
Arguably, the first malware extortion attack occurred in 1988 – the AIDS Trojan had the potential to be the first example of ransomware, but due to a design flaw, the victims didn’t end up actually having to pay up the 189 bucks. It’s safe to say that over the past 31 years, attackers have perfected the ransomware craft, with organizations shelling out more than $25 billion per year. We don’t expect it to end any time soon.

We’ve even seen the ransoms increased by as much as 2X this year alone. All this is evidenced by the recent activity on the Tripwire State of Security blog since the first of the year:
- “PwndLocker” Ransomware, March 2020
- “Nemty” Ramsomware, February 2020
- “DoppelPaymer” Ransomware, February 2020
- Ransomware Attack at Natural Gas Compression Facility, February 2020
- “Ransomwared” Ransomware, February 2020
- University pays 30 million, February, 2020
- “Emotet” Trojan, enabling ransomware, February 2020
- “WannaCry” continued fallout at NHS, January 2020
- “Ryuk” Ransomware, January 2020
- “Ako” Ransomware, January 2020
- “SNAKE” Ransomware, January 2020
- Marketing company detrimentally affected by Ransomware, January 2020
Ransomware in Industrial Control Systems
Now that we’ve established that ransomware is running wild in enterprise networks, it’s important to establish the fact that the threat isn’t just present in the office and datacenter setting; malware is making its way into ICS networks due to the fact that we are seeing increased connectivity of these once-disparate networks. Even if you aren’t an asset owner in the manufacturing, petrochemical, transportation or energy verticals, there’s a good chance you have industrial control systems in your environment. (Think building automation control systems like HVAC, elevators, backup generators and a myriad of other electrical control systems.) Whether it’s intentional or not, ransomware perpetrators have declared war on control networks. These include several specific cases like Norsk Hydro, the above-mentioned instance at a Natural Gas Compression Facility and an event at EVRAZ steel in North America caused a plant shutdown and according to some sources resulted in temporary layoffs. The moral of the story here is this: don’t forget to implement ransomware prevention steps on IT-like systems (Windows servers and workstations) that exist either in your industrial networks (such as HMIs, engineering workstations, etc.) or that have access to industrial networks (such as historians, MES, exchange, active directory, remote access servers, etc.).
Use Tripwire Enterprise to verify your configurations

You, yes you, can help to win this war on ransomware. As a Tripwire Enterprise customer, you have a unique advantage to ensure that your systems are hardened to help prevent the spread of ransomware. To make it even easier, our folks at VERT (Vulnerability and Exposure Research Team) and our field security engineering team have developed a Tripwire Enterprise Content Pack consisting of Tripwire Enterprise Rules and Policies that can be used as one-stop-shop insight into the state of your enterprise hardening efforts to combat the spread of ransomware. The Rules and Policy tests that make up this content pack have been carefully curated by Tripwire from industry best practices with the aim to help you quickly identify Windows security configuration items that can be adjusted to improve your chances of combatting the spread of ransomware. The content evaluates the following components that can have a meaningful impact on your ability to defend your systems with foundational controls:
