
10 years and counting! Such is the milestone of Verizon's 2017 Data Breach Investigations Report (DBIR). Like in years past, the 10th version of Verizon's research initiative highlights new patterns, evolving trends, and interesting findings in the information security field. It does so by synthesizing reports that Verizon received of discovered security incidents and breaches, or incidents with confirmed data disclosure. All these events occurred in 2016 and fit at least one threat action category in the Vocabulary for Event Recording and Incident Sharing framework. Here are some data points that stood out in Verizon's latest report.
Big Picture Stats
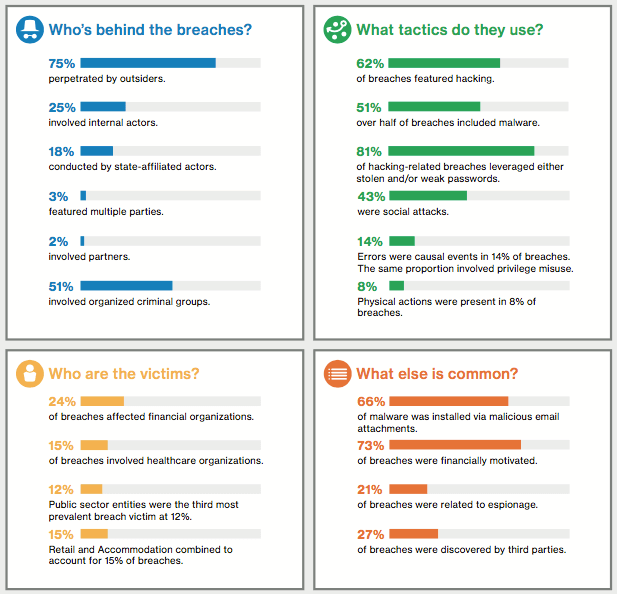
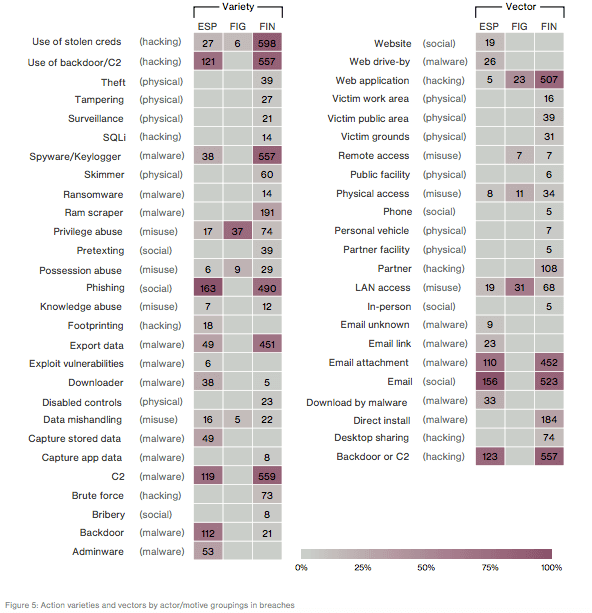
Verizon 2017 DBIR page 3 As you can see, external actors were responsible for three-quarters of the breaches reported to Verizon, whereas internal actors accounted for the other quarter. Some of these data disclosure events involved multiple parties and/or business partners. However, those instances were less frequent at 3 percent and 2 percent, respectively. Overall, Verizon saw a downtick in the percentage of breaches involving external actors and an increase with respect to internal actors. One explanation for this development is the decline of two external attack types in 2016: password-stealing botnets and point-of-sale (POS) intrusions. Nevertheless, breaches driven by internal partners remained relatively constant in absolute terms. It's not surprising to learn that attackers' motivations shape their techniques and targets. For instance, most organized criminal groups or actors with a financial motivation use stolen credentials, a C2, or a keylogger to hack a web application, gain backdoor network access, or plant malware on a victim's computer using an infected email attachment. The same can be said for state (affiliated) groups or actors wishing to commit espionage, although social engineering attacks such as phishing are more common in their category. Taken together, financial motivations and espionage accounted for 93 percent of the breaches analyzed by Verizon.
Verizon 2017 DBIR page 6 The decline of password-stealing botnets and POS intrusions didn't just reduce the percentage of external breaches. It also diminished the number of breaches whose time-to-compromise registered in the seconds or minutes. Their reduction notwithstanding, these events still accounted for 98 percent of all compromises. As for breach disclosure, Verizon observed a correction away from the spike that law enforcement exhibited in its 2016 report. That rise, which was driven by the Dridex botnet, settled down because of decreased card skimming and POS crime. In the meantime, employee notifications remained the most common means of internal discovery. Rates of detection and disclosure through internal audits and third-parties also went up.
