
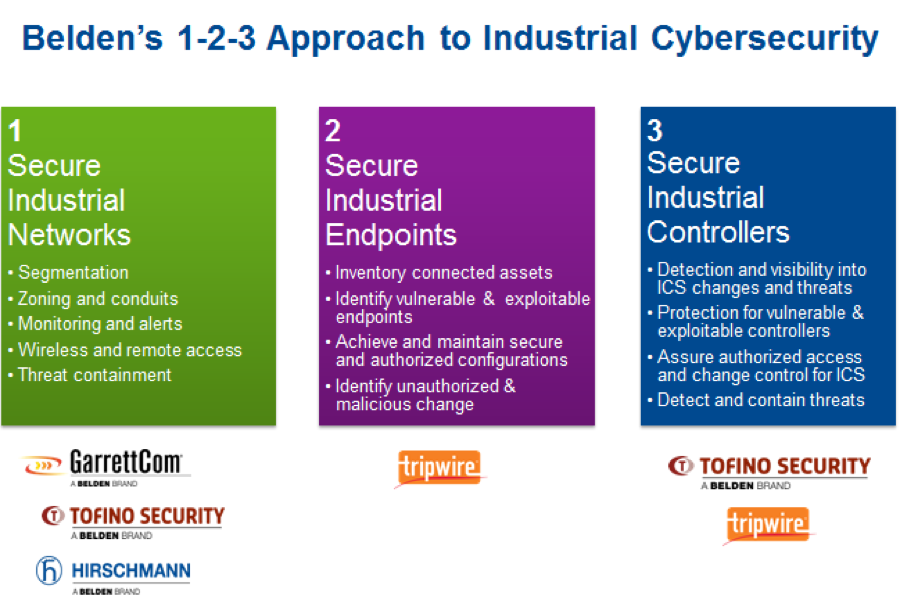
In a previous blog post, ICS: Next Frontier For Cyber Attacks blog, I spoke about the cybersecurity posture of industrial control systems (ICS) and the enormous implications for such attacks. For industrial organizations, it means downtime and lost business. For individuals, it means potential safety issues and lost services. For society, it means significant safety issues and productivity loss. Research from ICS-CERT, SANS, FireEye and others points to unhealthy cybersecurity postures for ICS environments, including many endpoint protection concerns. For example, computer assets (endpoints) are considered the highest risk in ICS-based organizations and only 50 percent scan for vulnerabilities on an endpoint (SANS 2016). This blog is the second part of a series on industrial cybersecurity approaches and aims to address the importance of securing all endpoints in an industrial organization to mitigate negative impact. Tripwire's parent company Belden provides a useful approach to industrial cybersecurity: the Belden 1-2-3 approach. At the same time, Tripwire protects and defends your industrial networks, PCs, critical endpoints and industrial controllers while maintaining high availability, reliable delivery and operational resilience.
Endpoints: OT & IT
Let's consider the mindsets of the two main bodies within an industrial company’s infrastructure, Informational Technology (IT) and ICS Operational Technology (OT), and how they view endpoints. IT is focused on the corporate side – typically Levels 4 and 5 (Purdue Model). These are business information and transactional systems commonly managed by the Chief Information Officer (CIO). IT endpoints are IP-based desktops, laptops, mobile devices, databases, application servers web servers, and often supply chains for contracts, order entry and accounting interactions. IT endpoints are highly dynamic with frequent updates and new additions connected with the internet and on the intranet. Given this dynamic environment, IT professionals are generally concerned with security for their IT assets, that is, the endpoints and access to those endpoints given the range of attack vectors here. ICS Operations (OT) systems also involve endpoints – many in a similar category. There are application servers, database servers, manufacturing systems, asset management, Human Machine Interface systems (HMIs), engineering workstations and, of course, Level 2 control systems. Every one of these systems has an OS, configuration/setup files, typically password-enabled access, and other factors. OT professionals are generally not especially concerned about security as they have specialized environments, protocols, communication channels, and proprietary hardware.