- AntiVirus/Malware Status
- Verify That Anti-Virus Software Is Installed
- Verify That Anti-virus Software Is Running Correctly
- AppLocker Enforcement
- AppLocker EXE Enforcement Mode: Enforcing Rules
- Validate That the 'AppIDSvcStatus' Is Running
- Validate That vssadmin.exe Is Denied by AppLocker
- Validate That wscript.exe Is Denied by AppLocker
- Backup Software Status
- Verify That Backup Agent Software Is Installed
- Verify That Backup Agent Software Is Running
- Credential Hardening
- Credential Protection
- Admin Approval Mode for the Built-in Administrator Account: Enabled
- Apply UAC Restrictions to Local Accounts on Network Logons: Enabled
- Run All Administrators in Admin Approval Mode: Enabled
- WDigest Authentication: Disabled
- Password Complexity
- Maximum Password Age Is Greater than 0 and Less than or Equal to 60
- Minimum Password Age Is Greater than or Equal to 1 Day
- Minimum Password Length Is Greater than or Equal to 14 Characters
- Password Complexity: Enabled
- Password History Memory Is Equal to 24
- Password Reversible Encryption: Disabled
- File Server Resource Manager (FSRM)
- FSRM Configuration
- FSRM File Group - Ransomware Extensions Configured
- FSRM File Screen - Exists
- FSRM File Screen Templates - Ransomware Blocking Exists
- FSRM File Screen Templates - Screening Type Active
- Windows Feature Installation
- FS-FileServer Installed
- FS-Resource-Manager Installed
- Hidden File Extensions
- User File Extensions Hidden is Disabled
- Operating System Updates
- Missing Patches: None Missing
- Powershell Settings
- PowerShell Script Execution Disabled
- Remote Desktop Protocol
- RemoteInteractiveLogonRight: Doesn't Contain Administrators
- Require User Authentication for Remote Connections by Using Network Level Authentication: Enabled
- Set Time Limit For Active Remote Desktop Services Sessions: Enabled
- Set Time Limit For Active but Idle Remote Desktop Services Sessions: Enabled
- Set Time Limit For Disconnected Sessions: Enabled
- Terminate Session When Time Limits Are Reached: Enabled
- SMBv1 Configuration
- Verify That the SMBv1 Protocol Is Disabled on SMB Client
- Verify That the SMBv1 Protocol Is Disabled on the SMB Server
- Windows Admin Shares
- Default share: Not Shared
- Remote Admin: Not Shared
- Remote IPC: Not Shared
- Server Service: Disabled
- Windows Defender
- Windows Firewall – Blacklisted Ports Blocked
- Windows Firewall - Enable Firewall
- Windows Firewall - Inbound: Blocked (Default)
- Windows Firewall - Log Dropped Packets: Enabled
- Windows Firewall - Log File Is Configured
- Windows Firewall - Log Size Is Equals Or Greater Than 16M
- Windows Firewall - Log Successful Connections: Enabled
- Controlled Folder Access: Enabled
- Windows Remote Management
- WinRM Service: Disabled
- FSRM Configuration
- Credential Protection
Get started today by visiting the Tripwire Customer Center, navigate to Product Downloads, then Content. You can easily locate the Malware Content Pack by filtering on “platform” and selecting in “Ransomware” as seen below.
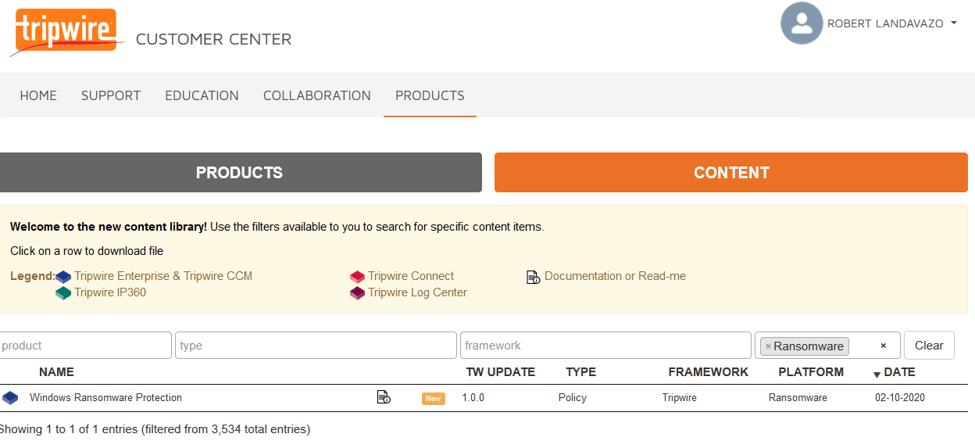
Download the “Windows Ransomware Protection” and import the XML into your Tripwire Enterprise Console. Don’t forget to scope the policy to the Windows assets in the environment you want to harden. If you have any questions, please contact your Tripwire Account Manager or Sales Engineer, and happy hunting hardening!

