The summer of 2016 was a tumultuous ride for those of us in the security community. Less than a year ago, nobody had ever heard of The Shadow Brokers or Anna-Senpai but the same month (August 2016), these two – as yet unidentified persons or groups – made it clear that we are in the midst of a massive paradigm shift regarding threats to our society. Anna-Senpai’s release of Mirai source code and Shadow Brokers release of a trove of Windows exploits enabled massively disruptive attacks within months of their release. This posting will be devoted to the events leading up to last week’s WannaCrypt Ransomware attacks. As mentioned above, the Shadow Brokers came to prominence in August 2016, with a brief posting in which they advertised an auction of advanced cyber weapons claimed to have been stolen from “Equation Group.” (“Equation Group” is the name given by Kaspersky researchers to an unknown threat actor commonly believed to be the Tailored Access Operations (TAO) unit of the NSA.) This initial leak included a variety of exploits targeting networking hardware including a 0-day (titled EXTRABACON) and a persistent implant (JETPLOW) for various Cisco devices. The message and specifically the auction concept were met with great skepticism. A few weeks later, perhaps fueled by a general lack of attention, they leaked data about servers allegedly compromised by the NSA. This was followed by another posting a few weeks later containing screenshots allegedly showing the directory structure and limited contents of some of the files on the auction block. After a few months of silence (and very little activity on the Shadow Brokers bitcoin address), another release was made in early April. This time, it was a letter to US President Trump indicating that they had supported him and now feel abandoned. The statement (posted on Medium), was highly critical of Trump and acknowledged that their auction was a failure. The message ended with a password for the auction file describing its release as a form of protest. This password exposed a cache of somewhat disorganized Linux/Unix exploits mostly affecting rather old software versions. Just a week later, however, on April 14, 2017, the group released a far more dangerous set of tools for exploiting Windows systems, including reliable exploits for vulnerabilities fixed by Microsoft only one month prior.
The Shadow Brokers Most Damaging Release
This last release contained, among other things, FUZZBUNCH – an exploitation framework complete with numerous exploits, implants and a listening post for remotely accessing compromised hosts. I’ve spent a good bit of time exploring FUZZBUNCH and in my estimation, the tools are probably three to four years old based on the use of Python 2.6.x and the lack of reference to any Windows OS newer than Windows Server 2012 RTM. This is particularly interesting to me because if FUZZBUNCH is truly an unaltered NSA tool, this is evidence that 0-day exploits were in use for years without being publicly discovered. After a few hours working with the tool, it became clear that one exploit in particular, called ETERNALBLUE, stood out from the pack.
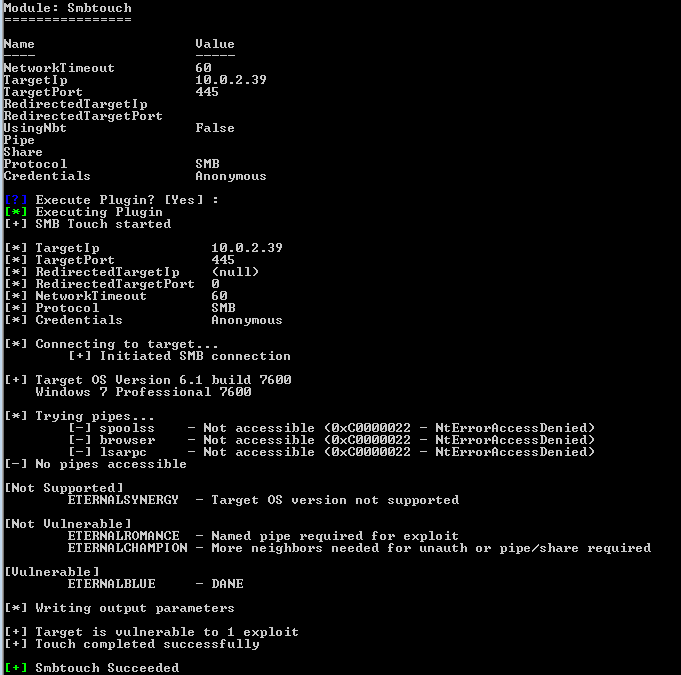
In my testing, this exploit proved to be extremely reliable for unauthenticated exploitation with the end result of giving arbitrary code execution within the Windows kernel. Specifically, ETERNALBLUE is designed to automatically implant a non-persistent backdoor into the target’s SMB stack. This backdoor, called DOUBLEPULSAR (DOPU), allows the operator to directly load kernel shellcode or to inject DLLs into usermode processes.
