
On 21 August, 2016, the International Olympic Committee (IOC) held the closing ceremony for the 2016 Summer Olympics at the Maracanã Stadium in Rio de Janeiro, Brazil. Hopefully, the celebration symbolized the close of a memorable fortnight during which athletes and spectators alike didn't get hacked and evaded the traps of computer criminals. Hacking attacks aren't new at the Olympics, after all. Apparently, neither are other forms of digital attack. Brazil's test came before the 2016 Games even began, when public-facing web properties and organizations affiliated with the Olympics suffered a sustained distributed denial-of-service attack (DDoS) that lasted for several months. As Arbor Networks' Security Engineering & Response Team (ASERT) explains in a blog post:
"…[S]everal organizations affiliated with the Olympics… [came] under large-scale volumetric DDoS attacks ranging from the tens of gigabits/sec up into the hundreds of gigabits/sec. A large proportion of the attack volume consisted of UDP reflection/amplification attack vectors such as DNS, chargen, ntp, and SSDP, along with direct UDP packet-flooding, SYN-flooding, and application-layer attacks targeting Web and DNS services."
A DDoS-for-hire service known as LizardStresser staged most of the pre-Olympic attacks. The Internet of Things (IoT) botnet, which is not the first of its kind, is the same booter that Lizard Squad created shortly after its Christmas 2014 takedown of Xbox Live and PlayStation Network. Perhaps in response to that notoriety, someone hacked LizardStresser just a few weeks after its 2015 debut and leaked the unencrypted login credentials of more than 14,000 prospective users. Once the Olympics got under way, LizardStresser along with a few other botnets ramped up their attack against organizations affiliated with the Olympics. The DDoS campaign launched attack traffic using the lesser-known IP protocol Generic Routing Encapsulation (GRE).
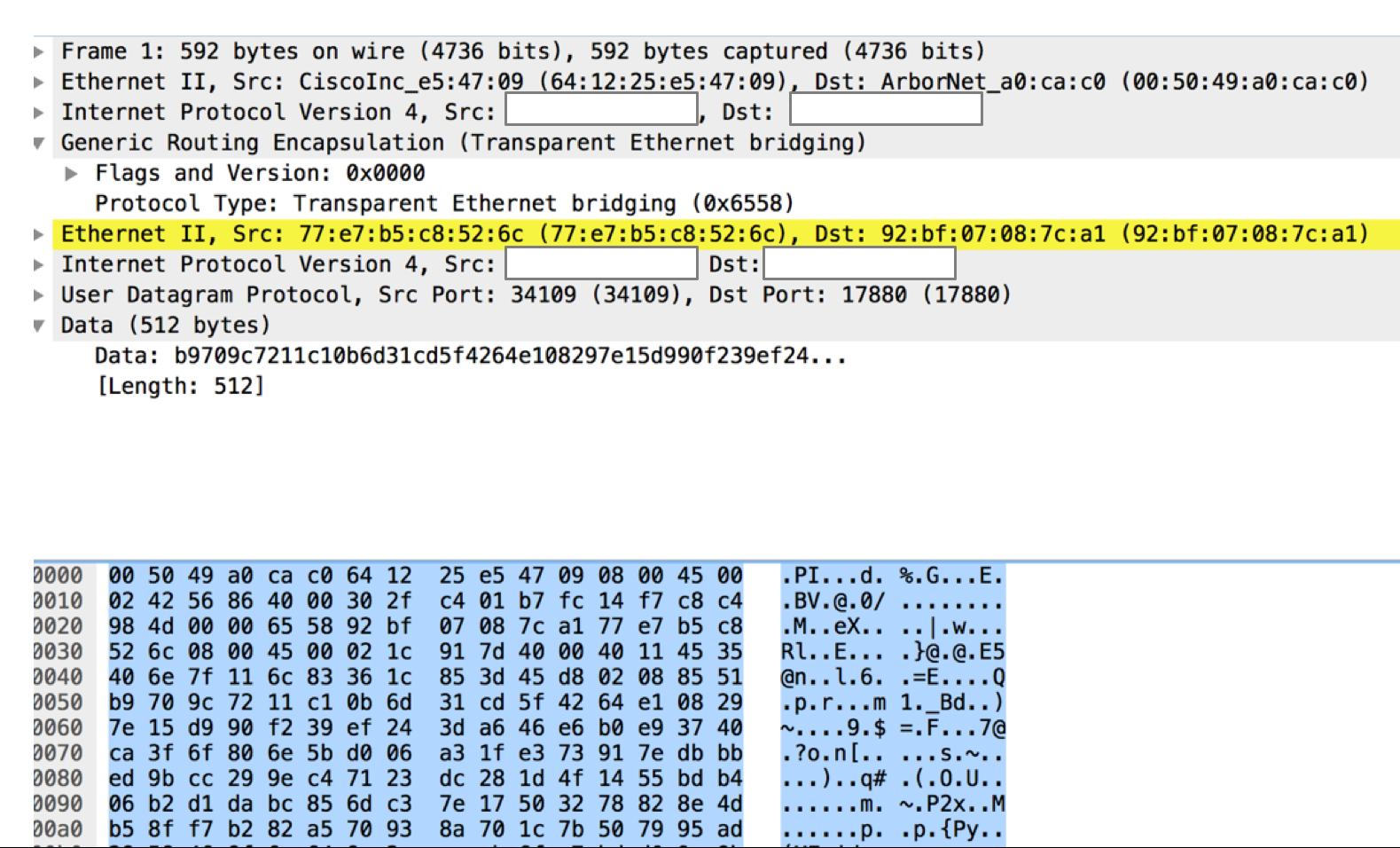
Example crafted GRE DDoS attack packet (Source: Arbor Networks) It also sent out high-volume packet-floods destined for UDP/179. ASERT believes the attackers employed that technique to partially conceal their campaign:
"As most (not all) UDP reflection/amplification attacks tend to target UDP/80 or UDP/443 in order to confuse defenders who might not notice that the attackers are using UDP instead of TCP (TCP/80 is typically used for non-encrypted Web servers, and TCP/443 for SSL-/TLS-encrypted Web servers), we believe the attackers were attempting to masquerade an attack on the BGP routing protocol used to weave Internet-connected networks together."
