Over the past few years, I have spent quite a bit of time trying to figure out a way to monitor what is happening on my home network in the same way that I have grown accustomed to doing so in an enterprise environment. Not happy with what was available on the market, I chose to start building my own solution. Back in 2015, I released the first set of scripts on putting together some tools that could be installed on a Raspberry Pi. Then in 2016, I dug into what was actually needed to bring these tools together. I still wasn’t happy with what I was giving out to people. There were too many moving parts, and it required too much intimate knowledge to get any real value out of it. Therefore, I began to revamp how everything was brought together and how it was managed. Ultimately, I stripped out some of the tools I never really seemed to use, while adding in others that gave me more control over the environment. Next week at Black Hat Arsenal, I will be officially releasing Sweet Security version 2.0. This version is a major update that includes the latest versions of Bro (2.5.1) and the ELK stack (5.5.0). The updated Python-based installer will now guide users through the entire installation process and configure everything for them. Here are some of the more exciting updates that are now available.
Modularized Installation
Installation can now be separated between web admin or sensor-only install. The Raspberry Pi has two main resource constraints when it comes to running Sweet Security. The first is memory – only having 1 GB of available memory limits what can be run on the Pi. Fortunately, what’s required for the client side processing will run just fine, as will what’s required for the web admin only processing. Splitting them up allows users to install on two Pi’s or perhaps using the sensor on a Pi with the web admin in a cloud service provider like AWS, so you can have control on-the-go.
The second constraint is the network card. Currently, the Raspberry Pi Model 3 only has a 100MB network card. Pushing it to the limit will still only garner about 80MB of throughput, which can be a limiting factor for those of us with a larger pipe from the ISP. Part of my work in splitting the installer out was giving it the ability to be architecture agnostic. Now the installer will run not only on ARM-based Raspberry Pi devices but on x86 devices, as well. If you have an old desktop sitting around collecting dust from 10 years ago, it’s probably more than powerful enough to run Sweet Security.
Plug and Play Deployment
One of the limiting aspects for people who tried to deploy version 1 was getting traffic to flow through the device. I left it up to the end-user to try and get the Pi in-line, set up some type of mirroring port, or reconfigure their networks to get traffic to flow through. Version 2 will now ARP spoof devices to get traffic to flow through the device. By going this route, you aren’t required to make any complex network changes or replace any equipment. Additionally, should the device fail for any reason, the network will still remain operational.
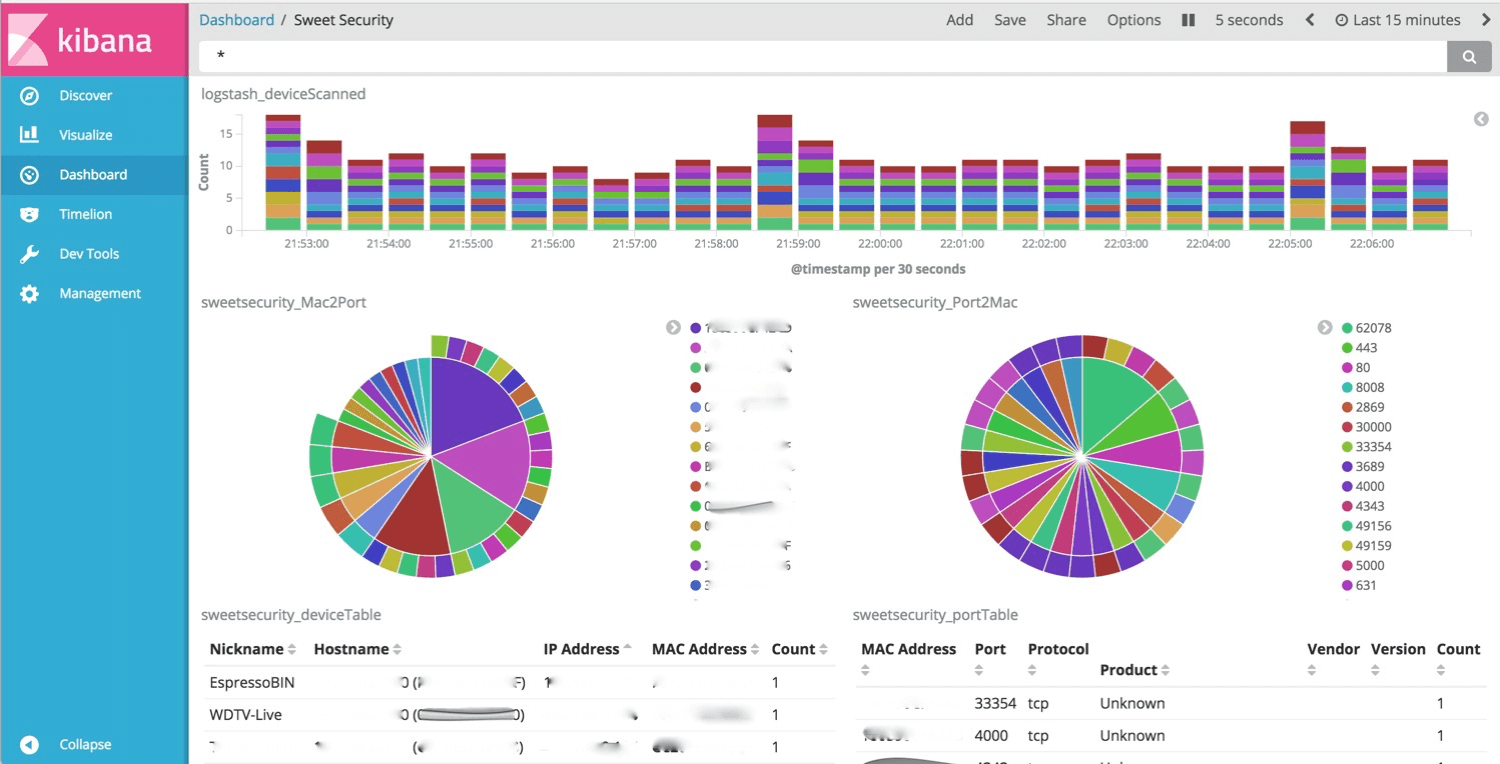
Major Logstash/Kibana Updates
The big update for Logstash is that all Bro logs are now normalized by the out-of-the-box configuration. In version 1, only the notice log was normalized, leaving the user to try and write their own rules. The configuration file was also optimized to use fewer resources, making everything run a bit smoother on smaller Pi-like devices. For Kibana, the biggest request was always, “Where are your dashboards?” Not only are the dashboard files uploaded to the GitHub repo but also imported automatically upon installation. I plan on uploading many more dashboards as time goes on, so I would love feedback on the type of dashboards you are using to find interesting things.