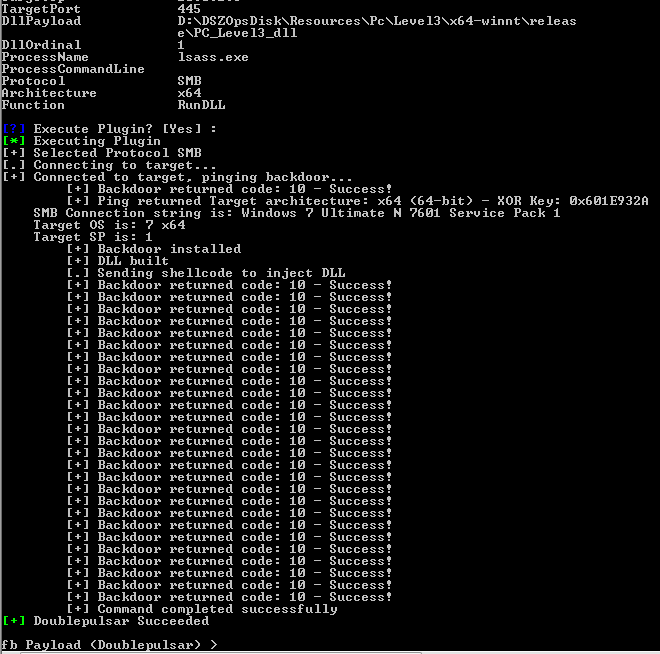
From this point, an NSA operator using these tools would likely use DOPU to deploy the PEDDLECHEAP payload, which is then connected to listening post (LP) software, such as the Java-based DanderSpritz tool included in the dump.
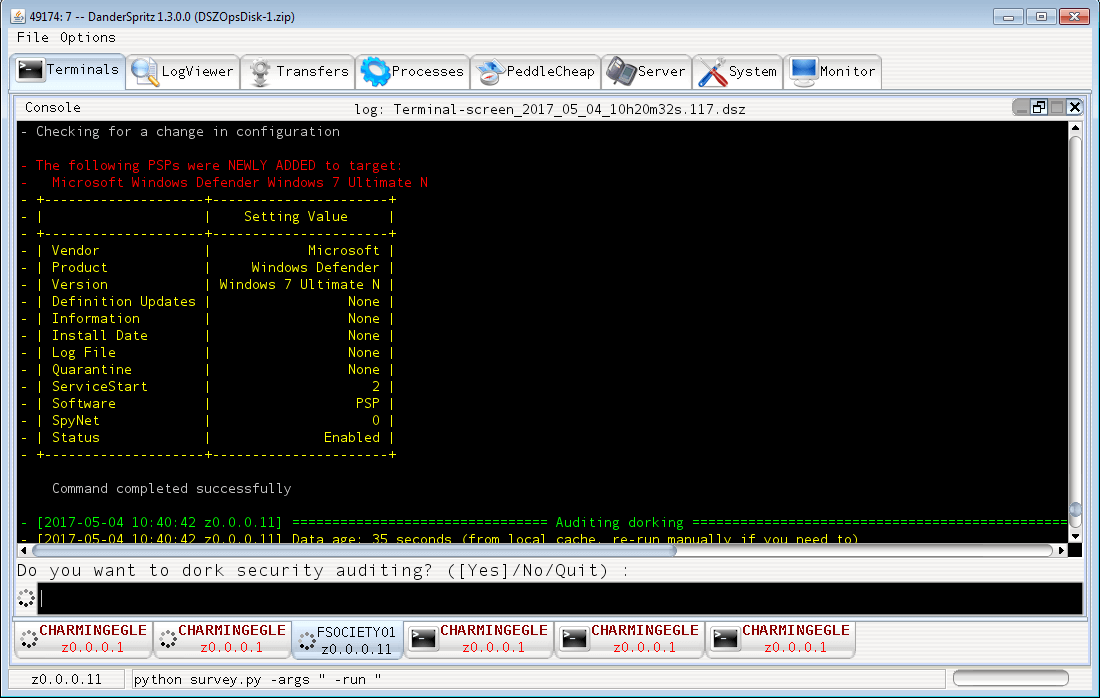
Unknown Attackers Leverage ETERNALBLUE For Ransomware
This is where the WannaCrypt ransomware attack comes into the picture. An unidentified individual or group saw the immense value of the ETERNALBLUE attack and set to work retasking this stealthy cyber weapon into a worm carrying a ransomware payload. The attack went live on Friday, May 12, apparently spreading through traditional worm techniques leveraging the many public IPs running SMB services. Once a server is compromised, the worm goes to work scanning for open SMB on the local subnet. The worm would then use ETERNALBLUE and DOUBLEPULSAR to load the WannaCrypt ransomware onto compromised hosts. Once installed, the ransomware would, in classic fashion, encrypt user data and display a message demanding the equivalent of $300 in bitcoin to recover the data. The ransom note instructed users that after three days, the ransom would double and after seven days, the data would be irrevocably destroyed. In the days following the attack, malware researchers began reporting connections between the code used in this attack and other attacks, which had previously been attributed to North Korean hackers. This may be evidence of North Korean involvement or it may simply be a false flag intended to give this impression. The worm propagated very quickly leaving a trail of destruction in its wake. Researchers have identified successful attacks in at least 150 countries with hundreds of thousands of computers locked. The considerable significance of this attack was already becoming clear in the early hours of Friday as reports came in that dozens of hospitals throughout the UK were finding themselves locked out of patient records. Operations had to be rescheduled and some number of patients had to be diverted to other hospitals. Fortunately, before the day was done, a malware researcher stumbled onto a kill-switch for the worm. This lucky break is likely what stopped the malware from spreading through North America with the devastating speed that was seen in Europe and Asia. By Monday, this researcher had been awarded a $10,000 bounty by HackerOne for their role in saving the day. It is important to note, however, that it would be trivial for anyone to restart the new campaign and, this time, without the kill-switch.
Staying Safe