But that didn't fool Brazil and other information security personnel responsible for protecting the Rio Olympics’ online presence. They did their due diligence and worked to understand their endpoint devices so that they could implement DDoS countermeasures throughout the Games' network. With those key mitigation services in place, Brazil and the International Olympics Committee (IOC) kept the systems up and running despite peak attack traffic registering in at a whopping 540 Gb/sec.
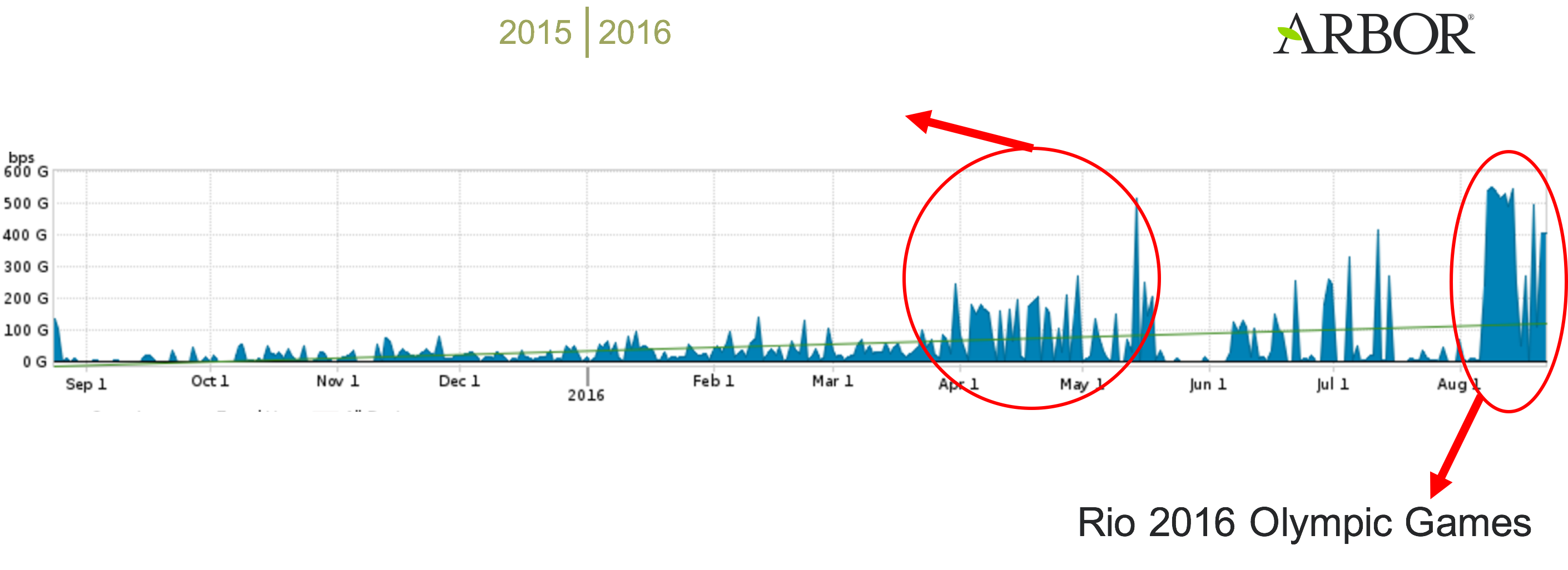
Source: Arbor Networks As a result, millions of viewers from around the world were able to watch the Games in real-time. Booter services like LizardStresser open the world of DDoS campaigns to script kiddies, amateur attackers, and other would-be criminals who make up for low levels of technical expertise with cash. That means DDoS attacks are unlikely to go away anytime soon. In fact, Arbor has found they are steadily increasing in size, sophistication, and frequency each year. Given the persistent threat of DDoS attacks, organizations should develop a mitigation strategy before they find themselves targeted by campaign. For tips on how to protect your organization's network against a DDoS campaign, please click here.
Meet Fortra™ Your Cybersecurity Ally™
Fortra is creating a simpler, stronger, and more straightforward future for cybersecurity by offering a portfolio of integrated and scalable solutions. Learn more about how Fortra’s portfolio of solutions can benefit your business.

