
Researchers have uncovered an attack campaign that is using social engineering techniques in order to deliver remote access trojans (RATs) to SMBs located in India, the UK, and the United States. The Security Response team at Symantec provides an overview of the campaign, which began early last year, in a blog post:
"The attackers operate with few resources, rely on social engineering rather than exploits, and use two publicly available RATs−Backdoor.Breut and Trojan.Nancrat," the security firm explains. "However, despite these limitations, the attackers can gain a huge amount of control of victim computers thanks to the malware’s multi-purpose capabilities."
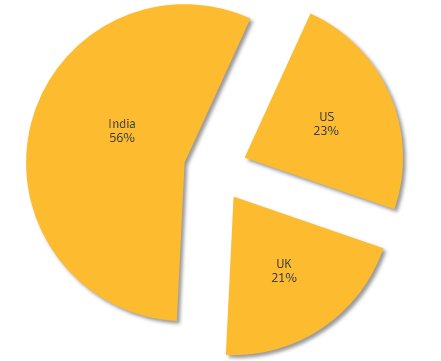
Infection activity in the top three targeted regions throughout 2015 (Source: Security Response)
Each compromise proceeds as follows. The attackers use stolen or spoofed accounts to send out emails to businesses based in different types of industries and sectors. Those emails generally contain a subject line, such as "Remittance Advice" or "PAYMENT REMITTANCE," that has been specially crafted in an attempt to lure employees with access to their business's financial accounts into opening the email.
All of the emails come with archive file attachments using ".zip" extensions. If a victim opens one of these files, either Backdoor.Breut or Trojan.Nancrat will infect their machines, thereby granting the attackers complete access of the target computer.
"Through these infections, the attackers can access the webcam and microphone, log keystrokes, steal files and passwords, and more," notes the Security Response team. "The attackers have been observed using the targeted employee’s privileged access to transfer money to an account under their control."
RATs, including those variants used to sextort children, demonstrate that attackers need not invest a large amount of resources in order to successfully infect a target machine.
With this in mind, users are urged to avoid opening up email attachments or clicking on links in suspicious email attachments, to avoid providing personal information in a web browser pop-up, and to maintain an up-to-date antivirus solution on their computers.