If nothing else, the events of the last week are a clear demonstration that too many organizations fail to implement the security best practices preached by Tripwire and others in the industry. Patches protecting against ETERNALBLUE and other exploits were available from Microsoft two months before the launch of WannaCry for all supported Windows versions. (It’s also interesting to note that while patches were not publicly available for the 14-year-old and now unsupported Windows 2003 and XP operating systems, Microsoft had, in fact, authored patches for these OS around the same time as the MS17-010 fixes for other systems.) The top of every security professional’s priority list should be applying patches quickly and comprehensively. (This also, of course, means not running deprecated OS like Windows XP or 2003.) Based on numerous analyses of real-world attacks, the use of 0-day is, by all accounts, rare, so staying up-to-date with security patches does, in fact, mitigate the vast majority of exploit-based attacks. Interestingly, a two-year-old study from Google found that among security experts, the top security practice was to install software updates whereas non-experts thought the most important thing was to run antivirus software. Ironically, installing software updates wasn’t on the non-expert list and running antivirus wasn’t on the top responses from security experts. Another important takeaway from this attack is that far too many organizations have SMB services (TCP 445 and/or TCP 139) exposed on public IP addresses. I cannot figure out why a network administrator would intentionally expose this service to the Internet. VPN should be deployed in any situation where there is a need for external access to SMB. The elephant in the room on this topic, of course, is SMBv1. Although it is an ancient protocol which lacks important security features and was officially deprecated nearly four years ago, it is still enabled by default all the way up to Windows 10 and Server 2016. The current version (SMBv3.1.1) was announced two years ago and introduced with Windows 10 and Server 2016. A good Windows security policy should include disabling SMBv1 as outlined here.
Summing Things Up
A quick recap of these safety tips is as follows:
- Install security patches as quickly as possible.
- Discontinue use of unsupported OS.
- Restrict access from the Internet to SMB and other non-public services.
- Disable SMBv1 throughout your networks.
If you want to learn more about how Tripwire's product suite can help your organization be prepared for similar attacks in the future, please watch this video: https://www.youtube.com/watch?v=plotp84p9o0 Alternatively, you can find out more about the malware's operation and how you can prevent a similar attack here.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

