
It's been a busy inaugural year for Locky. Security researchers first spotted the crypto-ransomware in February 2016. That same month, it made a name for itself when attackers used it to infect the IT systems at the Hollywood Presbyterian Medical Center. The Californian hospital ultimately decided to pay the ransom demand of 40 Bitcoins (approximately 17,000 USD) after suspending its computer systems for a week. Locky has evolved considerably since its initial discovery. At least five iterations emerged prior to December 2016: ".zepto," ".odin," ".shit," ".thor," and ".aesir." Each new version primarily relied on spam mail for distribution. Morten Kjaersgaard, CEO of Heimdal Security, says the ransomware kept up that same attack vector in November… with a twist:
"What we’ve seen this month is a cluster of large spam campaigns delivering Locky. What’s especially intriguing in this case is how the cybercriminals behind the campaigns are testing new distribution channels… and different social engineering angles (such as using images to deliver the ransomware). The clear objective is to increase their chances for successful ransomware infections by spreading across untapped channels."
But Locky isn't just trying out new distribution channels. It's also seeking to maximize the damage dealt to each victim by partnering with malware that enlists victims into a botnet. Heimdal has detected one such campaign.
First Comes Encryption, Then Comes the Botnet
In the latest offensive, Locky's developers are sending millions of pieces of spam to employees at various companies located all over the world. Each spam message comes with a subject line that tries to trick the recipient into opening the attached .vbs (Visual Basic Script) file.
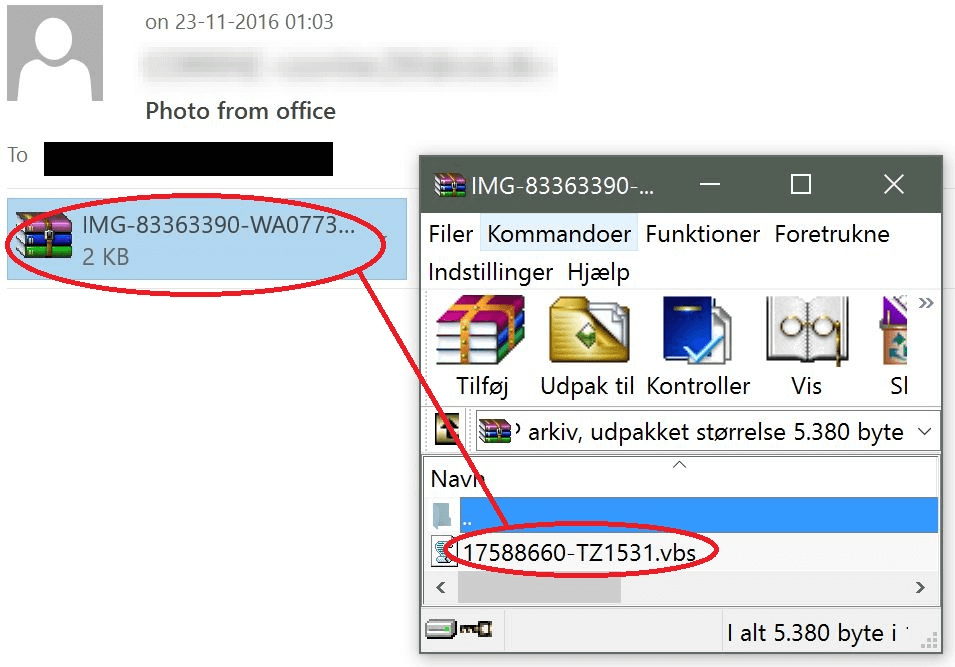
Source: Heimdal Security When clicked, the file fetches Locky in obfuscated form to avoid detection. It retrieves the ransomware from http://palsiraj [.] org, http://mvp-sp11 [.] ru, or several other compromised websites. The file then decodes Locky locally and runs it. A Locky ransomware infection is enough to ruin anyone's day. But this attack campaign doesn't end there. Heimdal's security evangelist Andra Zaharia explains:
"The encrypting malware then goes on to connect to a number of hard-coded IP addresses whose purpose is to enroll the affected computer into a botnet."
Short of that, it will fall back on its domain generating algorithm (DGA) to get the job done.
Conclusion
In Kjaersgaard's mind, these Locky attacks demonstrate that bad actors still prefer spam mail as a distribution vector for ransomware:
"Many users might still wonder if these indiscriminate spam campaigns still work, because they might seem outdated. But the truth is that Internet users still fall prey to curiosity and still open spam emails and click on links and download malicious attachments. Social engineering is deeply tied to human nature and our reflex to trust, which is why these tactics still work and will continue to do so."
Researchers have yet to crack Locky as of this writing. With that in mind, it's important that users back up their data regularly and implement some additional ransomware prevention tips. They can also learn more about ransomware in general here.

