
419 scams are one of the oldest and most common tricks used by fraudsters to extort money from online users. These schemes promise victims a large sum of money in exchange for a small upfront payment. In this sense, ploys, such as the Nigerian Prince scam, resemble social engineering attacks to the extent that they rely less on the expertise of the attacker and more on the weaknesses inherent in the human psychology of the intended victims. However, a group of Nigerian scammers is defying this stereotype. Rather than exploiting people's desire to make money without too great of effort, these fraudsters are using the Microsoft Word Intruder exploit kit to deliver keyloggers to their victims, malicious programs which, in turn, provide the foundation for payment diversion schemes. The group's activities are best understood when divided into the following four categories: culture, campaign, compromise, and "cha-ching."
Culture
American-based network security company FireEye has published a thorough report on the malfeasances of this particular group. Authors Eyre Hernandez, Daniel Regalado and Nart Villeneuve explain that the technical expertise of the members varies. Even so, the scammers do share techniques and tools with one another, including lists of compromised email accounts, malicious documents and binaries, and Vip72, which provides a VPN and SOCKS proxy that enables the scammers to conceal their IP addresses when logging into a victim's account.
Campaigns
To select their victims, the group of fraudsters peruses sites such as Alibaba in an effort to identify potential victims who reside in countries in which they already have existing bank accounts. An ideal target is one who lives in Asia and who is not a native speaker of the English language, with the latter condition meant to ensure that grammatical errors on the part of the scammers will not raise too many red flags with their victims. The scammers also tend to target users who have registered accounts with free email providers, such as Yahoo!, Google and Hotmail. This tactic is motivated by the attackers' assumption that people who use free email accounts are not tech savvy, the authors explain, and/or that they might be a small business. A malicious document attached to a business inquiry succeeds in compromising these targets in most situations. Once a victim has been chosen, the fraudsters must figure out a way to deliver to them remote access tools (RATs) and other exploits. To overcome its unequal distribution of skills, the group often relies on third parties to develop, sell, and even protect malicious software on their behalf.
"The scammers are… concerned about their malware being 'Fully UnDetectable' (FUD)…. Additional layers of protection, like encryption, are used to prevent exploits from being detected," explain the authors. "…Aside from encoding or encrypting their exploits, they [malicious service providers] also run them through underground antivirus scanners to verify detection rates and ensure that their tools will bypass AV detections on their victims' computers."
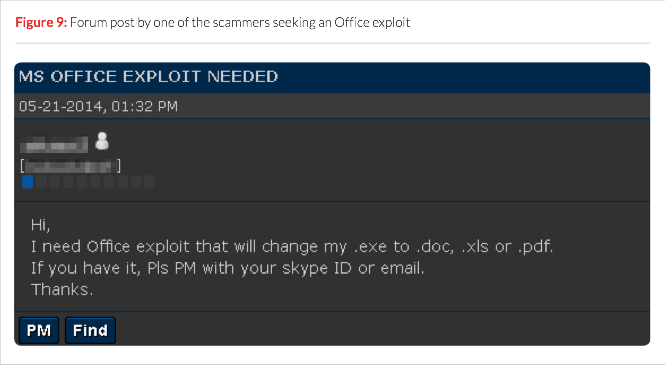
Source: FireEye
Among the tools developed by third parties and sold to the scammers include Microsoft Word Intruder (MWI), which is used to install malware on the victims' computer. The HawkEye and KeyBase keyloggers are just two software delivered by these fraudsters via the use of MWI and with the help of email extractors, bulk mailing providers, VPNs, and email notifiers.
Compromise
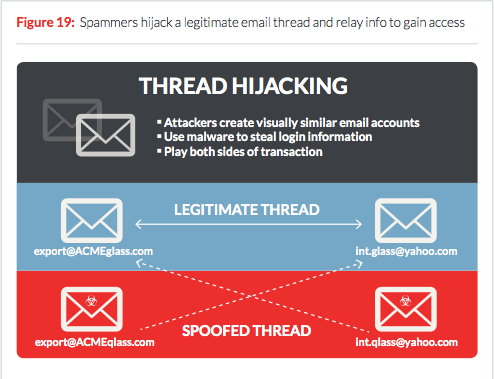
Armed with the multitude of tools described above, the scammers at this point scan their victims for evidence of monetary transactions, such as new purchases or refunds. If they spot such a payment, they log on to the victim's account and at that point execute a man-in-the-middle attack (MitM). This is done via the use of homograph "spoofing" techniques in which the attackers purchase domains and create emails that are similar to the victim and their correspondent. In some cases, the emails may differ by only one letter.
"Since the thread was legitimately established before the scammer hijacked it and the scammer copies the names and signatures of the original emails, both parties seldom realize that they are dealing with the scammer," FireEye explains. "The only difference is the spoofed email address, which would be hard to spot if the victim is not paying close attention."
Using these fake emails, they are able to inject their own content into the discussion and mislead both the buyer and seller of a financial transaction.
Source: FireEye
"Cha-Ching"
All scammers want one thing: money. This group of Nigerian fraudsters is no different. Once they have inserted themselves into an otherwise legitimate payment transaction, they begin forwarding fake invoices and product inquiries to the buyers and sellers, respectively. They also send updated payment instructions to the buyer and will follow up to make sure the transaction has been processed.
"Occasionally, the victim is reluctant to change the banking information as instructed, so the scammer must adapt and pressure the victim into sending the money," the authors have observed. "The scammer can use the information gleaned from the captured conversations and transactions to aide in convincing their victim."
In most cases observed by FireEye, money mules that have some relationship with the scammers receive the funds in their bank accounts. Depending on the size of the receipt, they may launder the money by purchasing luxury items or by mixing it with monies acquired legitimately.
Conclusion
As with phishing and social engineering attacks, avoiding a payment diversion scam hinges on an individual's ability to pay attention to the details. This includes watching for sudden changes in the minutia of a business deal, including the names and email addresses on transaction records. Also, it does not hurt to contact the other party directly when finalizing a transaction to make sure it has been processed correctly. Title image courtesy of ShutterStock
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