Social Attacks
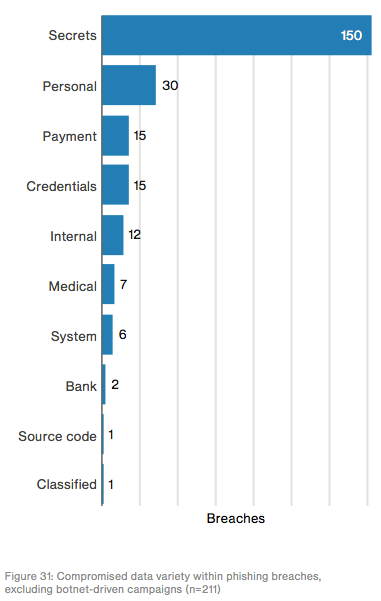
Verizon 2017 DBIR page 33 There were 1,616 social attacks in 2016, approximately half (828) of which with confirmed data disclosure. Those events accounted for 43 percent of all breaches in the 2017 DBIR's dataset. Nearly all the social incidents (99 percent) involved an external actor. In 95 percent of cases, attackers followed up a successful phish with software installation. That's to be expected given most social attackers' motivations and targets. Two-thirds of these actors chase after financial gain, whereas another third is in it for conducting espionage. Both these motivations involve the theft of credentials, personal information, and trade secrets. Across the companies that contributed data to Verizon's report, 7.3 percent of their users fell for a phish. Fifteen percent of that grouping took the bait a second time, with one percent of users clicking on a suspicious link or email attachment more than three times. Acknowledging the persistence of these individuals' behavior, organizations shouldn't just focus on phishing prevention. They should also work on emphasizing detection and encouraging employees to report when they've clicked.
Ransomware
A common payload of phishing attacks is ransomware, which became the fifth most common malware in Verizon's report. Part of this growth in popularity resulted from new ransomware technology and extortion methods. Some ransomware, for instance, lock the Master Boot Record instead of encrypting individual files. Others use techniques like unexpected command-line arguments to avoid detection or rely on exploit kits like RIG to spread them around the web. Others still leverage ransomware-as-a-service (RaaS) platforms to increase their exposure among less tech-savvy criminals, who can then customize a campaign to infect individual systems as well as target vulnerable organizations. In 2016, ransomware grew in the first two quarters. It then dropped slightly in Q3 2016 before falling by 70 percent in the subsequent quarter. This decline is due to the reduction of general ransomware detections and a decrease in the variants for Locky and CryptoWall, two of the top ransomware families in 2016.
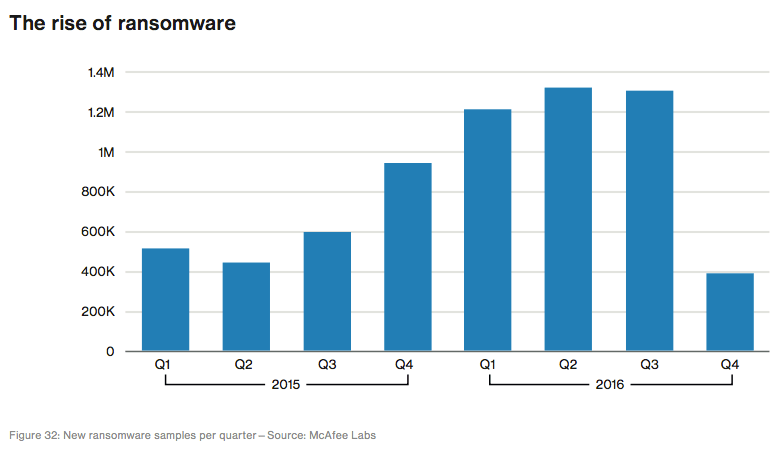
Verizon 2017 DBIR page 35 Companies aren't letting ransomware grow unchecked, however. The security industry is addressing the threat by equipping tools with the ability to enable earlier detection as well as promoting collaboration with law enforcement and threat intelligence sharing. Some of its members are also launching initiatives like No More Ransom that are designed to help ransomware victims regain access to their files without paying the ransom.
Introducing Industries
For the first time in its report series, Verizon introduced an "Industries" section that focuses in on industry-specific findings. Table 1 in the report encapsulates this new effort.
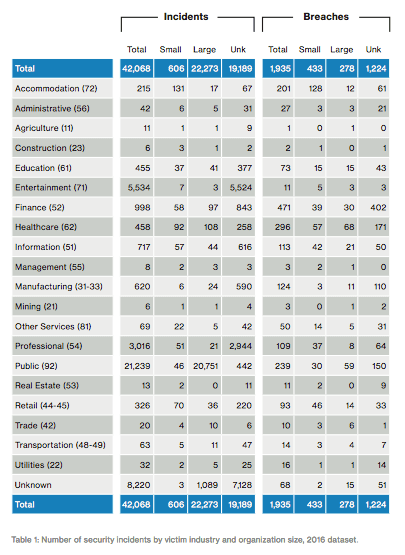
Verizon 2017 DBIR page 9 The researchers at Verizon made a special point of putting their data into context:
"The totals within Table 1 provide information on the sample size for this year's study and are not indicative of one industry being more or less secure than another. It is more of an indication of how well an industry is represented by our data contributors…. Think of Table 1 as opening up the fridge to see just what ingredients you have to cook with, and if you have enough of an industry to 'make the bread rise.'" -- Verizon 2017 DBIR page 9
Taken together, Information, Retail, Finance, and Education all featured high numbers of distributed denial of service (DDoS) attacks. These industries, which rely on a web presence to do business and to communicate with customers, also saw the largest median DDoS attack sizes. But just because other industries didn't see as many or as large of attacks doesn't mean they're secure against DDoS campaigns. Only six contributors sent Verizon vulnerability-scanning data. But that information did reveal some important insights regarding industry patch cycles. For example, Information, Manufacturing, Healthcare, Accommodation, and Retail all fixed between 25 percent and 50 percent of vulnerabilities within the first week, whereas Public, Finance, and Education took a bit longer to patch sometimes a lesser percentage of flaws.