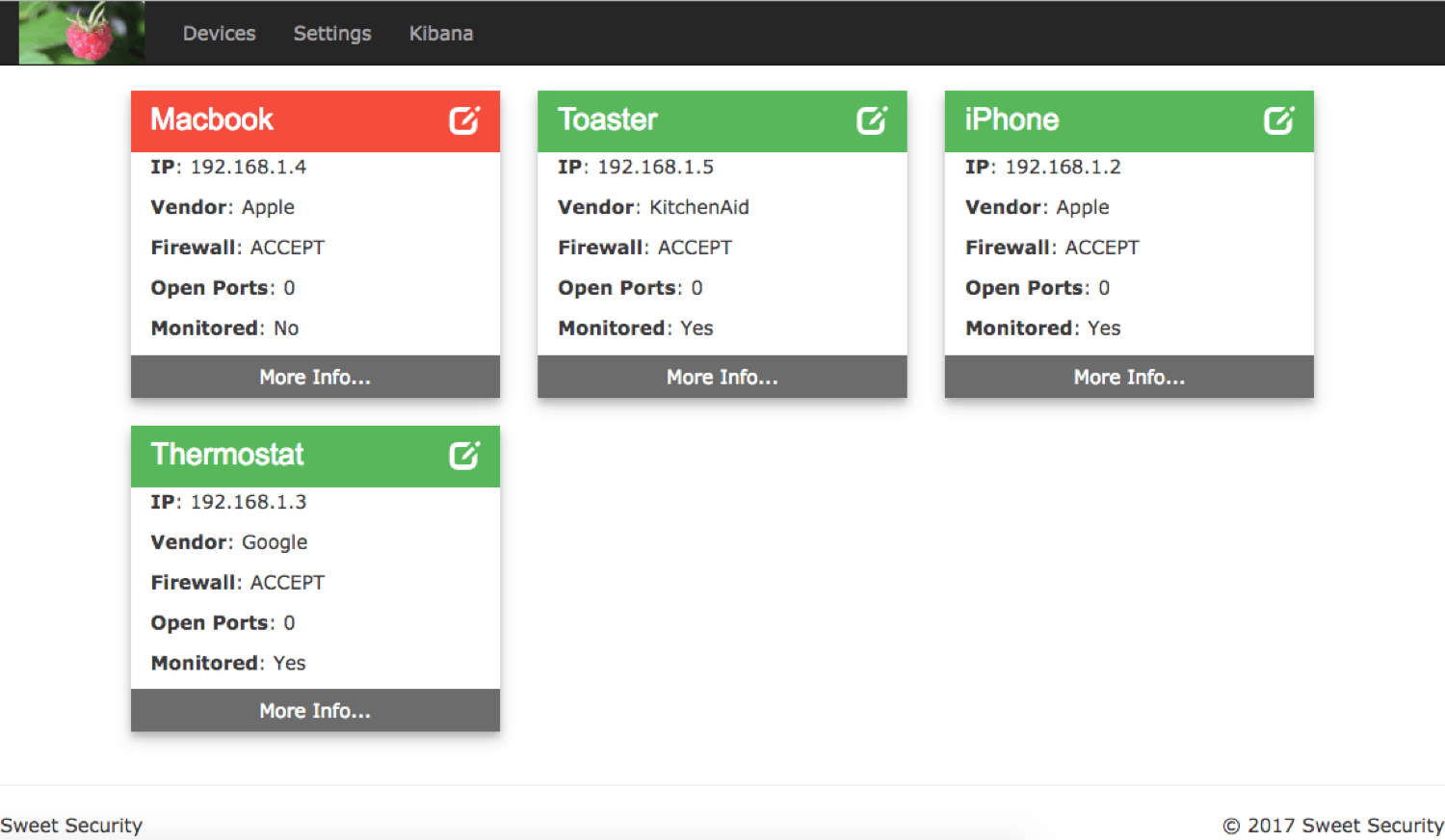
Web Administration Portal
Last but not least is the introduction of the web admin portal. Based on Flask, the portal gives insight into what is happening from the Sweet Security perspective. Logging in gives you a quick glance of all of the devices discovered on the network. Digging into each device allows you to control which is monitored (ARP Spoofed) by the sensor, give them friendly names, see what ports are open, and control their network traffic. The web admin portal sends down firewall configuration to the sensors on a routine basis. It’s now easy to create a managed firewall for individual devices or even isolate them from other local network devices entirely.
There are so many updates that it would take more than a single blog to outline them all. I look forward to being at Arsenal this year to discuss Sweet Security with all of you. You can find me on Wednesday, July 26th at 4 PM in the Business Hall (Level 2) talking about Sweet Security.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