The Great IT A-Ha Moment
I was recently at a conference where the focus was on OT & production systems. I was surprised to run into some IT security managers. When I asked them why they were at the conference, they indicated they needed to know more about these production systems because, ultimately, they would be responsible for their security. This aligns with their priorities versus those of an OT organization. OT’s focus is on control, monitoring processes and equipment in plant environments. Engineering and operational management typically manages them. Safety is the priority, closely followed by availability within industrial control environments. IT security values confidentiality as the top priority within the IT enterprise environment. OT includes an array of control systems, including:
- Programmable logic controllers (PLCs)
- Remote Terminal Units (RTUs)
- Intelligent Electronic Devices (IEDs)
- Distributed Control Systems (DCS)
- Supervisory control and data acquisition (SCADA)
- Human machines interfaces (HMI)
- Digital to analog converters (DAC)
In general, OT systems do not reside in a highly dynamic environment like IT. OT endpoints are for the most part, untouched legacy systems with specialized communication protocols and possibly air-gapped from the outside world. The reality is the endpoints in an OT environment are increasingly connected to the outside world. As a matter fact, a lot of the HMI endpoints are PC-based with an Internet connection, which introduces a nice attack vector. And another attack vector, as noted well in the ICS SANS 2016 survey, is the connection from IT to OT, which is a top concern. Imagine if IT endpoint malware found its way over to the OT environment. The reality is their worlds are converging with connectivity for the gains in higher efficiency. This, unfortunately, also brings greater risk to the OT environment. Bottom line: To mitigate OT attacks, PC-based endpoints in the OT environment need to be protected, and organizations need to ensure that IT endpoints are protected to avoid attacks that traverse over to the OT environment. An overarching endpoint security strategy needs to be in place for OT and IT environments.
OT & IT: Consider Endpoint Security Misconceptions
Let’s consider the vast range of endpoint security misconceptions that can lead us to great pains. "Anti-virus (AV) is just fine." While AV offers some level of endpoint protection, it requires regular signature updates and scheduled scans. Signature-based protection does not catch all attackers, and it is not appropriate for all endpoints. "Not all endpoints require protection." It’s a false sense of protection. Increasingly, endpoints are becoming connected or plugged in (like a USB drive), which constitutes an attack vector. "Endpoint protection can operate on its own." Security insight from both the endpoint and the network is required for a sophisticated attack. Understanding the source of the attack downstream, whether it is the network or email link, is critical to remediation. "Users operate most endpoints in a safe manner." The Human Attack Vector is one of the largest, and OT environments often times don’t consider the effects of operator error, social networking, and poor policy as influenced when an end user is involved. Endpoint protection must include user training on cybersecurity. Human error, whether inadvertently caused or through malicious intent, is a major source of attack vectors. "My endpoint connections to the internet are safe." Not in all cases, many older protocols to secure the connection have vulnerabilities. "Endpoint security ruins my user experience." Most endpoint security has evolved to minimize any performance issues. On the flip-side, what if your endpoint gets infected? It will more likely see some performance issues as a result of being infected. "Endpoint protection is the panacea." A comprehensive and integrated approach that considers the network and the endpoint will address most attacks effectively This is Tripwire’s philosophy for securing endpoints. For industrial organizations, basic endpoint security hygiene is the foundation of your cybersecurity. This includes:
- Knowing your endpoints. Have an inventory of assets, hardware, software, firmware, virtual and physical assets, and also have visibility into their configurations, OS, protocols, and communications, as well as who has access to them, when and for what purposes. This essentially defines key areas most often involved when a breach occurs.
- Understand the existing and documented vulnerabilities for any of your assets and the risk associated with your particular environment. (It’s unfortunate that many attacks came from known vulnerabilities.)
- Attain and maintain secure and authorized configuration on each endpoint. If a configuration is tweaked on your endpoint without proper reason or authority, there is reason to at least investigate if not believe there could be foul play.
- Find and discover any unauthorized changes in as close to real-time as possible. This will help determine as early as possible what process and policy failures may be present at best and potential malicious behavior at worst.
Part 3 of this blog series will speak to Belden and Tripwire securing the ICS environment directly without disruption.
Zero Trust and the Seven Tenets
Understand the principles of Zero Trust in cybersecurity with Tripwire's detailed guide. Ideal for both newcomers and seasoned professionals, this resource provides a practical pathway to implementing Zero Trust, enhancing your organization's security posture in the ever-evolving digital landscape.

