
DocuSign is warning customers and users to be on the lookout for targeted emails containing malware after a data breach affected one of its systems. On 15 May, the provider of electronic signature technology disclosed the security incident in an update posted to its website:
"...[T]oday we confirmed that a malicious third party had gained temporary access to a separate, non-core system that allows us to communicate service-related announcements to users via email. A complete forensic analysis has confirmed that only email addresses were accessed; no names, physical addresses, passwords, social security numbers, credit card data or other information was accessed. No content or any customer documents sent through DocuSign’s eSignature system was accessed; and DocuSign’s core eSignature service, envelopes and customer documents and data remain secure."
It's a good thing the breach didn't affect customers' more sensitive information. But bad actors can still do a lot with stolen email addresses. Worst of all, they can abuse them to conduct secondary attacks. DocuSign has already detected one such follow-up campaign. The offensive begins when a customer receives what appears to be an email from DocuSign requesting their signature for an accounting invoice. There's just one problem: although it exhibits company branding, the email is a fake. In actuality, it's a means of spreading a malicious Word document that's capable of downloading banking malware onto a customer's machine.
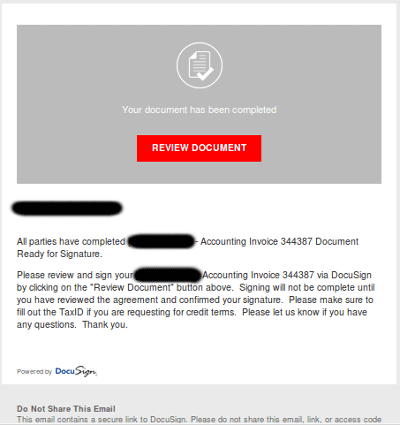
The fake DocuSign email. (Source: DocuSign) Word-based malware is no laughing matter. In April 2017, researchers spotted a campaign by which attackers sent out fake Delta Air Lines receipts. These emails contained malicious Word documents that downloaded Hancitor. This malware infected the compromised machine's system processes before contacting its command and control (C&C) server and retrieving Pony, a credential-stealer which can download other malware. To stay safe against these fake signature requests, DocuSign recommends that customers delete all emails that bear either of the following subject lines: "Completed: [domain name] – Wire transfer for recipient-name Document Ready for Signature" or "Completed [domain name/email address] – Accounting Invoice [Number] Document Ready for Signature". It also recommends that customers keep their anti-virus up-to-date, review tips on how to spot a phish, and forward all suspicious emails to [email protected].

