
If your doctor walks into the exam room for your annual physical and listens to your heart, takes a quick look at your throat, and then gives a clean bill of health without asking many questions, a quick interaction might make you feel good if you’re not worried about your health. However, if you haven’t been feeling well, or if you are at risk for chronic disease, this superficial approach could make you feel very uneasy. Unfortunately, enterprise security teams responsible for vulnerability management scans often accept the equivalent of a cursory diagnosis from their vulnerability management scans because it’s difficult to do the deeper set of diagnostics that provides real insight.
Credentialed vs. Non-Credentialed Vulnerability Assessment
Most vulnerability management solutions offer two kinds of vulnerability assessments: credentialed and non-credentialed (also known as authenticated and unauthenticated scans). Non-credentialed scans are very useful tools that provide a quick view of vulnerabilities by only looking at network services exposed by the host. Non-credentialed scans are very useful tools that provide a quick view of vulnerabilities by only looking at network services exposed by the host. Unfortunately, these scans can’t provide deeper insight into application and operating system vulnerabilities not exposed to the network, or those vulnerabilities that are potentially covered up by a firewall that sits between the scanner and the host. This could provide false hope that your system is safe, while in reality, those vulnerabilities are frequently targeted by attackers that have gained credentialed access, so they aren’t an accurate indicator of security risk.
Credential Challenges for a Vulnerability Assessment
One of the biggest reasons that security teams have a hard time completing credentialed scans is that maintaining an accurate list of credentials can be the equivalent of pulling teeth. In large organizations, it’s not always clear who owns specific assets, and even when the owner is clear, asking the asset owner for their credentials can be tricky business since many asset owners aren’t comfortable sharing this information. It may even be prohibited by company policy. For the sake of discussion, let’s fast forward to after the security team has invested the large chunk of time and resources required to put together a comprehensive list of credentials for targeted scans. Once they have that list, they still have to deal with expired or changed passwords, typos, access limitations and administrative privilege issues.
Credential Testing
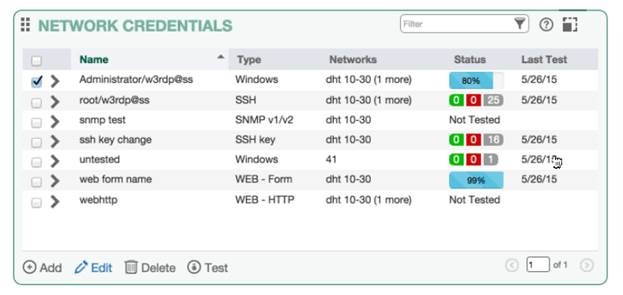
Fortunately, these are solutions that can help quickly diagnose and “treat” credential problems making it possible for security teams to get the critical vulnerability data necessary for an accurate representation of network security risk. A credential test dry-runs the credentials and then reports back which hosts were successfully authenticated and which were not. This allows security teams to quickly identify and resolve credential issues before performing vulnerability assessments that may encounter errors or provide inaccurate or incomplete information due to incorrectly configured credentials. Credentialed testing can help provide more accurate vulnerability assessment information, and credentialed testing can help solve problems related to credentialed assessment to help you assess more deeply into and across your networks. Interested in learning more about how credential tests work? Request a demo of Tripwire IP360. Title image courtesy of ShutterStock
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