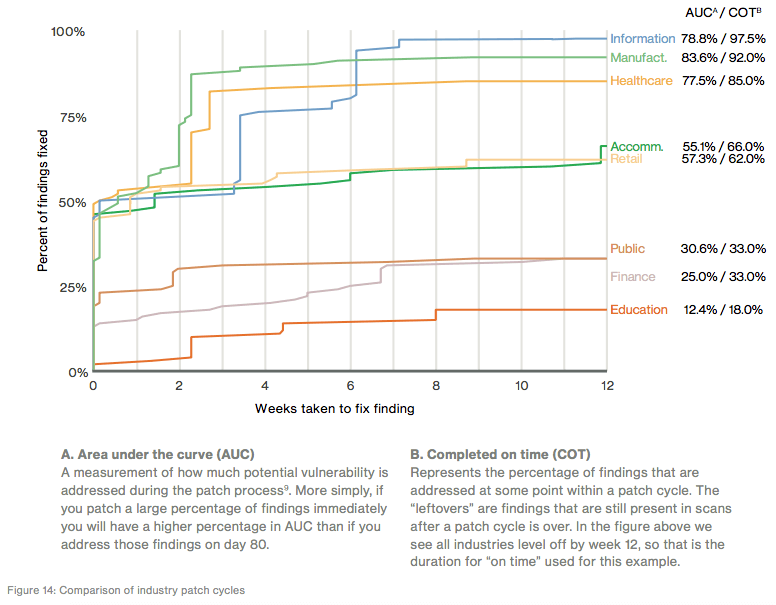
Verizon 2017 DBIR page 13 Verizon shared its thoughts on this observation:
"In your environment, you may have longer or shorter patch cycles that are dependent on the particular vulnerabilities discovered as well as the assets on which the findings are triggered. The vulnerabilities are treated as ‘equals’ in the chart below—organizations will need to factor in threat rates as well as potential impact to establish their own time-to-patch duration to review [completed-on-time] COT." -- Verizon 2017 DBIR page 13
The report then details industry-specific findings. For instance, Accommodation and Food Services primarily encountered financially motivated actors who targeted their POS terminals. Meanwhile, Financial and Insurance experienced lots of Denial of Service attacks.
A Look at Incident Classification Patterns
Verizon finished off its report by returning to its nine incident classification patterns. It dedicated an entire section to these attack types because 88 percent of all the breaches it analyzed fell into one of the nine categories. Here are three categories worth examining. Web Application Attacks The most prevalent category in 2017 DBIR was Web Application Attacks. This pattern saw 6,502 confirmed incidents, 3,583 with secondary motivations and 571 with confirmed data disclosure. Driven by the information gathered by contributors involved in the Dridex botnet takedown, these attacks targeted Finance, Public, and Information companies with social attacks. They then leveraged Dridex malware to steal customers' credentials and dominate their actions. Compared to 2015, there was a higher number of Web Application incidents. But there were fewer breaches this time around. In fact, most were website defacements and used stolen credentials, phishing, and C2/backdoors. Denial of Service Verizon found that Denial of Service attacks dethroned miscellaneous errors, the number one incident classification pattern in the 2016 DBIR. This category saw 11,246 incidents, five with confirmed data disclosure. Entertainment, Professional Services, Public, Information, and Finance saw the most instances of this category, with large organizations the targets in 98 percent of attacks. Across the board, the median size of DoS attacks decreased. Most attacks also didn't last for more than a few days. But the security industry still witnessed some notable attacks driven by IoT botnets, including Mirai's DDoS attack campaign against Dyn on 21 October 2016. POS Intrusions Accommodation and Food Services as well as Retail suffered the greatest from POS intrusions. In total, there were just 212 incidents, 207 with confirmed data disclosure. Many of these attacks involved RAM scraping. However, keylogging/spyware also played a part.
Conclusion
It might be easy for readers of the 2017 DBIR to despair and lament a persistently insecure world. But Verizon hopes this doesn't happen:
"…[W]e are aware that there are numerous success stories out there—it is not all bad news for the good guys. Our hope comes from the fact that we have been able to present these findings to the public for 10 years running. Our hope comes from how we have grown this publication from only one organization to include contributions from 65 sources, providing a solid corpus sample of security incidents and data breaches from which to learn." -- Verizon 2017 DBIR page 2
All readers can use the report to better protect their organization's security. At the same time, more companies should consider contributing data in the coming years to help Verizon present a more comprehensive overview of the digital threat landscape. To join the discussion, download your copy of Verizon's report here.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

