
Several high-profile attack campaigns targeting Middle Eastern companies have recently come to the attention of the security community. One of the first operations we heard about occurred on November 17, 2016, when Shamoon resurfaced and leveraged Disstrack malware to wipe the computers at an energy organization based in Saudi Arabia. Apparently, "Shamoon 2" was just getting started. Less than two weeks later, researchers detected another Shamoon 2 attack against a second Saudi Arabian energy organization. This campaign outfitted Disttrack with default credentials for Huawei’s virtualized desktop infrastructure (VDI), which could mean the wiper malware was configured specifically to hamper the target company's recovery efforts. Research by Symantec suggests the Shamoon group might have obtained those credentials from a digital espionage actor operating in the region. More than anyone else, energy organizations have felt the brunt of this latest wave of targeted campaigns. But they haven't been the only victims. Middle Eastern government agencies have also experienced their fair share of attacks. Most recently, researchers detected a threat actor targeting government entities in the region with the Downeks downloader and Quasar remote access trojan (RAT).
The Down-Low of Downeks and Quasar RAT
Researchers at Palo Alto Networks haven't identified the initial infection vector for this campaign. They do know, however, that the attack chain begins when a victim somehow receives an initial dropper (probably via email or the web). That dropper assumes the disguise "Joint Ministerial Council between the GCC and the EU Council.exe." GCC stands for many things. For the purposes of this campaign, it likely represents the Gulf Cooperation Council, an intergovernmental body of Arab states in the Persian Gulf. Correspondence of any sort between the GCC and the EU Council would be pertinent to the work of government officials in the Middle East. Attackers know this, which is why they've camouflaged their dropper with such a relevant disguise. Upon execution, the dropper extracts an embedded instance of the Downeks downloader with the file name "ati.exe." The downloader, which is technically a simple backdoor, oftentimes masquerades as icons, filenames, and metadata imitating legitimate applications such as VMWare. It communicates with its command and control (C&C) server via HTTP POST requests. By that channel, Downeks executes several actions, such as taking a screen shot, enumerating anti-virus solutions installed on the infected machine, achieving host persistence, terminating running processes, and sending information about the computer back to the attackers. The downloader also fetches a machine's external IP address to identify the victim location with GeoIP. All the while, it drops decoy documents for cover.
Quasar and Downeks. (Source: Palo Alto Networks) At some point, Downeks makes a POST request to dw.downloadtesting[.]com. This action leads to the installation of Quasar RAT, a .NET Framework-based open-source RAT. Quasar's C&C infrastructure remains separate from that of Downeks'. Even so, a single shared IP address connects the two malware samples. Downeks' infrastructure is also linked to DustySky, a campaign perpetrated by the Gaza cybergang against IT and IR staff in the Middle East.
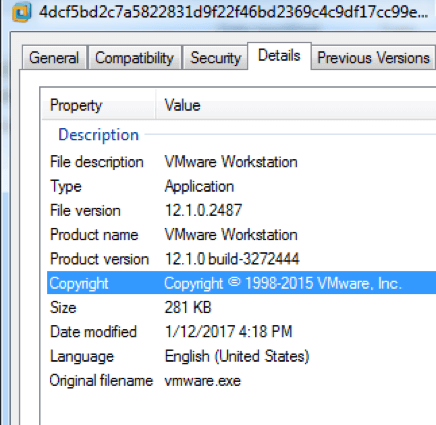
Application metadata masquerading as VMWare Workstation. (Source: Palo Alto Networks) An evolution of xRAT, Quasar can retrieve system information; upload, download, and execute files; edit the registry; shut down and restart the computer; open a remote desktop connection; issue remote clicks and keyboard strokes; steal passwords; and obtain Keylogger logs. But the malware is not perfect. A hole in the malware's C&C server could allow bad actors to get up to all kinds of trouble. Palo Alto Networks' researchers explain in a blog post:
"With further analysis of the Quasar RAT C2 Server, we uncovered vulnerabilities in the server code, which would allow remote code execution. This might allow a second attacker to install code of their choice – for example, their own Quasar RAT – on the original attacker’s server. We refer to this (somewhat ironic) technique as a 'Double Edged Sword Attack'. We did not apply this to any live C2 servers – we only tested this with our own servers in our lab."
Specifically, because the Quasar server does not verify the RAT data, an actor could supply convincing "victim data" in the way of a file of their choice. Palo Alto Networks' research team sent two files, including "dnsapi.dll," with the knowledge that Quasar is vulnerable to DLL hijacking. Once uploaded, their DLL file forces Quasar to connect to their own attack server, thereby allowing them to control the RAT's server with their own version of the malware.
Conclusion
Government agencies in the Middle East can defend against this campaign by blocking all associated C&C servers via the use of Threat Prevention DNS signatures. They should also leverage the Indicators of Compromise (IoC) for both Quasar and Downeks, which are available in Palo Alto Networks' blog post here.

