
Some digital threats are more serious than others but when it comes to unpatched software, nothing's worse than an exploit kit. These software packages come preprogrammed with the ability to exploit active security issues on vulnerable computers. If they find one such hole agape, they'll use their exploit code to download ransomware and other baddies onto your computer. Exploit kits come in many shapes and sizes. As a result, the security community sees exploit kit campaigns all the time. Case and point: Heimdal Security has detected a new attack campaign by which the RIG exploit kit is installing Cerber ransomware onto vulnerable machines.
Inside the Exploit Kit Campaign
The exploit kit campaign begins when a user visits a legitimate website. A malicious ad periodically displays on that site. When it does, it automatically redirects the user to one of 11 compromised websites. These domains, which employ the ".news" top-level domain (TLD) and which have low detection rates on Virus Total, are all victims of pseudo-Darkleech. Pseudo-Darkleech is a malware campaign that injects malicious code into core WordPress files and redirects users to a landing page for an exploit kit or a malware-downloader. These baddies then do their dirty work. Once they're finished, they install other malicious software, like Cerber ransomware and CrypMIC ransomware, onto victims' computers. In this campaign, pseudo-Darkleech redirects users to a landing page for RIG-E, the Empire Pack version of RIG that helped distribute CryptoLuck ransomware in November 2016. RIG-E then scans the computer for a total of eight vulnerabilities affecting Adobe Flash Player and Microsoft Silverlight, Internet Explorer, and Edge. All but one of those security flaws has a CVSS score of 7.5 and up.
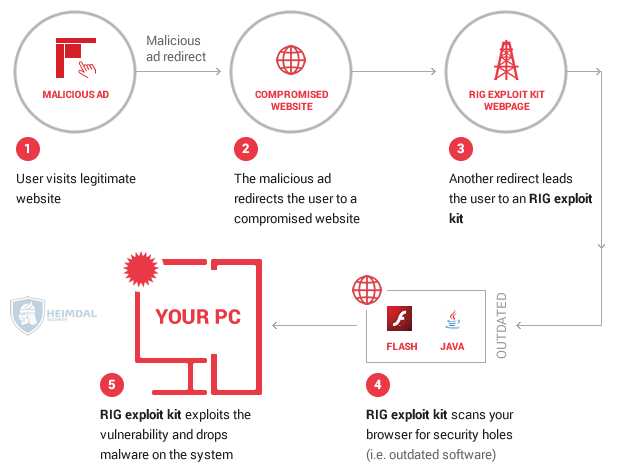
Source: Heimdal Security Take CVE-2016-0034, for instance. It's a denial-of-service (DoS) and code execution bug that affects Silverlight version 5.0. Its CVSS score is a 9.3. Microsoft patched the flaw back in January 2016. But that doesn't mean attackers can't still target it on vulnerable machines. Microsoft explains what could happen if a bad actor decided to abuse the issue. As quoted by Heimdal Security:
"In a web-browsing scenario, an attacker who successfully exploited this vulnerability could obtain the same permissions as the currently logged-on user. If a user is logged on with administrative user rights, an attacker could take complete control of the affected system. An attacker could then install programs; view, change, or delete data; or create new accounts with full user rights. Users whose accounts are configured to have fewer user rights on the system could be less impacted than users who operate with administrative user rights."
That vulnerability is bad enough on its own but if RIG-E detects it on a user's machine, it'll exploit it and download Cerber, the "ransomware that speaks," which has gone through at least five versions since researchers first discovered it in the spring of 2016. As of this writing, Cerber's author rakes in nearly one million dollars a year from the ransomware's affiliate scheme alone. That doesn't include any of the attack campaigns they launch on their own time.
Conclusion
Exploit kits like RIG-E are hoping users like you will ignore security updates. Don't give these malicious tools the satisfaction of compromising your computer or network. Instead, stay on top of the latest security flaws by developing a vulnerability management framework and implementing security patches as soon as they become available.
Mastering Security Configuration Management
Master Security Configuration Management with Tripwire's guide on best practices. This resource explores SCM's role in modern cybersecurity, reducing the attack surface, and achieving compliance with regulations. Gain practical insights for using SCM effectively in various environments.

