
In its 2016 Breach Detection Study, Tripwire evaluated the confidence and efficacy of 763 information security professionals in implementing seven key security controls: PCI DSS, SOX, NERC CIP, MAS TRM, NIST 800-53, CIS Top 20 and IRS 1075. Those resources, which align with the United States Computer Emergency Readiness Team (US-CERT) recommendations and international guidance, must be in place for organizations to quickly detect a cyberattack in progress. That's because they provide crucial information about all endpoints, including an inventory of hardware updates. Tripwire found that a majority of IT personnel suffer from overconfidence in their ability to detect a data breach. For instance, while 60 percent of respondents said they were unsure exactly how long it would take automated tools to discover configuration changes in their organizations' endpoints or for vulnerability scanning systems to generate an alert, more than 70 percent of participants said it should take only minutes for those same solutions to detect an alteration.
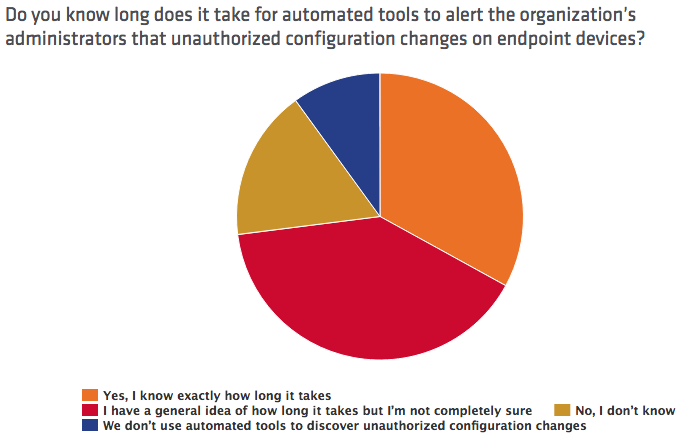
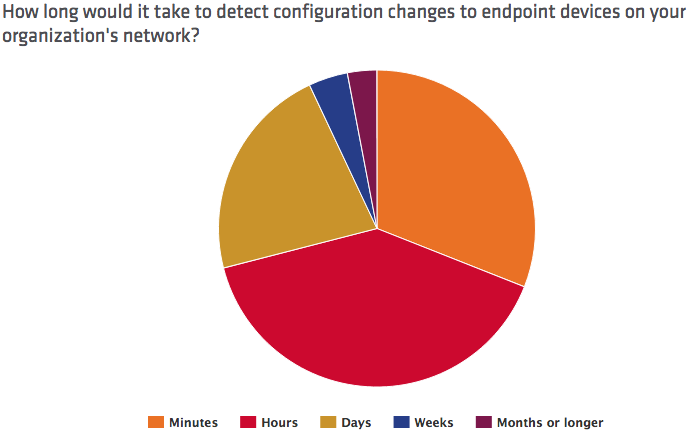
That figure's way off. As revealed by Mandiant’s M-Trends 2015 report and Verizon’s 2015 Data Breach Investigations Report, it usually takes weeks – if not months – for organizations to identify those modifications. Unfortunately, IT professionals' overconfidence didn't change when Tripwire broke down its survey by sector:
- 95 percent of respondents in the retail sector stated their organization could detect a breach within a month or less despite the fact that nearly half (48 percent) of participants said their breach detection products are just partially integrated.
- 87 percent of financial IT pros said they could remove an unauthorized device from the corporate network within minutes or hours. But almost as many respondents said they could automatically discover at most 80 percent of assets.
- A majority (78 percent) of respondents working in the federal government answered they could detect new network devices within hours, but 52 percent said they didn't know how long the detection process would actually take.
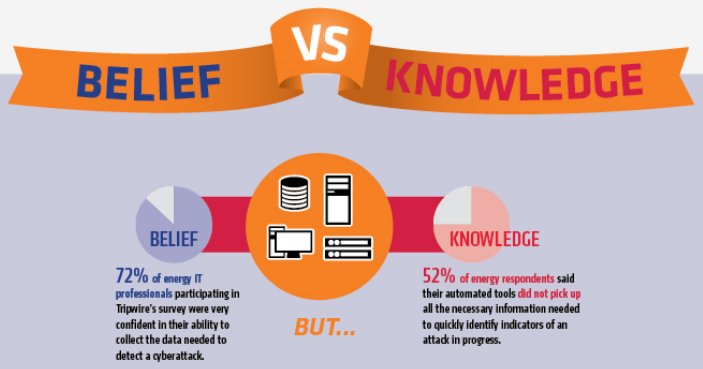
It's, therefore, no surprise that Tripwire observed high rates of overconfidence among respondents to its survey who work in the energy sector. For instance, 72 percent of energy respondents reported they could detect endpoint configuration changes within hours, but over half (52 percent) said their automated tools did not pick up all the necessary information.
Travis Smith, senior security research engineer for Tripwire, says those results reveal IT professionals are overestimating their efforts to secure their organization's systems:
"These results show that most security professionals are assuming they are doing the right things to secure their environments, but lack real world data to back up their assumptions. This highlights the importance of testing security controls to ensure they are functioning as expected. It’s not enough to install security tools throughout the environment. You must test the policies and procedures to be confident the controls in place will stop or detect real-world intrusions."
In fact, close to half of energy respondents lacked a basic understanding of how long it takes for them to detect unauthorized software, receive an alert from vulnerability scanning systems following a discovery, or get a notice that a system failed to log properly at 59 percent, 52 percent, and 40 percent, respectively. Even so, at least three-quarters of respondents said every one of those processes would take only hours. Additionally, 44 percent of energy sector respondents said less than 80 percent of patches succeed in a typical patch cycle. That makes Tim Erlin, director of IT security and risk strategist for Tripwire, feel IT professionals in the energy sector have a long way to go in securing their organization's environments:
"The energy sector has made significant improvements in securing their slice of the nation’s critical infrastructure, but broader adoption of security best practices is still lacking. While dedicated security staff is intimately familiar with the deployed capabilities and gaps, IT at large is often working on assumptions of protection."
For more information regarding Tripwire's 2016 Breach Detection Study, click here.
Achieving Resilience with NERC CIP
Explore the critical role of cybersecurity in protecting national Bulk Electric Systems. Tripwire's NERC CIP Solution Suite offers advanced tools for continuous monitoring and automation solutions, ensuring compliance with evolving standards and enhancing overall security resilience.
