Health-ISAC recently released their 2025 Health Sector Cyber Threat Landscape Report, a comprehensive outline of the malicious activity aimed at healthcare in the previous year. Not surprisingly, ransomware was cited by security professionals in the industry as the number one threat of 2024 and the top area of concern coming into 2025 (followed by third-party breaches, supply chain attacks, and zero-day exploits). Some things never change.
However, when it comes to ransomware, they do evolve. Take a look at some of the reasons ransomware maintains its top spot as the primary plague of healthcare organizations as we move into another threat-filled year.
The Patient Extortion Game
Patient extortion is a clever expansion of the ever-present ransomware attack, and the first attack-type highlighted in the report. Threat actors will exfiltrate patient data and, in addition to demanding a ransom payment from the provider, will attempt to hustle individual patients into paying up as well. This happened back in December 2023 in the attack on Integris Health System, as the report cited. After stealing social security numbers, medical visit details, and other bits of protected health information (PHI), attackers contacted victims personally, telling them they could pay $50 to avoid having their information leaked on the dark web.
As noted by Health-ISAC, "This worrying trend may begin to gain traction in 2025 as cybercriminal actors target healthcare even more." As if sick patients don't have enough to worry about.
Large-Scale Ransomware Strikes
When it comes to healthcare, attackers know what's at stake. As stated in a recent House Energy and Commerce Committee Subcommittee on Oversight hearing, "[If] you are a hacker and you ransom a hospital, you are forcing the decision on the hospital: should I pay the ransom and continue to treat patients or should I not and run the risk of not treating patients and... going out of business."
That's why a lot of threat actors opt to go big before going home. The 2025 Health-ISAC drew attention to several of this past year's mega-heists in the healthcare industry.
- The attack on payment processor Change Healthcare by RaaS group BlackCat/ALPHV highlighted the damage caused by a single ransomware outage; it left millions without the ability to pay for the medical services or medications they needed.
- The April ransomware attack on Ascension Healthcare impacted 40 senior care facilities and 140 hospitals, leading to wrongfully routed ambulances, inaccessible electronic health records (EHR), and delayed care. The culprit, BlackBasta, habitually targets healthcare companies and was caught buying compromised credentials to gain initial access.
The Most Active Ransomware Gangs Targeting Healthcare
So, who's behind the lion's share of attacks against the healthcare industry? Even though BlackCat/ALPHV and BlackBasta were responsible for the largest offensives, ransomware group LockBit 3.0 owns the blame for the highest number attacked: 52 healthcare sector victims in all. Here's how the Top 5 shakes out:
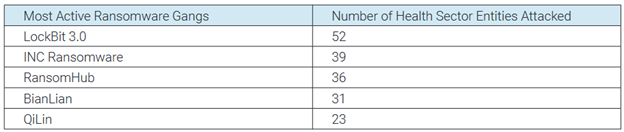
Source: https://health-isac.org/wp-content/uploads/Health-ISAC_2025-Annual-Threat-Report.pdf
LockBit denies any political motivation, and judging by its RaaS affiliate model, it would appear to be a financially motivated ransomware group. The fact that healthcare organizations are in "double jeopardy" as soon as they get hit would explain why LockBit favors the sector; not only do medical organizations have to worry about reputation, lost data, and financial loss (like everyone else), they've also got human lives at stake. This ups the ante and increases chances of a payout – as LockBit likely knows.
While not next-most-prolific in numbers, BianLian is distinguished among the remaining groups by their "history of targeting healthcare organizations." It favors LOLBins (living off-the-land binaries) and is known for a superfast encryptor that can lock down full disk encryption in just minutes.
Nation-State Threats to Healthcare
Now we jump to bigger fish. The report notes several nation-state actors that present as big a threat to the global healthcare industry as the previous ransomware operators do, if not more.
- Russian APT 29 | This Russian state-sponsored threat actor has been using its custom backdoor (WINELOADER) to target healthcare and pharmaceutical companies (among others) across the US and Europe.
- North Korean Remote Workers| As noticed by Health-ISAC members, North Korean threat actors have been gaining entry into healthcare organizations by posing as candidate hopefuls for remote job openings. Using AI to bridge the language gap, they pass the interviews and end up on the payroll of victim healthcare companies. Once inside, they attempt to steal valuable IP, money, and data – which they later use as ransom once they are dismissed.
An Opportunity to Act
Hopefully this report will be more than a shadow of things to come. By tuning in to the other risk factors covered by in Health-ISAC's report - from looming AI to third-party threats to exposed imaging services – healthcare entities can help the ISAC accomplish its overall goal: "[To] prevent, detect, and respond to cybersecurity and physical security events so that Members can focus on improving health and saving lives."
Step up your defenses with the tools that can help you fend off ransomware attacks, prevent third-party compromise, secure your Medical IoT and more. Check out Fortra's Cybersecurity Solutions for Healthcare today.
Editor’s Note: The opinions expressed in this and other guest author articles are solely those of the contributor and do not necessarily reflect those of Fortra.

