your network
Often the network communication protocols used by legacy devices are themselves not secure inherently. Even when a certain level of security is present, it is limited to weaker versions of SSL or SSH (Secure Shell) that can be easily broken or exploited. It is extremely important to secure these communication channels to prevent man-in-the-middle attacks, thereby avoiding any dangerous impact to the control system. One of the ways to secure this channel is by encrypting the communication over an IPSec VPN (Virtual Private Network) tunnel. A VPN gateway facing a single or a bunch of control system endpoints ensure these messages are encrypted using strong algorithms that are practically impossible to break. In case the endpoints are not IP-enabled, such as legacy serial devices transmitting Modbus, Profinet or similar protocol messages, the edge terminal sever that is converting the serial data into TCP/IP should secure the IP network before its transmission. Many methods can be employed to achieve this security, SSL and IPSec VPN being the most prominent ones.
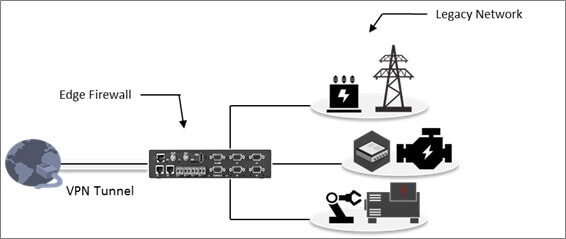
Figure 2: Edge firewall to protect legacy network from malicious traffic and man-in-the-middle attacks
Monitor your network and endpoint
Even when the endpoints and networks are secure, it is important to continuously monitor the network and look for changes that disturb the security equilibrium. Networks and control systems in particular are constantly evolving, with newer threats and vulnerabilities being discovered and exploited regularly. The networks themselves are expanding, adding more and more communication devices that bring their own security weaknesses with them. It is important that there is a system in place that keeps track of all the assets (or communicating devices) in the network and discovers in near-real-time any new device that can be a potential threat. This asset discovery should include devices that are both IP and non-IP communicating, such as serial devices. At a bare minimum, a proper audit mechanism that ensures compliance to an industry-specific standard (such as NERC CIP, NIST 800, IEC 62443, and so on) is what can help a control system remain secure and available at all times. For information on how to secure your organization’s industrial control systems with Tripwire and Belden, check out the video below. https://www.youtube.com/watch?v=BlfxKezWyOE About the Author: Divij Agarwal is a Senior Product Manager at Belden. He is responsible for product development and desiging for ICS Cybersecurity and firewalls.
Zero Trust and the Seven Tenets
Understand the principles of Zero Trust in cybersecurity with Tripwire's detailed guide. Ideal for both newcomers and seasoned professionals, this resource provides a practical pathway to implementing Zero Trust, enhancing your organization's security posture in the ever-evolving digital landscape.

